In January 2022, Oracle announced a security vulnerability in the MySQL Connectors product, specifically affecting the Connector/J component. Labelled as CVE-2022-21363, this vulnerability poses a significant risk to systems relying on Oracle MySQL with Connector/J versions 8..27 and earlier.
If exploited, a high-privileged attacker with network access could compromise the confidentiality, integrity, and availability of MySQL Connectors, which could lead to the complete takeover of affected systems.
- Component Affected: Connector/J
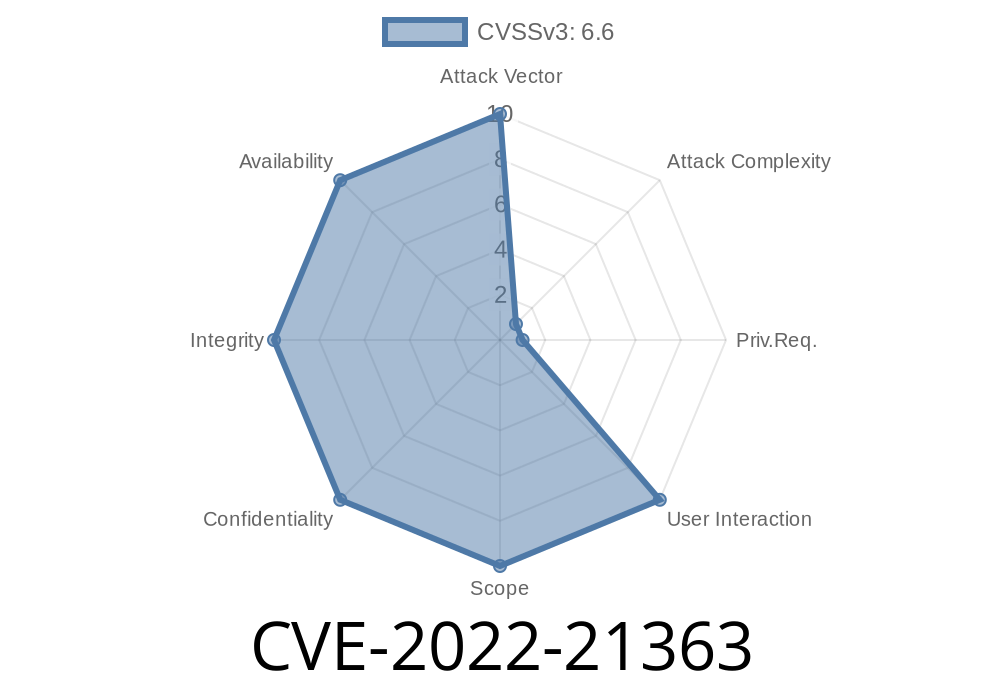
CVSS v3.1 Base Score: 6.6 (High)
- CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H
## What is MySQL Connector/J?
MySQL Connector/J is an official JDBC driver for MySQL, widely used in Java applications to interact with MySQL databases. Many applications depend on this connector for data access, making vulnerabilities in it particularly dangerous.
How Does the Vulnerability Work?
The issue lies in the way Connector/J processes certain network requests. Although Oracle has not published detailed proof-of-concept exploits, the available information suggests improper input validation or unsafe handling of user-supplied data over the network.
Example Exploit Scenario
An attacker, who already has high privileges (such as having a user account with elevated permissions in the target application), could send specially crafted database queries or protocol messages to the vulnerable MySQL Connector/J. This could trick the connector into executing unauthorized actions, leaking data, or letting the attacker control or disrupt database connections.
Here’s a simplified breakdown
1. Attacker gains high-privileged access (this isn’t a public exploit—attackers need legitimate accounts with strong permissions).
2. The attacker sends crafted JDBC queries or uses manipulative protocol sequences against the Java application using Connector/J < 8..28.
3. This triggers the flaw—resulting in data exposure, corruption, arbitrary command execution, or even denial of service.
Code Snippet: What Does Unsafe Code Look Like?
Please note: The following is an *illustrative* code snippet based on general patterns seen in Java JDBC vulnerabilities, not the actual vulnerable code, since Oracle did not release full technical details. It is meant for educational purposes only.
// Pseudo-code example of unsafe JDBC query execution
String userInput = request.getParameter("query");
// Directly passing user input to the database is dangerous!
// If the connector does not filter or validate input properly, this can be exploited
Statement stmt = connection.createStatement();
ResultSet rs = stmt.executeQuery(userInput);
// Attacker could inject malicious queries or statements here
If the connector, due to its flaw, would process protocol packets in an unsafe manner or mishandle certain JDBC operations, an attacker could leverage it for further attacks.
What Could Happen?
- Full Takeover of the Connector: An attacker could use the vulnerability to run arbitrary JDBC calls or escalate access.
Data Breach: Sensitive information handled by the Java app could be stolen.
- Data Corruption/Destruction: Malicious operations might corrupt important database tables.
Who is at Risk?
Any Java application using MySQL Connector/J version 8..27 or earlier that is accessible over the network and uses shared or elevated privileges.
How Can You Fix It?
Upgrade Immediately:
Oracle has patched this issue in Connector/J 8..28 and later.
- MySQL Connector/J Download Page
References
- Oracle Critical Patch Update Advisory - January 2022
- NVD (National Vulnerability Database) Entry for CVE-2022-21363
- Oracle MySQL Connector/J Release Notes
- CVSS Calculator
Summary Table
| Field | Value |
|-------|-------|
| CVE ID | CVE-2022-21363 |
| Component | MySQL Connector/J |
| Vulnerable Versions | 8..27 and prior |
| Attack Vector | Network |
| Privileges Required | High |
| Impact | Confidentiality, Integrity, Availability (Complete) |
| Patch Available? | Yes (8..28+) |
Closing Thoughts
CVE-2022-21363 is a serious vulnerability in one of the most widely used Java database drivers. While not trivial to exploit (as it demands high privileges), the potential consequences are severe. If you haven't already, update to Connector/J 8..28 or newer—and always practice secure coding and privilege management in your applications.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 05/27/2022 14:50:00 UTC