Date Discovered: January 2022
Affected Products:
Oracle GraalVM Enterprise Edition: 20.3.4, 21.3.
Component: Java 2D
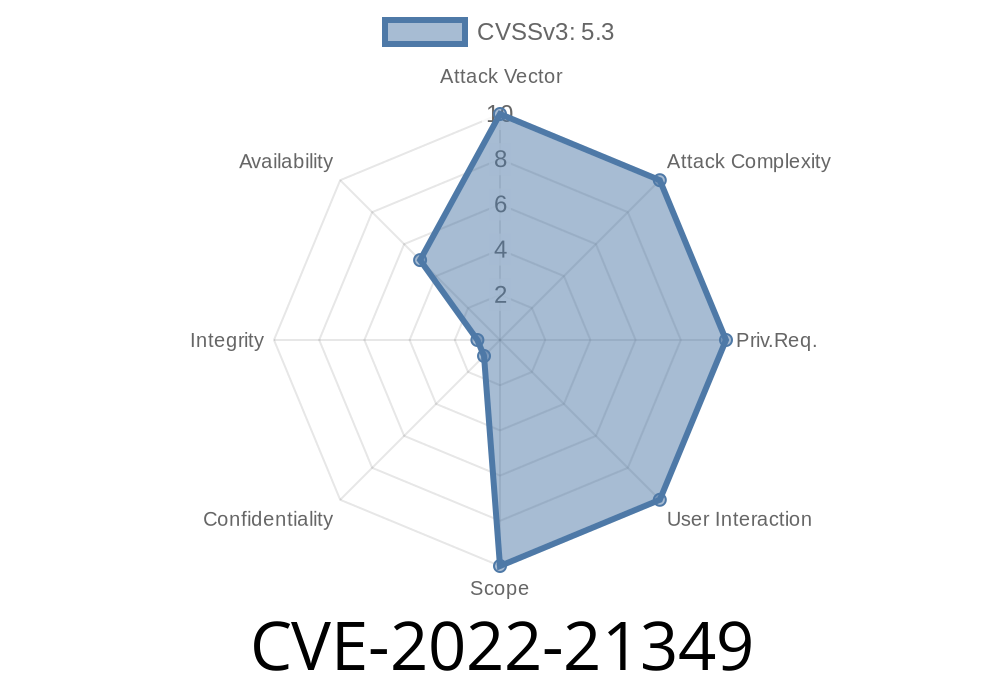
CVSS 3.1 Base Score: 5.3 (Availability impacts)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L
What is CVE-2022-21349?
CVE-2022-21349 is a security bug found in the 2D component of Oracle Java SE and Oracle GraalVM Enterprise Edition. This bug makes it possible for someone from outside your network (without needing any login or permissions) to send special data that forces Java to crash or hang, causing what's called a "Partial Denial of Service" (DoS). It’s not a full system shutdown, but certain Java functions or processes can become unresponsive.
This vulnerability is especially risky for systems that run untrusted code, like Java Web Start apps and Java applets loaded from the Internet, which many businesses and legacy systems still use. It also matters if your Java application exposes APIs that handle image or graphical data remotely.
Anyone running the listed vulnerable Java SE or GraalVM versions.
- Apps or services that accept image data or use the Java 2D API and process untrusted input—like graphical apps, online editors, or web services letting users upload/modify images.
- Java apps deployed via web technologies (Web Start, applets) which download and execute code from remote sources.
How Does the Vulnerability Work?
The issue lies in the 2D graphics subsystem (Java 2D API), responsible for processing and rendering images, shapes, and more. If an attacker can send malformed or specially crafted data to a vulnerable API that uses this component, they can cause the Java process to hang or crash, interrupting availability of your app or service.
No authentication is required. No user interaction is required. Just a request with crafted data sent over the network.
Scenario Example:
Let’s say your service exposes an endpoint which accepts image data (BMP, PNG, etc.) and manipulates it using Java's 2D API. An attacker sends a specially constructed image file (not a valid image, but made to trigger the flaw) that causes the JVM to freeze or crash while processing.
Example Exploit Scenario
Let’s take a look at an example Java code snippet that demonstrates how image handling might lead to this issue.
import javax.imageio.ImageIO;
import java.awt.image.BufferedImage;
import java.io.InputStream;
import java.net.URL;
public class ImageDoSExample {
public static void main(String[] args) throws Exception {
// Attacker controls this URL and hosts a maliciously crafted image
String imageUrl = "http://malicious-attacker.com/evil-image.png";;
try (InputStream in = new URL(imageUrl).openStream()) {
// This is where the vulnerability could be triggered
BufferedImage img = ImageIO.read(in);
System.out.println("Image loaded. Dimensions: " + img.getWidth() + "x" + img.getHeight());
}
}
}
If evil-image.png is constructed to trigger the bug in the 2D component, this code could hang or crash the JVM, leading to a denial of service.
Real-World Impact
- Attackers can repeatedly send malicious requests, causing your service to freeze multiple times, impacting reliability and user trust.
- Vulnerable endpoints (such as REST APIs handling images) are especially at risk, as attackers don’t need credentials.
- Mitigation is limited: You can’t reliably sanitize all possible image file manipulations, so patching is essential.
References
- Oracle Critical Patch Update Advisory - January 2022
- National Vulnerability Database (NVD) Entry for CVE-2022-21349
- GraalVM Release Notes
Upgrade Oracle GraalVM Enterprise to version 21.3.1 or later
- Download updates directly from Oracle or GraalVM.
Restrict exposure:
- Don’t process untrusted/remote images unless necessary.
Limit network access to endpoints using the Java 2D API.
3. Monitor and log unusually long processing times for image or media endpoints as an early sign of DoS attempts.
4. Deploy Web Application Firewall (WAF) rules that limit upload size and scan for known malformed image types.
Conclusion
CVE-2022-21349 might not be the flashiest Java exploit, but it is easy to trigger and affects a critical component used in many real-world applications. The best defense is prompt patching and reviewing your exposure to untrusted image or media input.
If you run Java apps where users upload or manipulate images—or if you expose Java APIs over the network—this is a risk you can’t afford to ignore.
More Links
- Oracle Java SE Downloads
- GraalVM Download Center
- Oracle’s security blog
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/13/2022 15:00:00 UTC