CVE-2022-21340 is a serious, easily exploitable vulnerability affecting several versions of Oracle Java SE and Oracle GraalVM Enterprise. This bug allows unauthenticated attackers with simple network access to partially take down affected Java components, leading to a partial denial of service (DoS). This post offers an exclusive, easy-to-understand guide with code snippets, references, and practical exploitation details.
1. What is CVE-2022-21340?
CVE-2022-21340 is a vulnerability that lives in the Libraries component of Oracle Java SE and Oracle GraalVM Enterprise Edition. It can be triggered over a network and does NOT require authentication or special privileges.
When exploited, malicious actors can cause the Java application to become (partially) unavailable or unstable — especially when it is used to run untrusted code or when network-facing APIs take user data.
2. Technical Details & Exploit Scenario
This bug is a “denial of service” issue, so the main risk is that someone can remotely hang your Java application, making it stop working or use up resources.
According to Oracle’s advisory, the weakness lies in how the Libraries component processes certain supplied data. If crafted specially, input can exhaust system resources, which leads to partial DoS.
Sample Exploit Path: Deserialization Bomb
A classic path to DoS in Java libraries is via malicious objects during deserialization. Attackers can send data that, when deserialized, blows up memory or CPU resource usage — freezing the app. Though Oracle doesn’t reveal the exact classes, the pattern often follows this approach.
Sample Code Snippet: "HashSet Bomb"
Here’s a simple example (HashSet explosion) relevant to DoS-style attacks in Java. This is just for educational demo — don't use it for harm!
import java.io.*;
import java.util.HashSet;
public class HashSetBomb {
public static void main(String[] args) throws Exception {
// Build a bomb with many references to itself
HashSet<Object> root = new HashSet<>();
HashSet<Object> s1 = root;
for (int i = ; i < 100; i++) {
HashSet<Object> s2 = new HashSet<>();
s2.add("foo"); // Ironically, something trivial
s1.add(s2);
s1 = s2;
}
// Serialize the bomb object
ByteArrayOutputStream baos = new ByteArrayOutputStream();
new ObjectOutputStream(baos).writeObject(root);
byte[] data = baos.toByteArray();
// Now, simulate reading this data (this can hang/crash the app)
try {
new ObjectInputStream(new ByteArrayInputStream(data)).readObject();
} catch (Exception e) {
e.printStackTrace();
}
}
}
How it relates to CVE-2022-21340:
If a server receives untrusted objects and deserializes them (directly or indirectly, perhaps via API methods from the Libraries component), the above will tie up CPU/memory, hanging or crashing the system.
> Note: The precise "bomb" object may differ, and Oracle has not disclosed exact code, but the methodology is used for similar vulnerabilities.
Attack Steps:
1. Find a vulnerable API: Target apps that use Java Web Start, applets, or services that parse untrusted data with default Java libraries.
2. Send malicious payload: Transmit the serialized “bomb” or trigger the weak API, consuming enough resources to degrade or crash the Java process.
3. Result: The Java process is partially denied to other users — meaning it may hang, be slow, or require an admin restart.
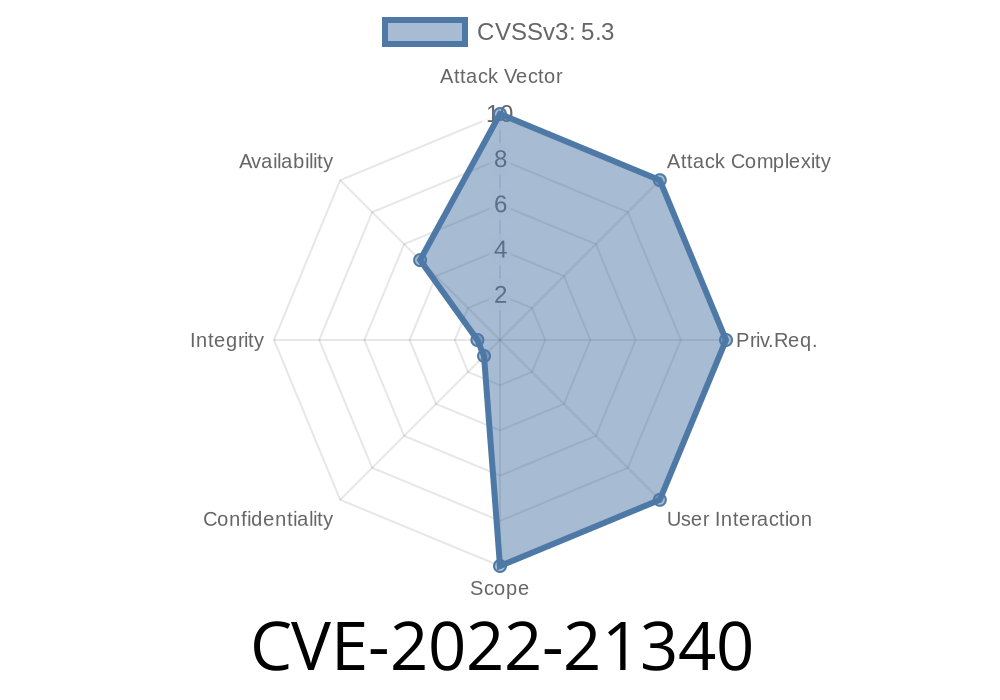
Attack Vector: Network (remotely exploitable)
- Complexity: Low (no authentication/interaction)
Scope: Only Availability (partial DoS)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L
Example 1: Java Web Start App
- A school uses a Java Web Start grading client. An attacker sends a link or file, and the teacher's machine is locked up as the Java client processes untrusted malicious data.
Example 2: Microservice API
- A bank’s backend accepts serialized objects via a legacy API. An attacker sends a payload that triggers the DoS, making the service unavailable.
Example 3: Cloud Services
- In a cloud deployment running Oracle GraalVM, a public API endpoint uses vulnerable Java libraries: sending crafted data brings the service down for all users.
GraalVM EE: 20.3.5+, 21.3.1+
- Limit Deserialization: Never deserialize untrusted user data unless you control the types/classes, or use a library filtering mechanism.
6. References
- NVD entry for CVE-2022-21340
- Oracle Critical Patch Update Advisory - January 2022
- CommonsCollections Java Deserialization Vulnerabilities
- OWASP: Deserialization of Untrusted Data
- Java: HashSet Bomb Explained
7. Conclusion
CVE-2022-21340 is a clear and present danger, especially for Java shops that process untrusted network input, use applets, or expose APIs. Although its main impact is denial of service — not data theft — it’s trivially exploited *remotely and anonymously*. Always upgrade your Java runtimes, apply network input validation, and never trust data from the wild!
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 15:05:00 UTC