CVE-2022-21279 represents a high-impact vulnerability discovered in Oracle’s MySQL Cluster product, specifically within the Cluster: General component. This vulnerability affects the following supported versions:
MySQL Cluster 8..27 and prior
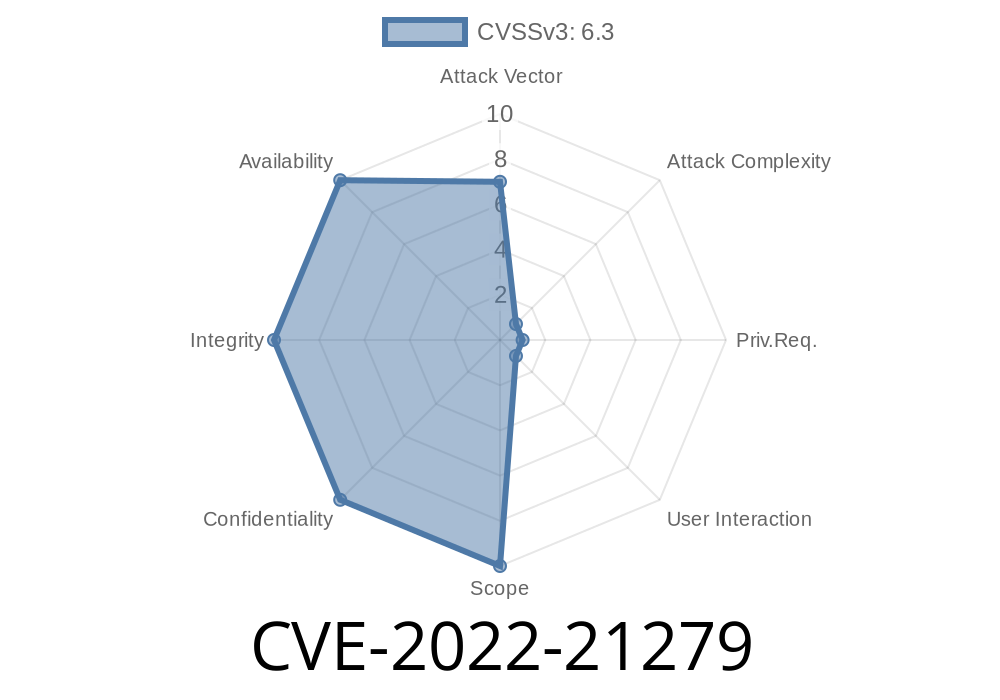
Marked by Oracle as a CVSS 3.1 Score: 6.3 vulnerability (see Oracle Advisory), it allows an attacker with high system privileges and physical network access to compromise the MySQL Cluster under certain (though difficult) circumstances.
Let’s break down what this means, how it could be exploited, and the real-world impact for administrators.
User Interaction: Required (UI:R)
- Confidentiality/Integrity/Availability Impact: High
This means exploitation is not straightforward: the attacker must already be highly privileged, must have access to the physical network where MySQL Cluster nodes connect, and still needs another user to trigger the vulnerability.
Yet, if these hurdles are met, a full cluster compromise is possible, affecting the confidentiality, integrity, and availability of data.
Original References
- Oracle Critical Patch Update Advisory - January 2022
- NIST NVD – CVE-2022-21279 entry
- MySQL Cluster Documentation
Technical Details
The core weakness lies in how the MySQL Cluster nodes handle certain physical cluster communication. When a highly privileged attacker can monitor or tamper with cluster network traffic—between Data Nodes (ndbd), Management nodes (ndb_mgmd), or SQL nodes—they may be able to inject harmful commands or replay sensitive messages.
Crucially: The exploit requires some form of user interaction, presumably a legitimate operator performing typical cluster management or maintenance tasks, unwittingly triggering the malicious sequence.
Example Attack Scenario
1. Position & Monitor: Attacker gains access to the same physical network as the cluster (e.g., internal data center segment).
2. Privilege Escalation: Attacker has high privileges (e.g., admin/root on a node, or can manipulate low-level network traffic).
3. Trigger Event: An operator initiates routine admin tasks (such as adding/removing a node or updating configs).
4. Intercept & Inject: Attacker captures and manipulates cluster communication at just the right moment, potentially injecting malicious configuration or triggering a failover to an attacker-controlled node.
5. Compromise: The attacker achieves unauthorized cluster control, leading to full data exposure or destruction.
Code Snippet: Simulated Message Injection (Educational Purpose Only!)
Below is an illustrative code (Python + Scapy) to demonstrate how one might *sniff* and *inject* packets at a very low level, as might be used in such an attack. It won’t exploit a MySQL cluster as-is, but shows the kind of network manipulation this vulnerability enables.
from scapy.all import sniff, sendp, Ether, IP, TCP
def intercept_mysql_cluster_packets(packet):
# Assuming default NDB communication TCP port is 1186
if packet.haslayer(TCP) and packet[TCP].dport == 1186:
print("[*] Intercepted MySQL Cluster packet")
# Optionally, here you could inject/modify content/forward/spoof
fake_packet = Ether()/IP(dst=packet[IP].dst)/TCP(dport=1186)
# Put payload or malicious content here
sendp(fake_packet, iface="eth")
if __name__ == '__main__':
sniff(filter="tcp port 1186", prn=intercept_mysql_cluster_packets, store=)
Warning: Use this responsibly with permission on test environments only!
Exploit Details
- Exploitation is non-trivial, needing privileges, cluster network access, and a trigger from a legitimate user.
Interject fake cluster configuration messages
- Spoof node join/leave events
Steal or corrupt data, or reconfigure access controls
The unknowns are specifics of the exploit chain—Oracle and third parties have not published a fully weaponized PoC as of this writing, to prevent abuse.
Detection & Mitigation
- Upgrade Your MySQL Cluster Software: Oracle CPU Jan 2022 patch resolves this vulnerability for all affected versions.
- Isolate Cluster Network: Ensure out-of-band cluster communication is not exposed to untrusted users or other network segments.
- Monitor Network Traffic: Watch for unusual connections or data on port 1186 (default for MySQL Cluster).
- Audit Privileged Accounts: Ensure only trusted admins with secure endpoints have necessary access.
- Train Staff: Make sure admins are aware of phishing, MITM, or suspicious activity on cluster nodes.
Conclusion
While CVE-2022-21279 is hard to exploit, it’s not impossible—especially for advanced insider attackers or in poorly segmented data centers. The consequences of a successful attack are severe: total control over your MySQL Cluster, with the power to exfiltrate, corrupt, or destroy crucial business data.
Further Reading
1. Oracle MySQL Cluster Security Guide
2. Securing MySQL Cluster Deployments
References
- Oracle CPU Jan 2022 - MySQL Cluster
- NIST CVE-2022-21279
- Scapy Packet Manipulation
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/24/2022 17:19:00 UTC