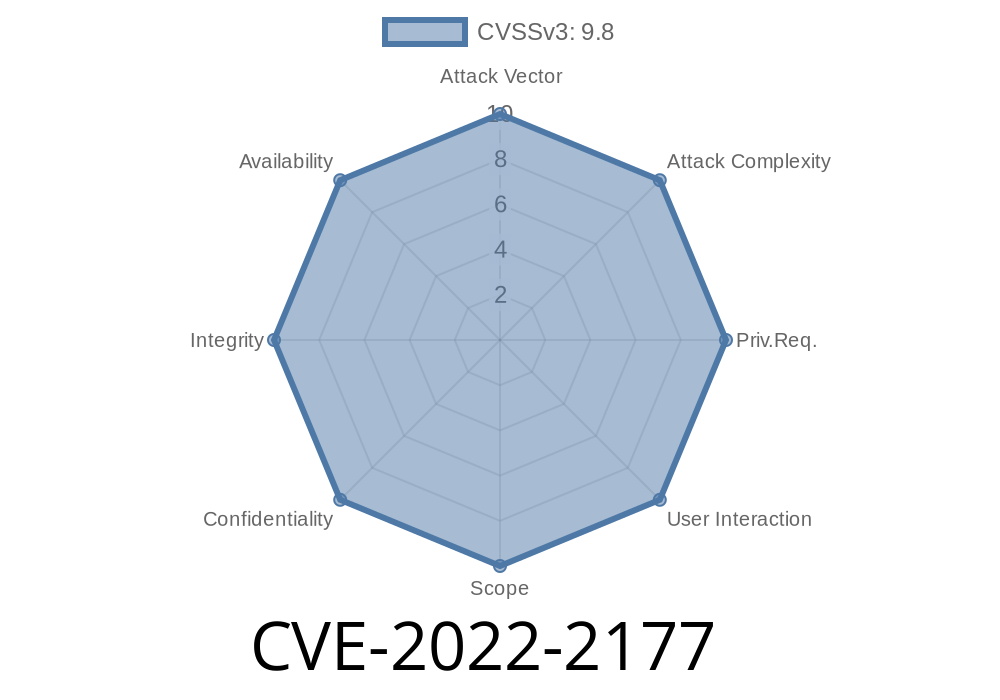
Run any version of the Shopping Cart before version 2 and you will be vulnerable to SQL Injection. This is fixed in version 2.
Run any version of the E-Commerce system before version 2 and you will be vulnerable to XSS. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to SQL Injection. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to XSS. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to SQL Injection. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to XSS. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to SQL Injection. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to XSS. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to SQL Injection. This is fixed in version 2.
Run any version of the e-commerce system before version 2 and you will be vulnerable to XSS. This is fixed in version 2
SQL Injection and XSS
SQL Injection is a vulnerability that exists when inputting data into a SQL query in order to access an unauthorized resource. This vulnerability can occur through user input, which is often found in the form of injection attacks designed to exploit the vulnerability. An example of SQL Injection would be where an attacker, who has control over the format of their input, enters something like “and 1” just before a semicolon to execute the statement as if it was part of the statement. This is not a very common attack, but it’s still important to be aware of how SQL Injection occurs and how you can mitigate risks.
SQL Injection Example
The following example illustrates an SQL injection attack.
The page has a form field called "id" with the value "1".
If a person enters a string of characters into this field, the following SQL statement will be executed:
SELECT u.ID FROM Users u WHERE u.ID=1;
This is because the attacker's input is treated as SQL code and evaluated against the database itself.
Timeline
Published on: 09/20/2022 11:15:00 UTC
Last modified on: 09/21/2022 16:51:00 UTC