Oracle WebLogic Server is a popular Java EE application server used by organizations worldwide for hosting enterprise apps and portals. In January 2022, Oracle disclosed a critical security flaw tracked as CVE-2022-21386 in the Web Container component—impacting versions 12.1.3.., 12.2.1.3., 12.2.1.4., and 14.1.1... This vulnerability stands out not only for its broad impact, but also for its ease of exploitation and the potential for unauthorized data manipulation, even without credentials.
This post will break down what CVE-2022-21386 is, how it works, how attackers can exploit it, and how you can protect your systems. We’ll include simple explanations, practical code snippets, and direct references for further learning.
What is CVE-2022-21386?
CVE-2022-21386 is a weakness in the “Web Container” feature of Oracle WebLogic Server, a core part that processes user HTTP requests. The issue allows a remote attacker—without authentication—to gain unauthorized read, update, insert, or delete access to certain server data. This access is possible if:
the attacker can reach the server over HTTP (network access, no credentials required);
- a user, such as an admin or employee, is tricked into interacting with malicious content (like clicking a crafted link).
Oracle notes that successful attacks may have a significant impact on other products beyond just WebLogic, since this server is a central middleware component.
14.1.1..
If you use any of these, make sure security patches from Oracle’s Critical Patch Update Advisory are applied.
How Does the Attack Work?
Short answer:
An attacker gets a victim (like an admin or regular user) to click or browse to a malicious URL, either in the same browser session or by manipulating HTTP requests. Once triggered, the attacker can control or view part of the data that the WebLogic server can access.
Why is user interaction needed?
The Common Vulnerability Scoring System (CVSS) for this bug includes “UI:R”—meaning User Interaction is Required. The attack setup might involve:
Injecting scripts in web apps served by WebLogic.
Once the victim interacts, data can be inserted, updated, deleted, or read by the attacker, depending on their crafted payload.
Example Exploit Flow
Below, we illustrate a simplified attack scenario, using a hypothetical vulnerable endpoint.
1. Attacker Prepares the Payload
The attacker creates a crafted HTTP request, for example an HTML file with a hidden form or a malicious JavaScript. Here’s a simple example:
<!-- Malicious phishing page hosted by attacker -->
<!DOCTYPE html>
<html>
<body>
<h1>Important Update – Click Below</h1>
<form id="evil_form" action="https://victim-weblogic-server/vulnerableEndpoint"; method="POST">
<input type="hidden" name="sql" value="DELETE FROM users WHERE id=1" />
<input type="submit" value="Update Now" />
</form>
<script>
// Auto-submit the form (or wait for user click)
document.getElementById('evil_form').submit();
</script>
</body>
</html>
This page, when visited by a logged-in user, triggers a request to the WebLogic server, executing a vulnerable endpoint that processes the post data. If CSRF protections or misconfigured endpoints are present, this can cause data deletion or tampering.
2. Victim Clicks the Link
The attacker sends a phishing email or message to a user with a link to the above page. When the user clicks, their browser issues the malicious request using their own credentials or session.
3. Payload Reaches WebLogic Server
The server, vulnerable to CVE-2022-21386, fails to properly verify or authenticate the request and executes the underlying action—such as inserting, deleting, or reading sensitive data.
Why is this Vulnerability Dangerous?
- No authentication needed: An attacker doesn’t need a username or password to trigger the weakness—just network access to the server.
Human interaction: Clever phishing or social engineering increases the risk.
- Widespread impact: Exploitation might allow the attacker to access or manipulate data not just in WebLogic, but in other applications that communicate with it.
- Data manipulation: Unauthorized “insert, update, delete” means potentially severe data loss or corruption.
CVE and References
- Official Oracle Advisory (January 2022)
- NIST CVE Entry: CVE-2022-21386
- Oracle WebLogic Server Documentation
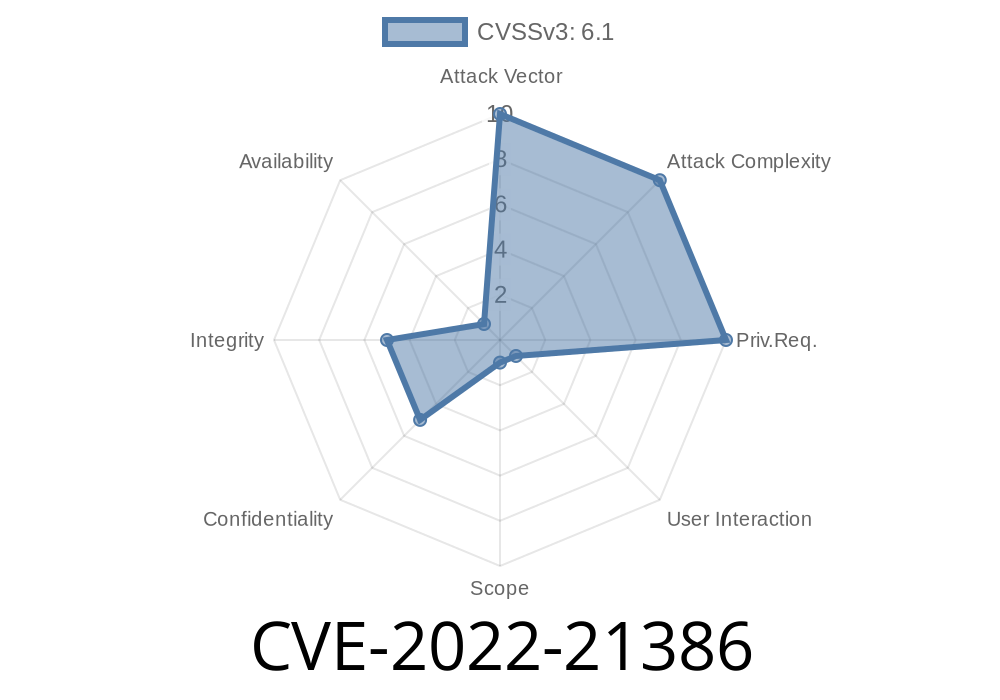
CVSS Base Score: 6.1 (Medium)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
- AV:N: Attack Vector: Network (over the internet/LAN)
How Can You Defend Against CVE-2022-21386?
1. Patch Immediately
Download and install the latest Oracle CPU patches for your WebLogic version. See Oracle’s list of patches here.
2. Restrict network access
Limit WebLogic management and admin interfaces to trusted hosts only.
3. Educate users
Help users spot phishing and suspicious links.
4. Enable CSRF protection
Where possible, add Cross-Site Request Forgery protections and strong session validation to all endpoints.
5. Monitor logs and traffic
Watch for unusual requests or unexpected data changes in WebLogic logs.
Conclusion
CVE-2022-21386 is a serious risk for any organization running Oracle WebLogic Server—especially those with internet-facing endpoints and unpatched systems. Because it doesn’t require a password—just a little social engineering and a vulnerable server—the best defense is rapid patching, user education, and smart network restrictions.
For more technical details or updates, always refer directly to the Oracle security advisory or the official NIST CVE page.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/25/2022 03:06:00 UTC