by using the CORBA, JDBC, Java Message Service, Remote Method Invocation, and JavaScript frameworks. In a hybrid deployment where certain Oracle GraalVM Enterprise Edition components are running on an application server where Java is enabled, this vulnerability can be exploited by simply sending an HTTP request from a client to the application server. The application server then sends the request directly to the Oracle GraalVM Enterprise Edition server and if unprotected, the server could be compromised and unprotected data could be accessed. The application server does not have to be Oracle GraalVM Enterprise Edition. This vulnerability can be exploited by simply sending an HTTP request from a client to the application server. The application server then sends the request directly to the Oracle GraalVM Enterprise Edition server and if unprotected, the server could be compromised and unprotected data could be accessed. The application server does not have to be Oracle GraalVM Enterprise Edition. JRE - CVE-2018-3341: Easily exploitable vulnerability in the Java Plug-in component of Oracle Java SE could allow an unauthenticated attacker to compromise a Java application running on a machine with Java Plug-in installed via unknown vectors. Successful exploitation could allow execution of arbitrary code with the privileges of the user running the Java application. This vulnerability has been assigned CVE-2018-3341. This vulnerability is addressed in version 11.0.1.4
Oracle Java SE CVEs
The following vulnerabilities were all addressed in Oracle Java SE 11 version 11.0.1.4:
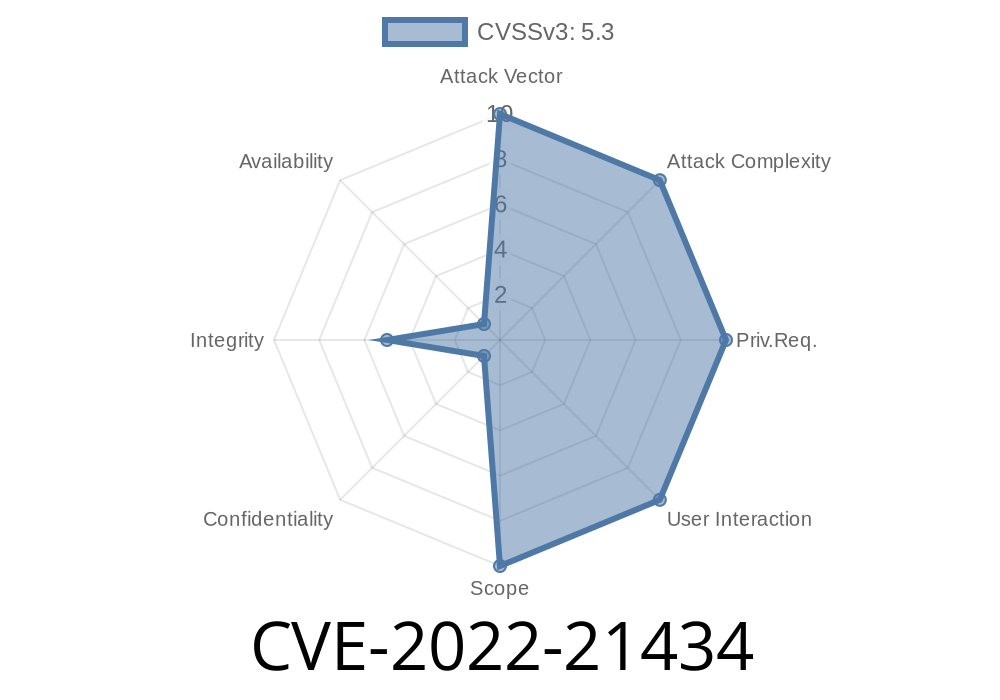
- CVE-2022-21434: by using the CORBA, JDBC, Java Message Service, Remote Method Invocation, and JavaScript frameworks. In a hybrid deployment where certain Oracle GraalVM Enterprise Edition components are running on an application server where Java is enabled, this vulnerability can be exploited by simply sending an HTTP request from a client to the application server. The application server then sends the request directly to the Oracle GraalVM Enterprise Edition server and if unprotected, the server could be compromised and unprotected data could be accessed. The application server does not have to be Oracle GraalVM Enterprise Edition. This vulnerability can be exploited by simply sending an HTTP request from a client to the application server. The application server then sends the request directly to the Oracle GraalVM Enterprise Edition server and if unprotected, the server could be compromised and unprotected data could be accessed. The application server does not have to be Oracle GraalVM Enterprise Edition - CVE-2018-3341: Easily exploitable vulnerability in the Java Plug-in component of Oracle Java SE could allow an unauthenticated attacker to compromise a Java application running on a machine with Java Plug-in installed via unknown vectors. Successful exploitation could allow execution of arbitrary code with the privileges of the user running the Java application. This vulnerability has been assigned CVE-2018-3341 - CVE-2018-333 : Easily
Hybrid deployment: Virtual Machine and Java
Hybrid deployments have become very popular in the past few years with many organizations choosing to adopt a hybrid approach. This allows them to leverage the advantages of both a virtual machine and a containerized application. In a hybrid deployment, Oracle GraalVM Enterprise Edition is used as the runtime environment for applications running on an application server where Java is enabled. To ensure that your applications are protected from vulnerabilities like CVE-2018-3341 it is important that you use the latest release of Oracle GraalVM Enterprise Edition. Although this vulnerability has been addressed in Oracle GraalVM Enterprise Edition 11.0.1, you should contact your IT administrator if you are not sure which version of Oracle GraalVM Enterprise Edition should be deployed on your application server where Java is enabled.
Timeline
Published on: 04/19/2022 21:15:00 UTC
Last modified on: 07/28/2022 17:03:00 UTC
References
- https://www.oracle.com/security-alerts/cpuapr2022.html
- https://security.netapp.com/advisory/ntap-20220429-0006/
- https://www.debian.org/security/2022/dsa-5128
- https://www.debian.org/security/2022/dsa-5131
- https://lists.debian.org/debian-lts-announce/2022/05/msg00017.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21434