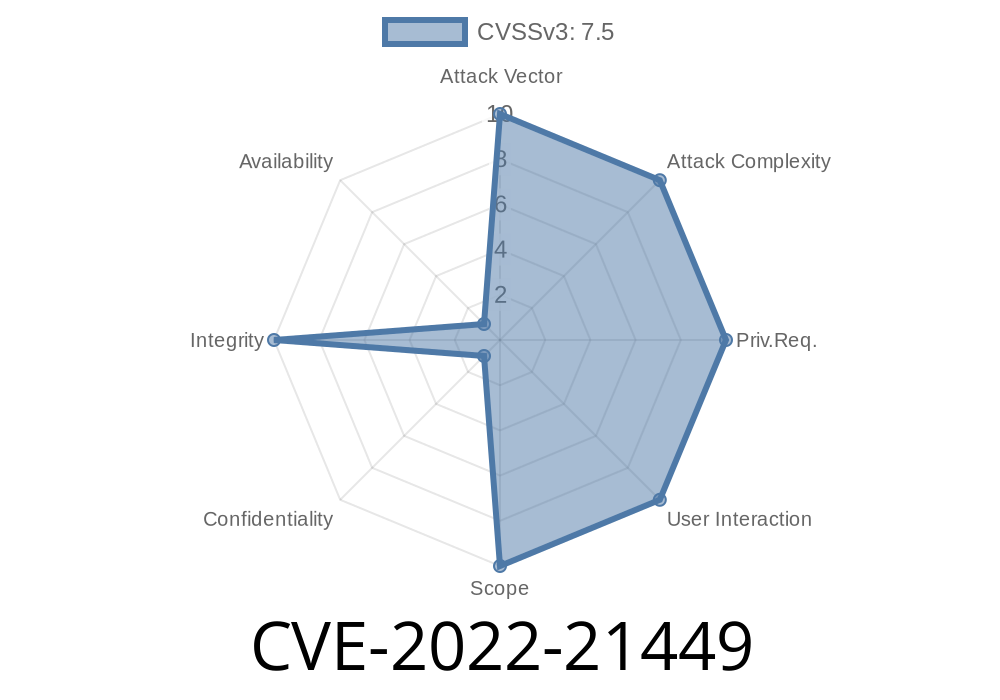
by using the Java API in the Oracle Java SE or Oracle GraalVM Enterprise Edition component to create, access, update, delete or modify data; or by using the JavaScript API to create, access, update, delete or modify data. In order to exploit this vulnerability, an attacker must be able to log in to an affected system and run JavaScript code. An attacker must have access to a victim's network and be able to inject JavaScript code into a web page that the victim views, in order for the attack to work. An attacker can run JavaScript code directly or via an application (e.g., a vulnerable Java Web Start or Java applet) that the user downloads and views. In all cases, an attacker would have to convince users to install JavaScript code on their clients, or have access to a network where the installation takes place, in order to exploit this vulnerability. The vulnerability can be exploited remotely or via a proxy. How does this vulnerability work? The vulnerability is caused by the way the Oracle Java SE, Oracle GraalVM Enterprise Edition component validates TLS certificates. What you need to know about this vulnerability? An attacker can exploit this vulnerability by sending a specially crafted SSL/TLS handshake to an application in an Oracle Java SE, Oracle GraalVM Enterprise Edition component that uses the Java API and the Oracle Java SE, Oracle GraalVM Enterprise Edition component to create, access, update, delete or modify data. An attacker would have to be able to log in to
Oracle Java SE and Oracle GraalVM Enterprise Edition Software Requirements
In order to exploit this vulnerability, an attacker must be able to log in to an affected system and run JavaScript code. An attacker must have access to a victim's network and be able to inject JavaScript code into a web page that the victim views, in order for the attack to work. An attacker can run JavaScript code directly or via an application (e.g., a vulnerable Java Web Start or Java applet) that the user downloads and views. In all cases, an attacker would have to convince users to install JavaScript code on their clients, or have access to a network where the installation takes place, in order to exploit this vulnerability. The vulnerability can be exploited remotely or via a proxy.
Vulnerability Scenario
An attacker could exploit this vulnerability by sending a specially crafted SSL/TLS handshake to an application in the Oracle Java SE, Oracle GraalVM Enterprise Edition component that creates, accesses, updates, deletes or modifies data. To do so, an attacker would need to log into the system and run JavaScript code. The JavaScript code would have to be able to run on the server and then on the client.
The vulnerability is caused by the way that the Oracle Java SE, Oracle GraalVM Enterprise Edition component validates TLS certificates.
Oracle Java SE, Oracle GraalVM Enterprise Edition and Oracle APIs Overview
This vulnerability is caused by the way Oracle Java SE, Oracle GraalVM Enterprise Edition component validates TLS certificates.
An attacker would have to log in to an affected system and run JavaScript code.
An attacker must have access to a victim's network and be able to inject JavaScript code into a web page that the victim views in order for the attack to work.
Timeline
Published on: 04/19/2022 21:15:00 UTC
Last modified on: 05/13/2022 12:55:00 UTC
References
- https://www.oracle.com/security-alerts/cpuapr2022.html
- http://www.openwall.com/lists/oss-security/2022/04/28/2
- http://www.openwall.com/lists/oss-security/2022/04/28/4
- http://www.openwall.com/lists/oss-security/2022/04/28/3
- http://www.openwall.com/lists/oss-security/2022/04/28/6
- http://www.openwall.com/lists/oss-security/2022/04/28/5
- http://www.openwall.com/lists/oss-security/2022/04/28/7
- https://security.netapp.com/advisory/ntap-20220429-0006/
- http://www.openwall.com/lists/oss-security/2022/04/29/1
- http://www.openwall.com/lists/oss-security/2022/04/30/1
- http://www.openwall.com/lists/oss-security/2022/04/30/2
- http://www.openwall.com/lists/oss-security/2022/04/30/3
- http://www.openwall.com/lists/oss-security/2022/04/30/4
- http://www.openwall.com/lists/oss-security/2022/05/01/1
- http://www.openwall.com/lists/oss-security/2022/05/01/2
- http://www.openwall.com/lists/oss-security/2022/05/02/1
- https://www.debian.org/security/2022/dsa-5128
- https://www.debian.org/security/2022/dsa-5131
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21449