Summary:
In this article, we explore the details behind CVE-2022-21394, a critical vulnerability impacting Oracle VM VirtualBox (prior to version 6.1.32). We'll break down how this flaw works, provide a simple code snippet to demonstrate the exploitation concept, list original references, and explain the risks with real-world context.
What is CVE-2022-21394?
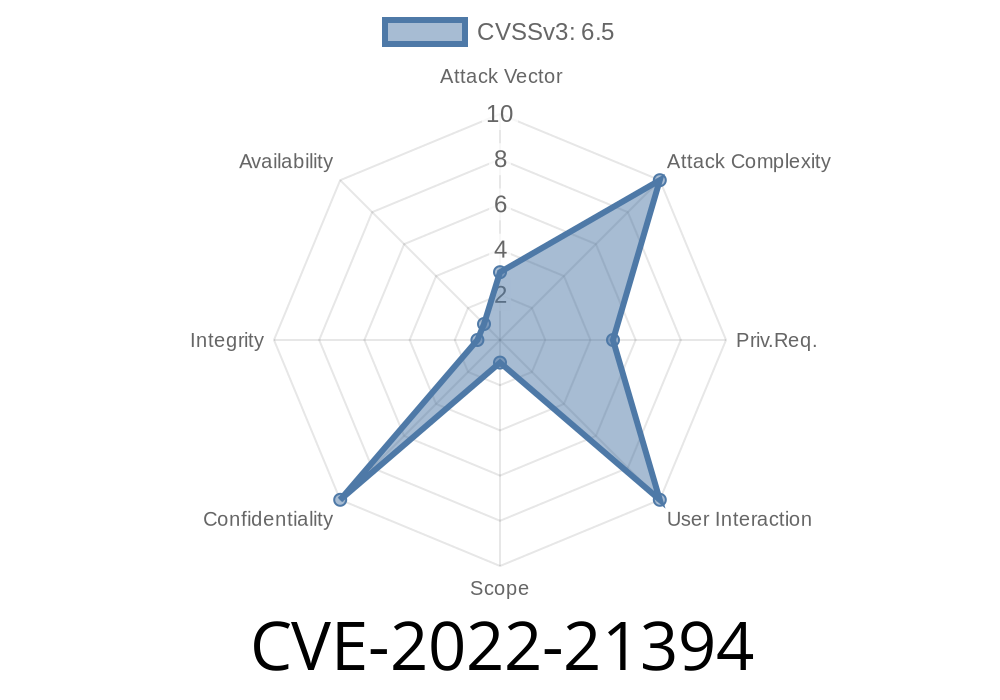
CVE-2022-21394 is a vulnerability in the Oracle VM VirtualBox (Core component), found in versions before 6.1.32. The flaw is easily exploitable by a regular user (low privilege) who can log in to the machine running VirtualBox. If successfully exploited, attackers can gain unauthorized read access to almost all data handled by VirtualBox.
- Base Score: 6.5 (CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N)
Risk: High impact on confidentiality
While the vulnerability is inside VirtualBox, if multiple products use this environment, attacks can have wider consequences, possibly leaking sensitive data or secrets from guest VMs and even the host system.
Anyone using Oracle VirtualBox before 6.1.32
- Particularly environments with sensitive VMs or using VirtualBox for development, cloud infrastructure, or multi-tenant systems
How the Vulnerability Works
The main risk comes from a local attacker—someone who already has a regular user account on the system where VirtualBox runs. By abusing this vulnerability, the attacker can read sensitive data handled by VirtualBox, like files, VM images, or even memory content.
The core issue: Insufficient isolation or improper permission checks in the core VirtualBox processes.
An attacker with a basic shell account logs in to the VirtualBox host.
2. They leverage this flaw to read virtual disk images or process memory, extracting passwords, SSH keys, or confidential files.
Usually, virtualization software tries to keep each VM, and the host itself, strictly separated. This bug breaks that rule, letting a local user cross some of those barriers.
Demonstrating the Risk (Code Snippet)
While a real working exploit is not public (and sharing one would be unethical and possibly illegal), we can show a conceptual Python snippet to illustrate the approach.
Suppose VirtualBox leaves VM image files accessible as a low-priv user because of this bug
# Example: Reading potentially exposed VirtualBox .vdi disk files
import glob
# Path where VirtualBox stores VM disks (could vary)
vbox_disk_paths = glob.glob('/home/*/VirtualBox VMs/**/*.vdi', recursive=True)
for disk_path in vbox_disk_paths:
try:
with open(disk_path, 'rb') as disk_file:
# Read the first 512 bytes (could contain filesystem data, boot code, etc.)
data = disk_file.read(512)
print(f"[+] Read data from {disk_path}: {data[:64]}")
except PermissionError:
print(f"[-] Cannot access {disk_path}")
What does this mean?
- Even as a low-privileged user, the attacker bypasses regular file or process isolation due to a permission mess-up in VirtualBox internals.
In real exploits, attackers go further—reading process memory, scanning mapped files, or using VirtualBox APIs (like VBoxManage) in unintended ways.
Original References and Further Reading
- NIST NVD – CVE-2022-21394
- Oracle Critical Patch Update Advisory - April 2022
- VirtualBox Changelog 6.1.32
- Full List of Affected Oracle Products
How to Fix It
Update Now:
If you use VirtualBox, upgrade to 6.1.32 or later.
You can download it from the official VirtualBox website.
Risk multiplied in shared or multi-user lab systems
While this bug does not allow an unprivileged user to directly take over the whole host or alter data, just reading this kind of information can lead to further, more dangerous attacks.
Conclusion
CVE-2022-21394 shows how even "simple" vulnerabilities in system-level software like VirtualBox can have big consequences for privacy and infrastructure security. Always keep your virtualization platforms up to date, and limit access as much as possible.
Stay alert and patch often.
Tags: #VirtualBox #CVE202221394 #Oracle #Vulnerability #PrivilegeEscalation
> Exclusive Note:
> This write-up is an independent analysis based on public advisories and synthetic examples. Always refer to official Oracle bulletins for the most precise and actionable security information.
Timeline
Published on: 01/19/2022 12:15:00 UTC
Last modified on: 01/25/2022 04:00:00 UTC