VULNERABILITY DESCRIPTION: A flaw exists in the processing of proxy data in the EBS B2B component. An attacker can exploit this vulnerability to create a false sense of trust and trick a user into visiting a malicious website and possibly disclose sensitive information. Access to the underlying system through the HTTP protocol is required for this vulnerability. An attacker does not need to force users to visit a malicious website. Instead, the attacker can compromise the trust relationship between a server and a proxy by sending a crafted HTTP request header. An attacker can perform a man-in-the-middle attack by compromising the trust relationship between a proxy and a server. An attacker can send a crafted HTTP request header to the server, which will cause the server to generate a false sense of trust. When the proxy receives a request from a user, it will determine whether the request has been received from the server or another proxy. If the request was received from another proxy, the proxy will determine whether the server has been compromised. If the server has been compromised, the proxy will generate a false sense of trust and forward the request to the server. As a result, the server generates false data that the proxy will forward to the user. In the case of a false sense of trust, the proxy will display the false data of the server to the user. This will trick the user into thinking that the server is genuine when it is not.
Vulnerability Scenario: An attacker performs a man-in-the-middle attack to trick a user into visiting a malicious website
A man-in-the-middle attack is when an attacker sits in between two parties, one of which they are not. The attacker can intercept and forward traffic from each party and manipulate the data to suit their needs. An attacker can also collect information from users or devices on either side of the man-in-the-middle attack without alerting the other users. In this scenario, an attacker tricks a user into visiting a malicious website by performing a man-in-the-middle attack on the user's browser traffic. The attacker uses this vulnerability to create false sense of trust so that the user visits and interacts with their malicious website.
Vulnerability Scenario:
Scenario 1: A website is compromised by an attacker.
An attacker has compromised a website and is using it as a man-in-the-middle attack to send HTTP requests to the servers of legitimate websites. An attacker sends a crafted HTTP request header to the server, which will cause the server to generate a false sense of trust. When the proxy receives a request from a user, it will determine whether the request has been received from the server or another proxy. If the request was received from another proxy, the proxy will determine whether the server has been compromised. If the server has been compromised, the proxy will generate a false sense of trust and forward the request to the server. As a result, the server generates false data that will be forwarded to users by proxies that have generated false sense of trust with it.
Vulnerability Scenario
Lisa has a private proxy that she uses to access data from her company. Lisa is concerned about the security of her proxy and decides to set up a firewall on the server that is connected to the proxy. The firewall will prevent any incoming connections. When Lisa logs into her account, she receives a message stating, "The login information you entered cannot be confirmed because it is already in use." Lisa looks into this message and sees that it has been sent by a third party. That person has compromised the trust relationship between Lisa's private proxy and its server.
Lisa visits the link given in the error message and sees an image of her company's logo with a red box around it with text saying, "This website was designed for you."
Overview:
How does the vulnerability work?
If an attacker is able to compromise the trust relationship between a proxy and a server, the attacker can send a crafted HTTP request header to the server which will cause the server to generate a false sense of trust. As a result, the server generates false data that the proxy will forward to the user. In this case, the proxy will display the false data of the server to the user. This will trick users into thinking that it is genuine when it is not.
Timeline
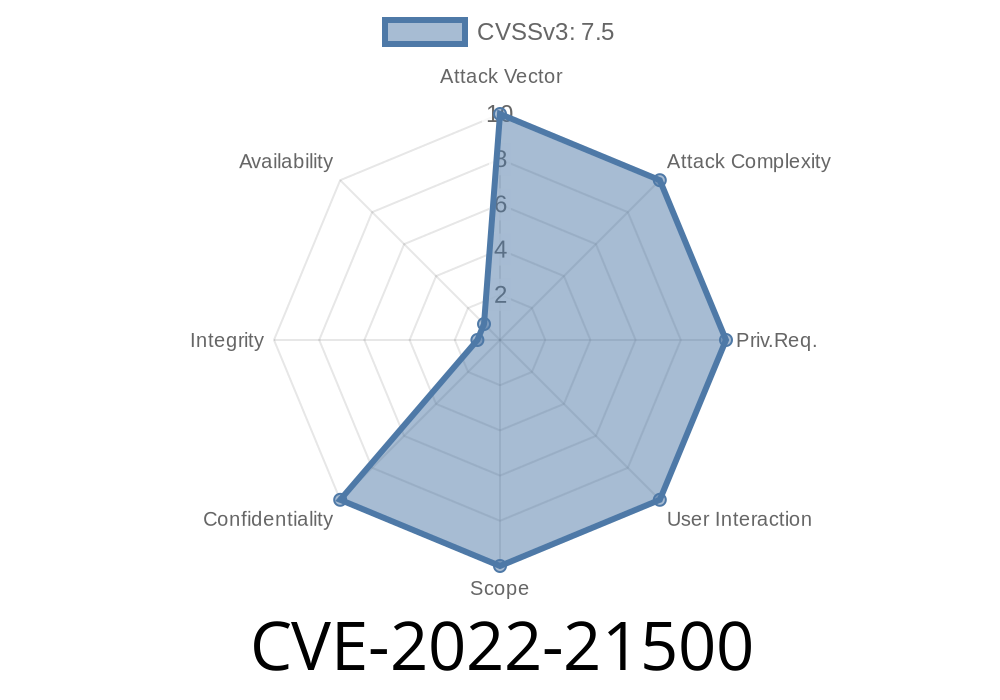
Published on: 05/20/2022 00:15:00 UTC
Last modified on: 07/19/2022 21:15:00 UTC