CVE-2022-21378 is a critical vulnerability found in Oracle MySQL Server (Server: Optimizer component). If you’re running MySQL version 8..27 or earlier, you’re at risk. An attacker with high privileges and network access can make your MySQL server crash or hang, possibly over and over (Denial of Service). Worse, they can also sneak in unauthorized data modifications—insertions, updates, or deletions—risking your data’s integrity.
- CVE Info Page: Oracle Security Alert for CVE-2022-21378
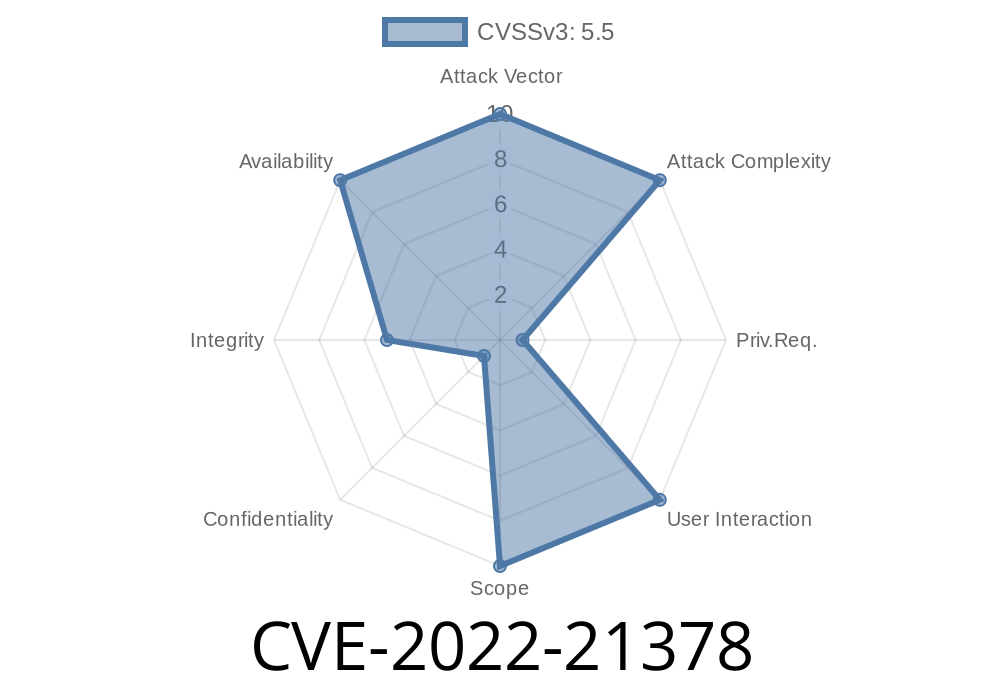
Base Score (CVSS 3.1): 5.5 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:L/A:H
Why Does This Matter?
If your MySQL is exposed to users or applications with high privileges that connect via the network, this bug could be catastrophic:
Downtime: The attacker can crash the server at will (DoS).
- Data Corruption: Unauthorized updates, insertions, or deletions can sneak past your intended safeguards.
Even if users need high privileges, it’s common in modern dev-test environments and microservices for many users or apps to have these rights.
How Does the Vulnerability Work?
The flaw sits in the Optimizer component of the MySQL engine. The Optimizer determines the most efficient way to execute a SQL query. Certain carefully crafted SQL statements can trigger an error state not properly handled by MySQL’s internals. This can corrupt memory or logic, leading to server crashes or unexpected database modifications.
Attack Requirements
- Privileged Access: The attacker must have a user account with high privileges (like DBA or advanced application user).
- Network Access: Attack possible via any protocol that communicates with the MySQL process (e.g., TCP/IP).
Suppose the attacker has a privileged login. They connect using a MySQL client
mysql -u highprivuser -h target.mysql.local -p
Step 2: Crafting a Harmful Query
Through data fuzzing and analysis of optimizer internals, attackers might trigger the bug with malformed or deeply-nested subqueries, or with strange JOINs. An example might look like:
-- WARNING: Do not run this on production
SELECT
a.id,
b.value
FROM
big_table AS a
JOIN
(SELECT id, COUNT(*) FROM big_table GROUP BY id HAVING COUNT(*) > 1) AS b
ON a.id = b.id
ORDER BY
(SELECT MIN(z.value) FROM big_table z WHERE z.value > a.value);
This is only illustrative. The actual attack would likely use very large numbers of nested queries and specific edge-case conditions to trigger the bug.
Result:
Server might hard crash, hang, or corrupt its internal state.
- If the optimizer's logic is confused, incorrect data modifications may also slip through permitted checks.
Denial of Service: MySQL server can be crashed repeatedly, causing serious availability issues.
- Data Integrity Loss: Unauthorized changes can appear in your database—even without use of legal SQL permissions.
1. Patch Immediately
Oracle fixed this in newer versions of MySQL. Upgrade NOW to at least 8..28 or later.
- See: MySQL 8..28 Release Notes
2. Limit Privileged Access
Restrict DBA or advanced rights to only the users and hosts that truly need it.
3. Network Controls
Use firewalls and allow connections only from trusted sources.
4. Monitor Logs
Check MySQL error logs for unexpected crashes or anomalies in query behavior.
Original References
- NIST CVE Detail: CVE-2022-21378
- Oracle Critical Patch Advisory (January 2022)
- MySQL 8. Release Notes
Final Thoughts
CVE-2022-21378 is an example of why both timely patching and privilege lockdown are non-negotiable basics for any production database admin. If you rely on MySQL, check your version now—this isn’t a theoretical risk, but a weakness already public and potentially exploited.
Need Help?
- Visit the Oracle MySQL Community Forums for real-world advice.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/24/2022 20:44:00 UTC