Oracle WebLogic Server is a popular Java EE application server widely used in enterprise environments. In January 2022, Oracle announced a critical vulnerability tracked as CVE-2022-21371, affecting the Web Container component of WebLogic Server. This post gives you an in-depth, easy-to-understand breakdown of this vulnerability, including steps to exploit, sample code snippets, links for original references, and practical remediation advice.
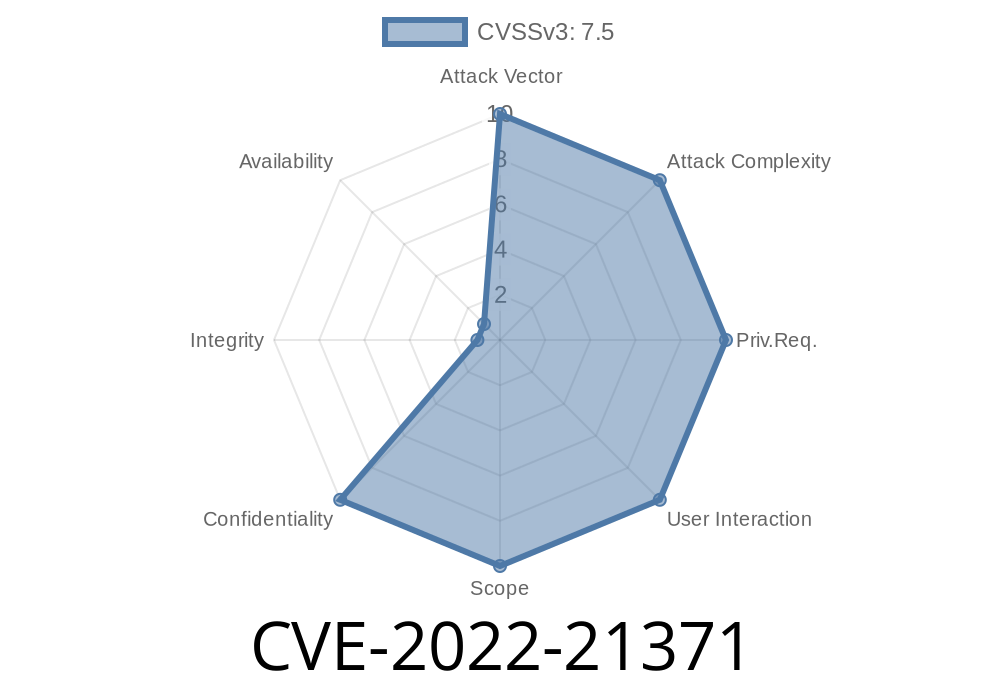
CVSS 3.1 Score: 7.5 (High)
- CVSS Vector: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N (Network/Low/None/None/Unchanged/High/None/None)
What Is CVE-2022-21371?
CVE-2022-21371 is a severe security flaw in Oracle WebLogic Server. This bug lets an attacker—who doesn’t even need a username or password—gain access to data that should never leave your WebLogic environment. All the attacker needs is network access to your server and the right HTTP request.
Potential full access to all data available to the affected server
This is a “confidentiality” flaw: attackers can read but not change or delete data via this bug.
How Does the Vulnerability Work?
Oracle patched this vulnerability in their January 2022 Critical Patch Update. However, they did not release technical details. Security researchers observed that attackers could use specially crafted HTTP requests to make the server reveal restricted web resources or application files.
Example Exploit Scenario
1. Attacker scans a corporate network for exposed WebLogic instances (ports 7001/7002 by default).
Proof-of-Concept Exploit
Because details are restricted, the following code presents a common pattern for HTTP-based data exposure vulnerabilities in Java applications. This doesn’t represent the exact exploit but shows how attackers might probe servers.
Python Example
import requests
# Replace with the actual server's address and port
url = 'http://target-weblogic:7001/';
# Some PoCs target sensitive files or paths like /WEB-INF/web.xml
potential_sensitive_paths = [
'WEB-INF/web.xml',
'META-INF/MANIFEST.MF',
'admin/console'
]
for path in potential_sensitive_paths:
exploit_url = url + path
response = requests.get(exploit_url)
print(f'[*] Trying {exploit_url}...')
if response.status_code == 200:
print(f'[!] Sensitive file exposed at: {exploit_url}')
print(response.text[:500]) # Print first 500 chars
else:
print(f'[-] {path} not accessible ({response.status_code})')
Checks if the server leaks content that should not be public
This is a generic technique. Real-world exploits might require a more tailored payload based on the server configuration.
Official References
- Oracle Critical Patch Update Advisory - January 2022 (CVE-2022-21371)
- NIST NVD Entry for CVE-2022-21371
- Oracle WebLogic Security Updates
Patch Immediately:
Apply the latest Oracle Critical Patch Update for your version. *Do not wait*; this vuln requires no credentials.
Limit Network Exposure:
If possible, never expose your WebLogic admin or app servers directly to the internet. Use firewalls, VPNs, or internal-only networks.
Monitor Access Logs:
Look for suspicious HTTP requests (unusual resource paths, repeated requests to protected areas, etc.).
Upgrade Old Versions:
If you can’t patch, upgrade to the latest supported series. Oracle does not backport all critical fixes to older, unsupported versions.
Final Thoughts
CVE-2022-21371 is a high-profile mistake that attackers can (and do) use for direct data theft from unprotected Oracle WebLogic servers. Proof-of-concept scripts and active exploit attempts have followed every major Oracle patch. Immediate patching and good network hygiene are your best defenses.
Don’t forget:
- Check your environment for old/test WebLogic instances.
Always stay current with Oracle’s quarterly security bulletins.
> Stay Secure:
> Subscribe to security alerts at Oracle’s Security Page, and test your systems proactively.
If you want further details or have a unique network topology, let us know! We can provide tailored advice.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 02/09/2022 20:46:00 UTC