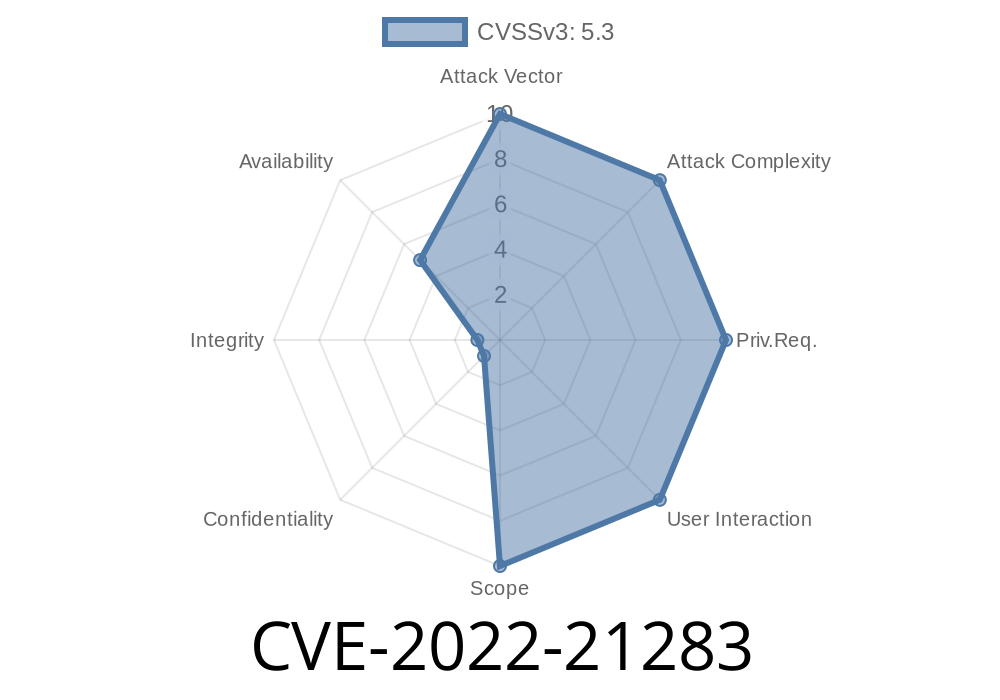
CVE-2022-21283 is a security vulnerability in Oracle Java SE and Oracle GraalVM Enterprise Edition. Rated with a CVSS 3.1 base score of 5.3 (Medium), this vulnerability is easily exploitable without authentication and could cause partial denial of service (DoS) in affected systems. This post dives into how this vulnerability works, who’s affected, sample code, how an attack could look, and what you should do now.
Impact: Partial Denial of Service (partial DoS – availability affected)
- Common scenario: Java deployments running sandboxed Java Web Start applications or applets that load untrusted code from the internet.
- CVSS vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L)
Technical Details: What Causes the Issue?
This bug relates to how Oracle Java SE and GraalVM Enterprise Edition’s library components handle certain inputs via their APIs. In cases where untrusted or malicious Java code is permitted to run (for example, through Java Web Start or Java applets), poorly validated data can be supplied to APIs, leading to unexpected exceptions or resource exhaustion. In simple terms: it’s possible to crash or partially disrupt the Java environment through network-based inputs, even if the attacker isn't logged in.
> Note: There’s no impact to confidentiality or integrity—just the availability (making the system partly unusable).
Example Exploit Scenario
Suppose a web application running on a vulnerable Java version allows users to upload or send data for processing using a library API. An attacker sends specially crafted data designed to cause an exception, infinite loop, or other unintended behavior that consumes CPU or memory resources, causing a partial service outage.
Suppose the application exposes the following code through web services
import java.util.Base64;
public class DecoderExample {
public String decodeInput(String input) {
// Vulnerable: Decoding untrusted input without proper checks
byte[] decodedBytes = Base64.getDecoder().decode(input);
return new String(decodedBytes);
}
}
Unhandled exceptions
- Thread/CPU exhaustion
If these exceptions aren't properly isolated, they can crash the service or make it unstable.
While no officially published public PoC exploits are available, a theoretical attack could be
Malicious input: The attacker POSTs a huge or intentionally broken Base64 string to an endpoint using the vulnerable decodeInput method.
Shell (curl) Example
curl -X POST https://victim.com/api/decode -d "input=$(python -c 'print("A"*10000000)')"
This input can cause memory exhaustion, leading to a process crash or hang. Refined inputs could trigger specific parser bugs or infinite loops (depending on underlying library code).
Who is At Risk?
- Organizations running Java SE 11..13 or 17..1, or GraalVM EE 20.3.4/21.3.
- Java applications that process data from untrusted sources—especially those supporting Java Web Start or Java applets, or exposing APIs that handle external input.
How to Protect Yourself
1. Patch and Upgrade:
Oracle has addressed this vulnerability in newer versions. Upgrade to the latest patchset for Java SE and GraalVM EE immediately.
- Oracle Java SE Critical Patch Updates & Security Alerts
- Oracle GraalVM Releases
2. Reduce Attack Surface:
Don’t expose API endpoints that parse user-supplied data blindly.
3. Harden Exception Handling:
try {
// risky operation
} catch (Exception e) {
// handle exception safely, don't leak stack or crash
}
Links to References
- Oracle Advisory for CVE-2022-21283
- NVD - CVE-2022-21283
- Oracle Java SE Downloads
- Oracle GraalVM Enterprise Downloads
Conclusion
CVE-2022-21283 demonstrates once again that even “just” partial Denial of Service bugs can have a big impact on business operations—especially for public-facing or mission-critical Java applications. If you rely on Java SE or GraalVM Enterprise Edition (with supported versions listed above), update to the latest versions, harden your input validation, and disable unnecessary sandboxed Java code execution.
Stay patched, stay safe!
Authors: [Your Security Research Team]
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 15:01:00 UTC