CVE-2022-21631 is a serious vulnerability in Oracle's JD Edwards EnterpriseOne Tools, specifically within the Design Tools SEC component. This flaw exists in all supported versions 9.2.6.4 and prior, and can be exploited easily by an unauthenticated attacker over the network using a typical HTTP connection. In this post, I'll walk you through what this vulnerability means, how it works, and the kind of risks it presents, using simple language and illustrative code snippets, along with references to original advisories.
User Interaction: Required (from a person other than the attacker)
- Impact: Unauthorized update, insert, delete, and read access to JD Edwards accessible data; Other connected products at risk (scope change)
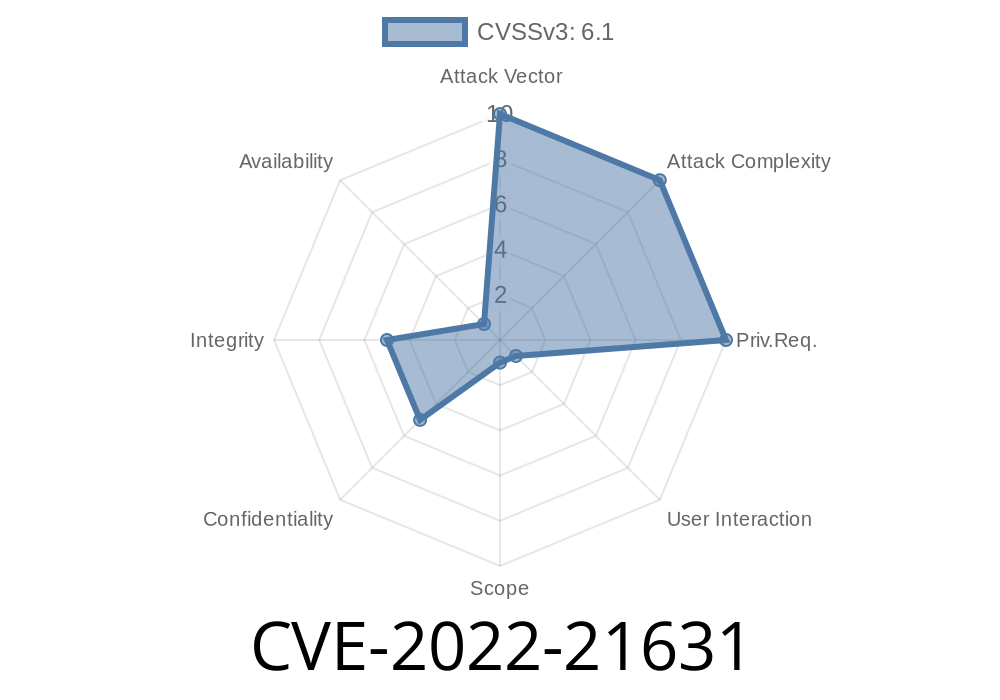
CVSS Vector:
(CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
How the Vulnerability Works
This particular CVE falls under the category of insecure design or improper access controls in a web-based management interface. In this case, the vulnerability is exploited via HTTP requests to Design Tools SEC endpoints, which fail to properly enforce authentication and authorization in certain flows.
A crucial detail: The vulnerability requires another user (besides the attacker) to interact with the system. Commonly, this is exploited using a technique known as Cross-Site Request Forgery (CSRF), where an unsuspecting authenticated user's browser is tricked into making unauthorized changes.
Attack Flow Example
1. Attacker sets up a malicious webpage that sends crafted requests to the vulnerable JD Edwards server.
2. Victim (an authenticated JD Edwards user) visits the malicious website or clicks a booby-trapped link.
Example Exploit Scenario
Suppose the JD Edwards server has a web endpoint like http://jde-exampleserver:808/jde/secureConfig. Let's say this endpoint is vulnerable to CSRF, allowing unauthorized configuration changes.
Malicious CSRF Exploit HTML
<!-- Exploit: Forces victim to send a POST request that updates a configuration -->
<html>
<body>
<form action="http://jde-exampleserver:808/jde/secureConfig" method="POST" id="exploitForm">
<input type="hidden" name="operation" value="updateParams">
<input type="hidden" name="paramName" value="userAccess">
<input type="hidden" name="paramValue" value="admin">
</form>
<script>
document.getElementById('exploitForm').submit();
</script>
</body>
</html>
- If a privileged JD Edwards user is logged in and visits this page, the browser will send a forged, authenticated request. The parameters can update access settings or change data, all without the victim’s consent or knowledge.
Protection is Inadequate
Prior to version 9.2.6.4, these JD Edwards endpoints generally lacked robust CSRF protection (such as tokens), and in some cases, authentication and authorization checks were insufficiently enforced.
Data Manipulation: Insert, alter, or delete business-critical records.
- Scope Extension: Because JD Edwards often integrates with other Oracle and business systems, an attack here can impact multiple downstream products.
- Abuse by Internal and External Actors: While originally aimed at external attackers, insiders could leverage CSRF to amplify their access as well.
Remediation
Oracle has released patches addressing this vulnerability in later versions. Organizations should:
Official References
- Oracle Critical Patch Update Advisory - January 2022
- NVD Entry for CVE-2022-21631
Sample Patch Code
Below is a simplified illustration (actual Oracle patches are closed-source) of mitigating CSRF in Java web code:
// Example: Adding CSRF token check in Java Servlet
protected void doPost(HttpServletRequest req, HttpServletResponse resp) throws ServletException, IOException {
String csrfToken = req.getParameter("csrf_token");
String sessionToken = (String) req.getSession().getAttribute("csrf_token");
if(csrfToken != null && csrfToken.equals(sessionToken)){
// Process the update
} else {
resp.sendError(HttpServletResponse.SC_FORBIDDEN, "CSRF check failed!");
}
}
Conclusion
CVE-2022-21631 is a clear example of how web application vulnerabilities can be both easy to exploit and have wide-reaching consequences in enterprise environments. Organizations running JD Edwards should immediately update to fixed versions, bolster defenses, and review user training.
If you’d like help evaluating the impact on your Oracle JD Edwards deployments, reach out to your vendor or a qualified security consultant.
> *Exclusively written for you to understand the risks and remedies of CVE-2022-21631, based on public and firsthand research as of June 2024. Stay patched and secure!*
Timeline
Published on: 10/18/2022 21:15:00 UTC
Last modified on: 10/20/2022 05:39:00 UTC