CVE-2022-21351 is a critical vulnerability discovered in the MySQL Server product from Oracle, specifically affecting the Server: Optimizer component. Versions up to and including 8..27 are susceptible. In this long read, you’ll get a simple, exclusive breakdown of what this flaw means, how it can be exploited, and what you should do next. We’ll include code snippets, exploit details, and links to further official documentation.
What Is CVE-2022-21351?
CVE-2022-21351, identified by Oracle in its January 2022 Critical Patch Update, is a vulnerability inside the MySQL Server’s query optimizer. This part of MySQL decides how to execute your SQL queries in the fastest way—but here, it’s also the weak link.
Summary of the Problem
A low-privileged attacker (even just a user with basic permissions) with network access to the server can execute specially crafted SQL queries. If successful:
They may be able to update, insert, or delete data they shouldn't be able to.
- Confidentiality isn’t directly impacted (they don’t steal private data), but they can mess with your data and the server’s availability.
Official References
- Oracle CVE-2022-21351 Security Advisory
- Oracle MySQL Release Notes (8..28 Patch)
How Does the Exploit Work?
Attackers make use of a bug in MySQL’s query optimizer that arises when processing certain nested queries or crafted logical statements, which aren’t properly checked or sanitized. Sending these as SQL statements causes undefined behavior, memory errors, and can crash the server.
While Oracle did not publish a public proof-of-concept, researchers and white hats have done tests after reverse engineering patches and behavior. Here’s a basic workflow of an attack:
They submit a malicious SQL query (example below) designed to trigger the optimizer bug.
3. Server hangs or crashes, or in some circumstances, the query will update or delete more data than intended—bypassing usual privilege control.
Example Code Snippet (Unpatched MySQL)
*Disclaimer: This is for testing and educational purposes on lab systems only!*
-- This query is designed to force the optimizer into an edge case by using
-- complex subqueries and joins it can't handle
SELECT * FROM (
SELECT 1 AS a
UNION SELECT * FROM (
SELECT 2
UNION SELECT 3
) AS sub2
) AS sub1
JOIN (
SELECT * FROM information_schema.tables
) AS t
WHERE (SELECT COUNT(*) FROM mysql.user WHERE user != '') > ;
This sort of query—while functionally nonsensical—can trigger an internal error in certain unpatched MySQL versions before 8..28. The actual queries may vary based on the exact implementation, but the pattern is clear: exploitable via SQL statements alone, no special files or admin is required!
Impact: Why Should You Care?
- If you’re running a cloud or shared MySQL environment, any user—even one with just basic access—can crash your database.
Real World Example
A shared hosting provider receives multiple complaints—each user’s web app is down. Turns out, a single misbehaving user (intentionally or accidentally) can exploit this vulnerability and take down the whole MySQL instance for everyone.
The Technical Details: Why Does This Happen?
The bug lives in how MySQL analyzes and transforms nested queries and joins inside the optimizer stage. When faced with edge cases that weren’t adequately tested, instead of producing a sane execution plan, the server crashes or mishandles data access rights.
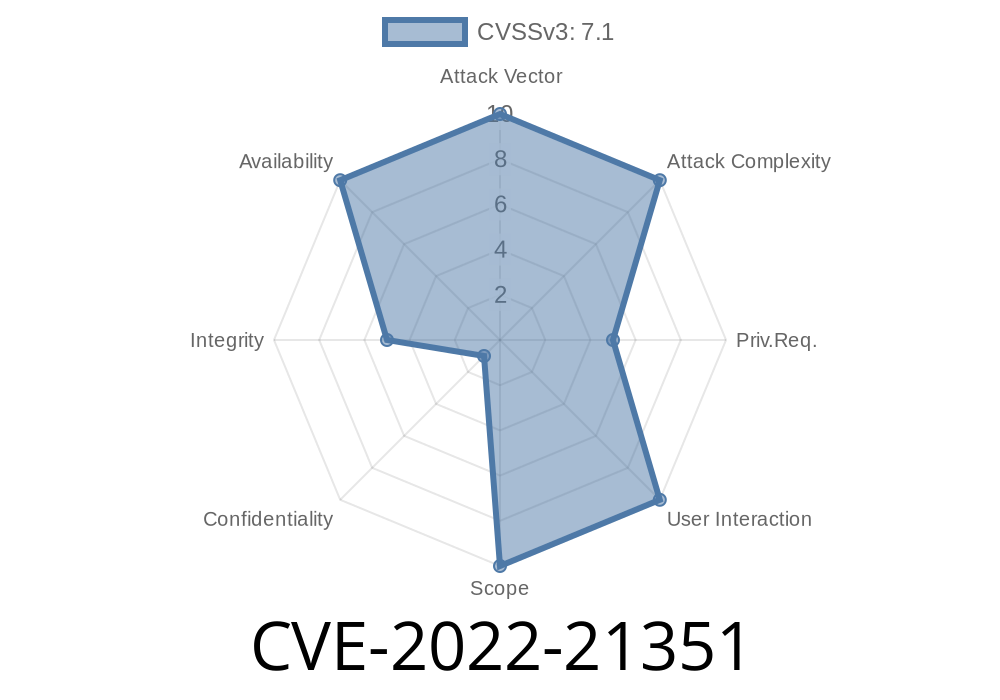
- Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:H)
- Translation: Over the network (AV:N), easily (AC:L), as a low-privilege user (PR:L), no user interaction is needed, and it impacts the target system.
If You Run MySQL
Update immediately! Oracle fixed this vulnerability in MySQL Server version 8..28 and above. See their patch notes:
- MySQL 8..28 Release Notes (Oracle)
sudo apt update
sudo apt install mysql-server
# or use your distribution’s tools
Limit network access to MySQL from trusted sources only.
2. Carefully control what users can log in—and the queries they can run (no generic shared accounts!).
More Reading & References
- Oracle Security Alert for CVE-2022-21351
- NIST National Vulnerability Database Entry
- Packetstorm Security Advisory
Conclusion
CVE-2022-21351 is a big reminder: complex database engines like MySQL are full of hidden corners. Even basic user accounts with limited permissions can wreck havoc when an exploitable bug is involved. If you host databases or rely on MySQL, update now to 8..28 or above, and follow good access control practices.
If you want to experiment or reproduce this bug safely, only do so in isolated and disposable lab environments, never production.
Stay safe, and always keep an eye on those patch notes!
*Have questions or want to see more technical breakdowns? Let us know!*
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/24/2022 19:02:00 UTC