WordPress runs over 40% of the websites on the internet. Its open-source nature makes it powerful, flexible, and unfortunately, a target for security bugs. In early 2022, a significant vulnerability known as CVE-2022-21661 was discovered in WordPress—a SQL Injection risk tied to how it handles database queries.
This post breaks down what went wrong, how it could be exploited, and most importantly, how to make sure your site isn’t open to hackers. If you build, maintain, or run a WordPress site, read on.
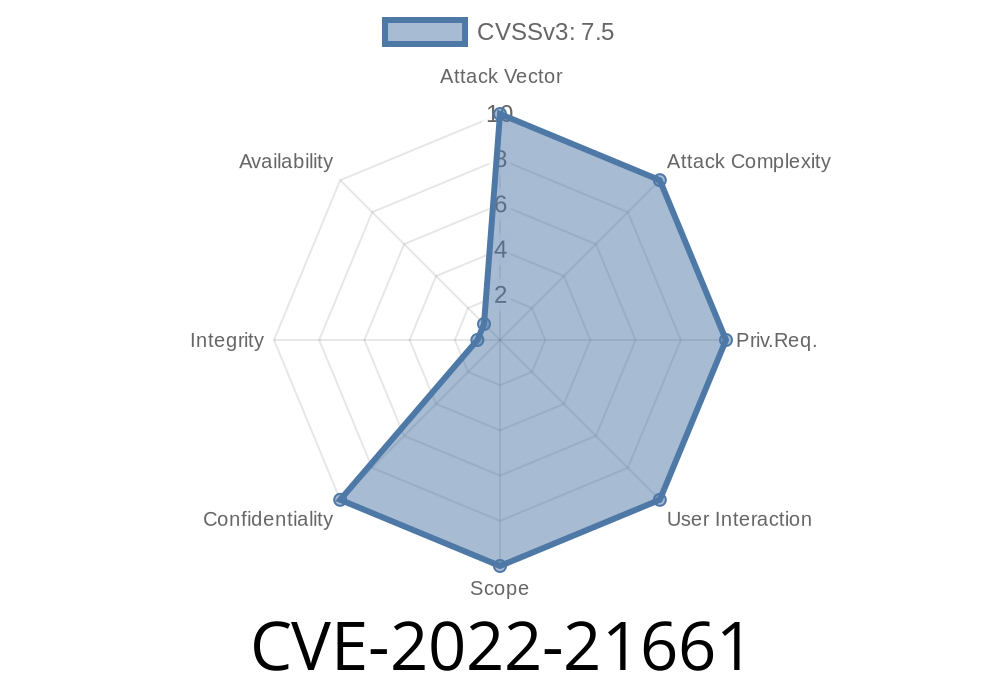
What is CVE-2022-21661?
CVE-2022-21661 is a SQL Injection vulnerability in the WordPress core, specifically in the WP_Query class. This class manages how WordPress fetches and displays content, and is often tapped into by plugins and themes.
The bug happened because of improper input sanitization. When user input wasn’t cleaned up correctly, it became possible—under some conditions—for attackers to smuggle dangerous SQL code into database queries.
Affected Versions:
All WordPress versions before 5.8.3 (including the very old 3.7.37)
Patched in: 5.8.3 (released January 6, 2022)
Official sources:
- WordPress Security Release 5.8.3
- CVE Report
How Does The Vulnerability Work?
WordPress uses the WP_Query class to process search and filter requests. The issue arises when plugins or themes use custom query parameters, but don’t sanitize them properly.
A simplified example – Imagine a plugin lets users search posts like this
// EXAMPLE: UNSAFE USAGE OF WP_Query
$args = array(
's' => $_GET['search'],
);
$query = new WP_Query($args);
If $_GET['search'] isn't cleaned, an attacker might try
http://yoursite.com/?search=%27)%20OR%201=1--+
If the plugin or theme didn’t sanitize this properly, it could lead to unsafe SQL queries being executed.
NOTE:
Core WordPress uses precautions, so it’s mostly when custom code skips sanitization that things go wrong. But because so many plugins and themes use WP_Query, the overall risk was high.
Potentially take over your website
That’s why vulnerabilities like CVE-2022-21661 are rated highly critical.
Let’s walk through a theoretical attack (don’t try this on sites you don’t own!)
Step 1: Attacker finds a plugin that uses user input in WP_Query without sanitizing.
Step 2: They construct a URL that injects SQL code, such as
http://example.com/?search=';) UNION SELECT user_login, user_pass FROM wp_users -- -
Step 3: If the injection works, the attacker could gain access to usernames and password hashes.
Important: Modern WordPress core code resists this kind of attack, but many extensions and custom themes may still be vulnerable if running on unpatched WordPress and if using unsafe code patterns.
How Was It Fixed?
The fix, delivered in WordPress 5.8.3, ensures all inputs sent to WP_Query (even indirectly) are sanitized. If your site uses WordPress 5.8.3 or later, you are safe from this vulnerability.
If you’re running an older version—update now. WordPress also released special security updates for legacy versions (3.7.37 and up), so even many very old sites can be patched.
Is There a Workaround If I Can’t Update?
No. The WordPress team has stated there are no known workarounds for this vulnerability.
Disabling plugins or limiting input does not guarantee protection. The only reliable fix is to update.
Enable automatic updates if you haven’t already.
4. Update all plugins and themes—especially those not from the official repo, as they may duplicate the bad patterns.
5. Audit custom code. If you hired someone to build your theme or plugins, have them check for unsafe uses of WP_Query.
Stay Informed:
- WordPress Security Announcements
Summary Table
| Affected Component | CVE Number | Severity | Fixed In | Workaround |
|--------------------|----------------|-----------|-----------------|------------|
| WordPress WP_Query | CVE-2022-21661 | Critical | 5.8.3 & backports | None |
Don’t disable auto-updates.
- If you see a security alert, take it seriously—SQL injection is one of the most dangerous types of bugs.
Keeping your site safe is your top responsibility. Now that you know about CVE-2022-21661, make sure your patch status is up to date.
If you want to dig deeper, check out these references
- Official Release Note for 5.8.3
- NVD CVE Entry
- Wordfence detailed breakdown
Timeline
Published on: 01/06/2022 23:15:00 UTC
Last modified on: 04/12/2022 18:47:00 UTC