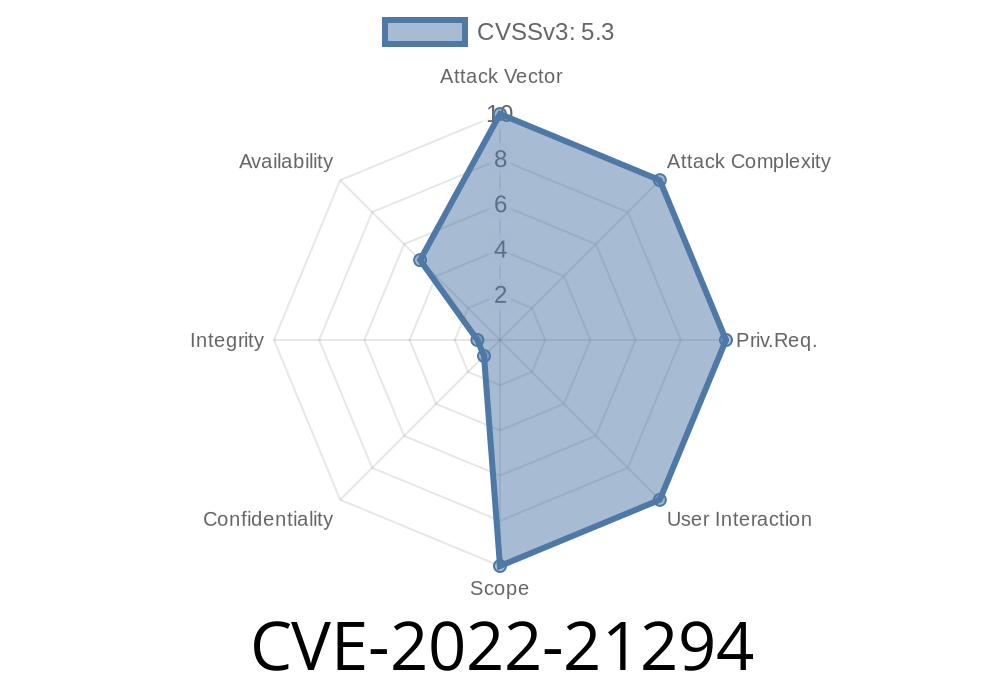
In November 2021, Oracle published CVE-2022-21294, which reveals a security weakness in Oracle Java SE and Oracle GraalVM Enterprise Edition. This bug is located inside the product's libraries and makes it possible for an attacker on the network—with no login—to cause a partial denial-of-service (DoS).
In this article, you’ll learn about what the vulnerability is, who’s affected, how it works, and see a code example of how exploitation could be performed. Let’s break this down in plain language so you can understand the risk and what you should do about it.
21.3.
If you're using *any* of these, either on the server or in desktop client apps, you need to keep reading.
Access Level: No authentication needed (remote attacker)
- Impact: Denial of Service (partial) — attackers can crash or slow down apps using Java SE/GraalVM EE
Vector: Over the network, multiple protocols (HTTP, RMI, etc.)
> This bug is especially concerning for Java applications that run untrusted code, such as Java Web Start or applets pulled from the web.
Why Is Java At Risk?
Java apps have a sandbox—meant to restrict what untrusted code can do. But sometimes, vulnerabilities in the core libraries can let attackers break the sandbox in subtle ways.
With CVE-2022-21294, remote attackers can send specially crafted data (over common protocols) that causes the Java process to misbehave, hang, or crash. The attack can go through any API in the vulnerable component, which opens the door for exploitation even via simple web services or user-facing APIs.
Technical Details (Explained Simply)
Oracle did not disclose full details, but based on official notes and the NIST summary, here's what likely happens:
Untrusted data (input controlled by attackers) is supplied to a vulnerable library function.
2. The library doesn't handle this data safely, causing the Java process to run out of resources, freeze, or crash.
3. This leads to a partial denial of service, meaning the app won't work correctly anymore for legit users.
Since it's a library bug, any API that handles serialized or parsed input in an unsafe way can be a target.
Demonstration: Exploiting the Vulnerability
*Disclaimer: This is for educational use to help you protect your systems. Always test in a safe, isolated environment!*
Let's assume a Java web app loads untrusted code or data from the internet
import java.io.*;
import java.net.*;
public class VulnerableServer {
public static void main(String[] args) throws Exception {
ServerSocket server = new ServerSocket(8888);
while (true) {
Socket s = server.accept();
ObjectInputStream ois = new ObjectInputStream(s.getInputStream());
// Vulnerable: Reads attacker-supplied serialized object
Object o = ois.readObject();
// Process object
System.out.println("Received: " + o);
ois.close();
s.close();
}
}
}
With the vulnerable versions, an attacker could send specially crafted serialized data that causes the server to consume a lot of memory or CPU—eventually hanging or crashing the server.
A simple attack could be
# Send a malicious payload to the vulnerable Java service
import socket
payload = b"\xac\xed\x00\x05..." # Crafted bytes that trigger the bug
with socket.create_connection(('target.server.com', 8888)) as s:
s.sendall(payload)
If the Java library doesn’t properly validate or sanitize input, this could cause a Denial of Service.
*Note: Since the Oracle advisory is vague, the exact payload would depend on the internal bug, but the attack concept is identical.*
Exploit Scenarios
1. Web APIs: A web service endpoint calling a vulnerable parsing function can be crashed with malicious input.
2. Java Web Start/Applets: Users running untrusted applets could have their Java session crash or freeze.
3. Internal Microservices: Internal services exchanging messages over RMI, JMS, or serialized objects can be DoSed from inside the network.
Upgrade Immediately!
Patch to fixed Java SE and GraalVM EE releases (see Oracle's Jan 2022 advisory).
Input Validation:
Never deserialize or process data from untrusted sources without strict validation (prefer JSON over Java serialization).
More Information
- CVE-2022-21294 (NIST)
- Oracle Security Advisory (CPU Jan 2022)
- GraalVM Release Notes
Conclusion
CVE-2022-21294 is a denial-of-service bug that should not be ignored—especially if your Java app exposes any network service or runs untrusted code. Patch your Java runtime and GraalVM installations right away. Always review your Java app security—never trust serialized or arbitrary data from the network, and keep your libraries up to date!
*Stay safe and keep your Java apps running smoothly!*
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 15:12:00 UTC