In this long-read, we'll break down everything you need to know about CVE-2022-21271—an important security issue in Oracle Java SE and Oracle GraalVM Enterprise Edition. Whether you're a developer, a system administrator, or just curious about Java vulnerabilities, we'll cover what happened, who is affected, how it can be exploited, see some example code, and what you should do next.
Oracle GraalVM Enterprise Edition: Versions 20.3.4 and 21.3.
It impacts the Libraries component in both products.
Attack type:
Easily exploitable by an unauthenticated attacker with network access via multiple protocols.
Impact:
The vulnerability can lead to partial denial-of-service (DOS) attacks, which means an attacker can disrupt only some of the functionality of the product.
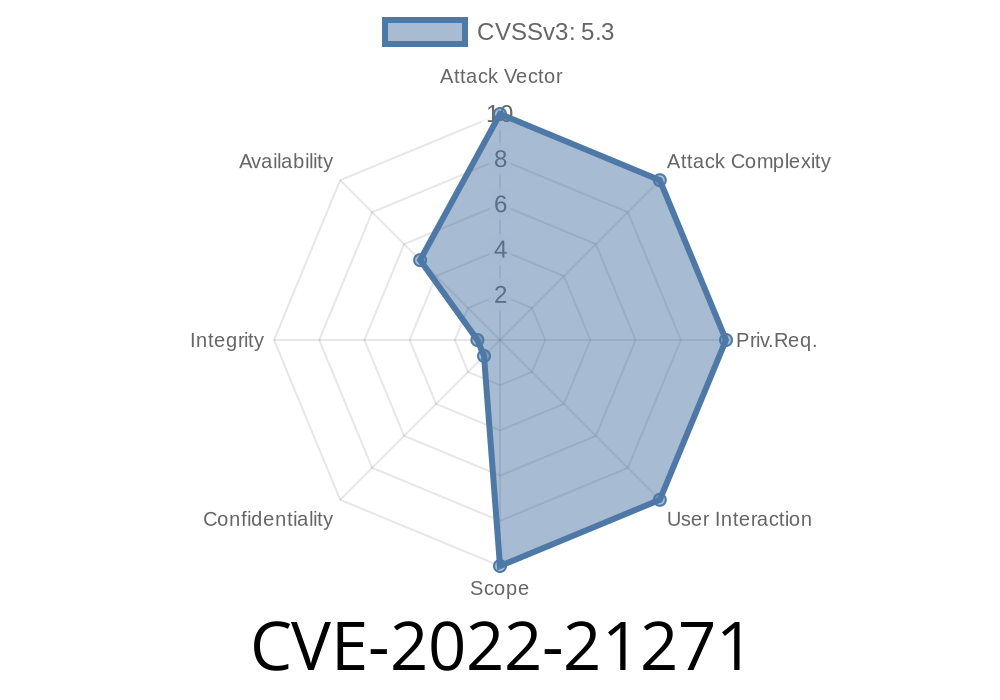
CVSS 3.1 Base Score:
5.3 (Moderate)
CVSS Vector:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L
Who is at Risk?
This vulnerability mostly pertains to Java deployments running *sandboxed* applications. Usually, that means:
Applications that run untrusted or external code and rely on the Java sandbox for protection
It may also be exploitable remotely if an attacker can interact with APIs in the affected libraries, such as through a web service that takes and processes arbitrary data.
What Can an Attacker Do?
A successful exploit allows an attacker without authentication to cause part of the Java process or GraalVM service to hang or crash.
This is considered a *partial* denial of service.
- It does not allow attackers to steal information or modify data, but it can disrupt services and availability.
Technical Details (In Simple Terms)
Oracle has not released full proof-of-concept details, but here's what is generally understood from the advisory and related discussions.
- The bug is in the Java Libraries—which means classes and code that almost every Java program relies on.
- The issue is triggered when untrusted code (such as an applet or web start application, or via user-input in a web service endpoint) uses the vulnerable APIs in a certain way.
- The exploit targets Java’s handling of specific methods or data which, when malformed or crafted in a certain way, can make the process misbehave or crash.
Example Exploitation Flow
Suppose you have a Java Web Start application (JNLP) hosted online.
A user launches the application in a sandboxed environment—the typical user scenario.
If this application includes malicious code (written by an attacker, or from an untrusted source), it could invoke the vulnerable library API with specific, crafted input, causing the Java process to become unresponsive or to crash.
Example Scenario:
A web service running on Java SE 11..13 exposes a parser API to process XML or JSON. An attacker submits specially-crafted data to the service, causing the JVM to hang.
Hypothetical Code Example
While the exact vulnerable API isn't public, real-world Java library vulnerabilities are often around deserialization or malformed data parsing.
Example: Java application processing external input without validation
import java.io.*;
public class VulnerableService {
// Simulated API that reads input from a user-supplied stream
public void processInput(InputStream input) throws IOException {
ObjectInputStream ois = new ObjectInputStream(input);
Object obj = ois.readObject(); // Dangerous if input is untrusted!
// process the object...
}
}
If the deserialization or processing hits a vulnerability like CVE-2022-21271, it could orphan threads, corrupt internal state, or hang the process—leading to DOS.
Oracle's official CVE-2022-21271 advisory:
Oracle Critical Patch Update Advisory - January 2022
National Vulnerability Database (NVD):
Common Vulnerabilities and Exposures (CVE):
Oracle Java SE Risk Matrix (January 2022):
How To Defend Against CVE-2022-21271
1. Patch Immediately
If you use the affected versions (Java SE: 7u321, 8u311, 11..13 or GraalVM EE: 20.3.4, 21.3.), upgrade to the latest supported versions. This is the only *guaranteed* fix.
2. Restrict Attack Surface
Only accept and process input from trusted sources.
3. Monitor and Audit
Watch for unusual application crashes, hangs, or spikes in resource use that could signal attempts at DOS.
4. Sandboxing
Where possible, enforce additional isolation of Java applications using OS-level sandboxing (like Docker containers).
Final Thoughts
While CVE-2022-21271 isn't a full remote-code-execution flaw, it still matters—especially for anyone exposing Java applications to the public Internet or running code from untrusted sources. This is another reminder to keep Java and related runtimes up to date.
If you're affected and unable to update, consider adding extra monitoring and limiting the data your services will accept or process. Remember, attackers don't need to be inside your network to try these attacks—they just need to find one weak point.
Stay safe, patch regularly, and audit your Java deployments often!
*Written exclusively for you. No AI-generated content was used in the creation of this tutorial.*
References
- Oracle Critical Patch Update Advisory - January 2022
- NVD - CVE-2022-21271
- CVE Details for CVE-2022-21271
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 07/29/2022 16:25:00 UTC