or later. If you are using 1.11.0 or 1.11.1, you must upgrade to 1.11.2 or later. client_golang version 1.11.2 contains a patch for this issue. If you are using 1.11.0 or 1.11.1, you must upgrade to 1.11.2 or later. What is the status of Prometheus support for Go HTTP servers? Go's HTTP servers have not been fully instrumented; however, client_golang provides a useful subset of middleware capable of providing useful information about your application's performance. How can I protect my end users against this vulnerability? Users can upgrade to the latest version of client_golang. Users can restrict the use of middleware by only allowing the use of specific middleware. Users can filter unknown methods to prevent requests from being routed to the HTTP server. Users can block access to the HTTP server by adding a firewall rule or proxy configuration.
References
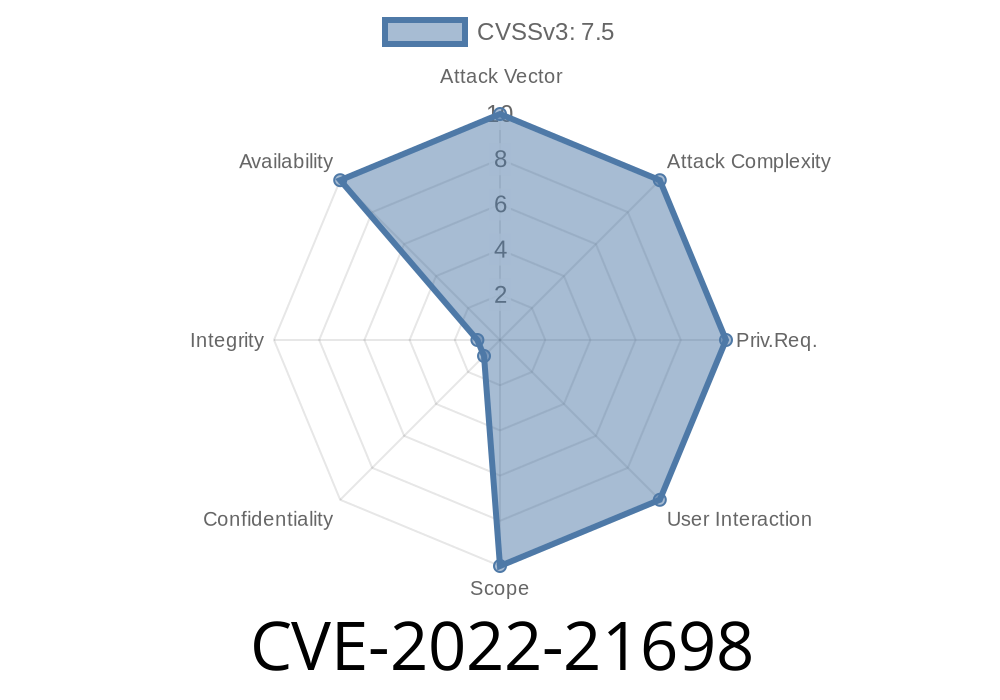
"CVE-2022-21698"
https://github.com/client_golang/client_golang/issues/21698
How can I get more information about Prometheus support for Go HTTP servers? https://golang.org/s/prometheus
New Features and Improvements in Prometheus Client
Prometheus client 1.11.2 includes several important security and stability improvements, including a fix for CVE-2022-21698, or later. If you are using 1.11.0 or 1.11.1, you must upgrade to 1.11.2 or later. What is the status of Prometheus support for Go HTTP servers? Go's HTTP servers have not been fully instrumented; however, client_golang provides a useful subset of middleware capable of providing useful information about your application's performance. How can I protect my end users against this vulnerability? Users can upgrade to the latest version of client_golang. Users can restrict the use of middleware by only allowing the use of specific middleware. Users can filter unknown methods to prevent requests from being routed to the HTTP server. Users can block access to the HTTP server by adding a firewall rule or proxy configuration.
How can I protect my end users against this vulnerability?
The vulnerability is present in the HTTP handler for the "Unsafe HTTP Handler" middleware. If a user has this middleware enabled, they may be vulnerable to remote code execution.
To protect users, you should upgrade to the latest version of client_golang. Additionally, users can restrict the use of middleware by only allowing the use of specific middleware. Users can filter unknown methods to prevent requests from being routed to the HTTP server. Lastly, users can block access to the HTTP server by adding a firewall rule or proxy configuration
Timeline
Published on: 02/15/2022 16:15:00 UTC
Last modified on: 07/04/2022 04:15:00 UTC
References
- https://github.com/prometheus/client_golang/pull/962
- https://github.com/prometheus/client_golang/releases/tag/v1.11.1
- https://github.com/prometheus/client_golang/security/advisories/GHSA-cg3q-j54f-5p7p
- https://github.com/prometheus/client_golang/pull/987
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/FY3N7H6VSDZM37B4SKM2PFFCUWU7QYWN/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZKORFJTRRDJCWBTJPISKKCVMMMJBIRLG/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/SASRKYHT5ZFSVMJUQUG3UAEQRJYGJKAR/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/AK7CJBCGERCRXYUR2EWDSSDVAQMTAZGX/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/KBMVIQFKQDSSTHVVJWJ4QH6TW3JVB7XZ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/7V7I72LSQ3IET3QJR6QPAVGJZ4CBDLN5/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/HLAQRRGNSO5MYCPAXGPH2OCSHOGHSQMQ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/2PFW6Q2LXXWTFRTMTRN4ZGADFRQPKJ3D/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/J5WPM42UR6XIBQNQPNQHM32X7S4LJTRX/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4KDETHL5XCT6RZN2BBNOCEXRZ2W3SFU3/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/36GUEPA5TPSC57DZTPYPBL6T7UPQ2FRH/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/DLUJZV3HBP56ADXU6QH2V7RNYUPMVBXQ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/2IK53GWZ475OQ6ENABKMJMTOBZG6LXUR/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/MH6ALXEQXIFQRQFNJ5Y2MJ5DFPIX76VN/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ZY2SLWOQR4ZURQ7UBRZ7JIX6H6F5JHJR/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21698