CVE-2022-21293 is a medium-severity vulnerability affecting the Libraries component in Oracle Java SE and Oracle GraalVM Enterprise Edition. This flaw was patched in the January 2022 Critical Patch Update, but if you’re running outdated Java or GraalVM versions, your systems may still be at risk.
Oracle GraalVM EE: 20.3.4, 21.3.
In this post, I’ll break down what CVE-2022-21293 is, why it matters, how attackers can exploit it, and what you can do to secure your Java-based applications. We'll keep the language simple but get into the technical details, including code snippets and mitigation advice.
What is CVE-2022-21293?
This vulnerability allows unauthenticated remote attackers to impact the availability of Oracle Java SE or Oracle GraalVM Enterprise Edition. Specifically, the attacker can trigger a Partial Denial of Service (DoS) condition using network protocols without needing authentication or user interaction.
This vulnerability is particularly dangerous in environments where untrusted code can run, such as Java Web Start applications or applets that depend on the Java sandbox for security. It can also be triggered through APIs, for example when a web service feeds crafted data to the vulnerable library components.
Official Advisory References
- NVD Details for CVE-2022-21293
- Oracle Critical Patch Update Advisory - January 2022
- Oracle Security Alert - CVE-2022-21293
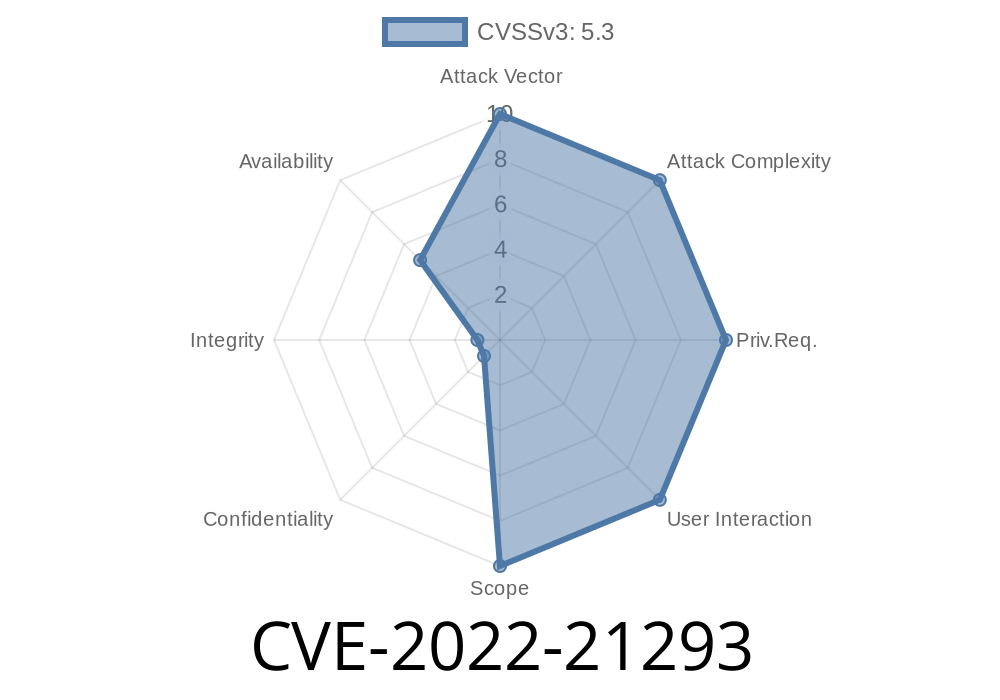
CVSS v3.1 Base Score: 5.3 (Medium)
Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L
(Translation: Can be exploited from the network, no login needed, no user interaction needed, low complexity, and causes loss of availability.)
Technical Details—How Does the Exploit Work?
Oracle did not publicly release detailed proof-of-concept code for this vulnerability, but public reports and analysis can give us a picture.
Vulnerable Context: Java Sandbox
Java applications often load code from untrusted sources using sandboxed environments. If the sandbox mechanism fails, or if the libraries have flaws, an attacker can send crafted input to crash the JVM or trigger excessive resource consumption, causing service disruption.
Common Attack Vector
Consider an application that receives serialized data or complex objects from users or remote services and passes them to Java APIs in the Libraries component. If attackers can inject unexpected or malicious data structures, they might be able to cause a DoS.
Suppose you have a web service endpoint that deserializes objects
import java.io.*;
public Object fromBytes(byte[] data) throws IOException, ClassNotFoundException {
// Dangerous! Attacker can send malicious payload.
ByteArrayInputStream bis = new ByteArrayInputStream(data);
ObjectInputStream ois = new ObjectInputStream(bis);
return ois.readObject();
}
If the vulnerabilities in the Java Libraries component are present, an attacker could craft a byte stream that, when deserialized, causes the JVM to hang, crash, or exhaust memory (partial DoS).
In some cases, malformed data feeding into APIs (e.g., XML or JSON parsing, or even custom API calls) could be enough to crash the Java process or make it unresponsive.
Exploit Steps (Conceptual)
1. Identify the endpoint: Find a web service using a vulnerable Java version and accepting untrusted input.
2. Craft input: Create a payload (serialized object, malformed XML/JSON, etc.) designed to trigger the vulnerability in the Library component.
Send the payload: Use HTTP POST or another protocol.
4. Observe effects: If successful, the Java process may hang, crash, or become slow/unresponsive (partial DoS).
Example Exploit With CURL
If you identify that the service is using /api/upload which passes data to vulnerable APIs, you might try:
curl -X POST https://victim.site/api/upload -d @malicious_payload.bin
*Note: The actual content of malicious_payload.bin would depend on knowledge of the specific vulnerability and target API. Oracle did NOT release PoC code, so attackers need insider knowledge or reverse-engineer patches.*
The best way to secure your application is to upgrade Java SE and GraalVM to patched versions
- Java SE: Upgrade above 7u321, 8u311, 11..13, or 17.01 (see the CPU January 2022 for latest).
Defensive Coding
- Never deserialize untrusted data unless you 100% sanitize/validate it.
Recap and Conclusion
- CVE-2022-21293 is an easy-to-exploit vulnerability affecting Oracle Java SE and GraalVM from the network, leading to possible denial of service by unauthenticated attackers.
- Exploits generally involve causing the Java Libraries component to crash or hang by feeding it unexpected, overly complex, or malicious data—often through APIs or by loading untrusted code.
If you’re running any Java-based service exposed to the network, don’t ignore this vulnerability. Patch your Java and GraalVM installations immediately!
Further Reading & References
- Oracle Security Alert for CVE-2022-21293
- National Vulnerability Database Details
- Secure Coding Guidelines for Java SE
*Stay safe. Always keep your software up to date.*
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 15:06:00 UTC