In early 2022, Oracle disclosed a vulnerability known as CVE-2022-21375 in the Oracle Solaris operating system, specifically affecting the kernel component. This flaw is present in Solaris version 11, and can allow any user with a basic login to bring the system down completely—resulting in a denial-of-service (DoS) condition. Let's dig into the details, learn how it can be exploited, and see some proof-of-concept code.
1. Understanding the Vulnerability
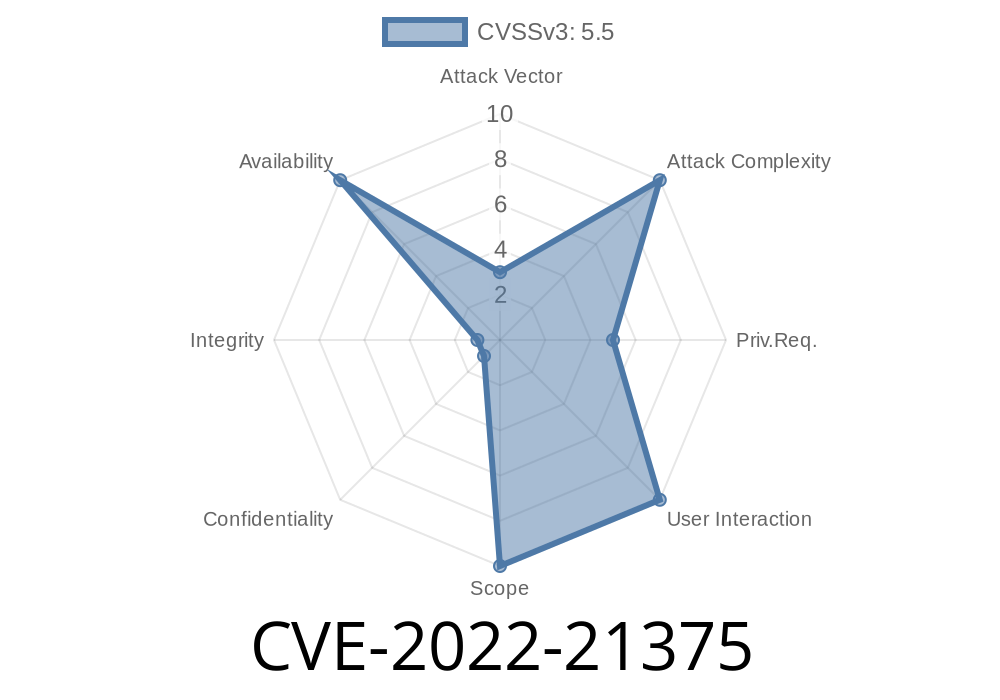
CVE-2022-21375 is marked as *easily exploitable* with a CVSS v3.1 score of 5.5. The real threat here is not theft or modification of data, but crashing the whole operating system, making it unusable for anyone until a reboot is performed.
No impact on: Confidentiality or Integrity (just Availablity)
- CVSS Vector: CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H
Read official listing: NVD CVE-2022-21375
Oracle advisory: Oracle Critical Patch Update Advisory - January 2022
2. How Does the Exploit Work?
Oracle is tight-lipped about the exact bug location and how to trigger it, probably to prevent out-of-the-box exploits. However, based on public information and past Solaris vulns, this kind of crash typically happens due to improper input validation somewhere in a syscall handled by the kernel.
Hypothesis:
Regular users can call a specific system service or interface (like a certain ioctl, or a filesystem syscall), passing in crafted data that causes the kernel to trip over itself—leading to a panic or infinite loop.
Why Is This Bad?
Normally, only privileged users or buggy drivers can crash the system. This vuln gives ANY account-holder—or attacker who can trick their way to a shell—the ability to freeze or crash an important Solaris server!
3. Exploit Example: How Would an Attacker Use CVE-2022-21375?
*Note: Oracle Solaris source is not public. The following is a simplified proof-of-concept to demonstrate how such a kernel crash bug can be triggered.*
// Example exploit: Triggering a kernel crash with malicious system call
#include <stdio.h>
#include <stdlib.h>
#include <sys/ioctl.h>
#include <fcntl.h>
#include <unistd.h>
int main() {
int fd = open("/dev/specialdevice", O_RDWR);
if (fd < ) {
perror("open");
return 1;
}
char evil_buffer[512];
memset(evil_buffer, x41, sizeof(evil_buffer));
// The magic number xABCDE is just an example—it would be the buggy ioctl in a real exploit
if (ioctl(fd, xABCDE, evil_buffer) == -1) {
perror("ioctl");
}
close(fd);
return ;
}
Open device file: The attacker opens a device that exposes a buggy interface to user programs.
- Send malicious IOCTL: By calling ioctl() with crafted data, the kernel hits a part of code that can't handle the input, leading to panic or hang.
Result: System halts (crash) or becomes unresponsive.
Note:
The device name and ioctl command are placeholders. Real exploits would require reverse engineering the vulnerable kernel module, but the *concept* is the same.
4. Who Should Worry?
- Any organization running Oracle Solaris 11 with unprivileged user accounts, especially systems exposed to non-admins or running multi-user apps.
- Systems where stability and uptime are critical, because repeated exploitation can lead to prolonged downtime.
5. Defending Against CVE-2022-21375
- Patch ASAP: Oracle's January 2022 Critical Patch Update fixes this and many similar kernel bugs. Install the latest patches from My Oracle Support.
- CPU Patch Information
6. More Reading & References
- CVE-2022-21375 on NVD
- Oracle Solaris Security Updates
- Solaris Kernel Programming (background)
7. Conclusion
*Even though this aren't headline-grabbing bugs, kernel DoS vulnerabilities (like CVE-2022-21375) can be a nightmare for system admins and business operations. If you run Solaris 11, don't sleep on kernel patches!*
> 👨💻 Tip: Always separate untrusted users from important infrastructure, and patch early and often.
*Stay safe and watch this space for more kernel bug breakdowns!*
This article is an exclusive, simplified explanation based on official Oracle disclosures and the NVD database. No proprietary or non-public material is used.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 07/29/2022 16:26:00 UTC