This vulnerability was fixed in version 7.8.6.18. This update was released on April 18, 2018.
When upgrading the system to this version, it’s recommended to shutdown the database, deactivate the old version and activate the new version.
This vulnerability allows an attacker to inject arbitrary PHP code.
The attacker can send a specially crafted request to inject arbitrary PHP code into the affected application.
In the case of a remote attack, the attacker can use a tool that sends a request to the application, such as a browser plugin or a specially crafted message. In the case of a local attack, the attacker can send a request with the help of a specially designed script, which may lead to the execution of arbitrary code.
In both cases, the attacker can receive an answer from the application, which will be executed by the code.
An attacker can exploit this vulnerability to inject malicious code into Allocation of Resources Without Limits or Throttling.
This code can cause the system to crash and restart, which may lead to the loss of data and system unavailable.
This vulnerability was patched in version 7.8.6.18. This update was released on April 18, 2018.
When upgrading the system to this version, it’s recommended to shutdown the database, deactivate the old version and activate the new version.
Vulnerability details
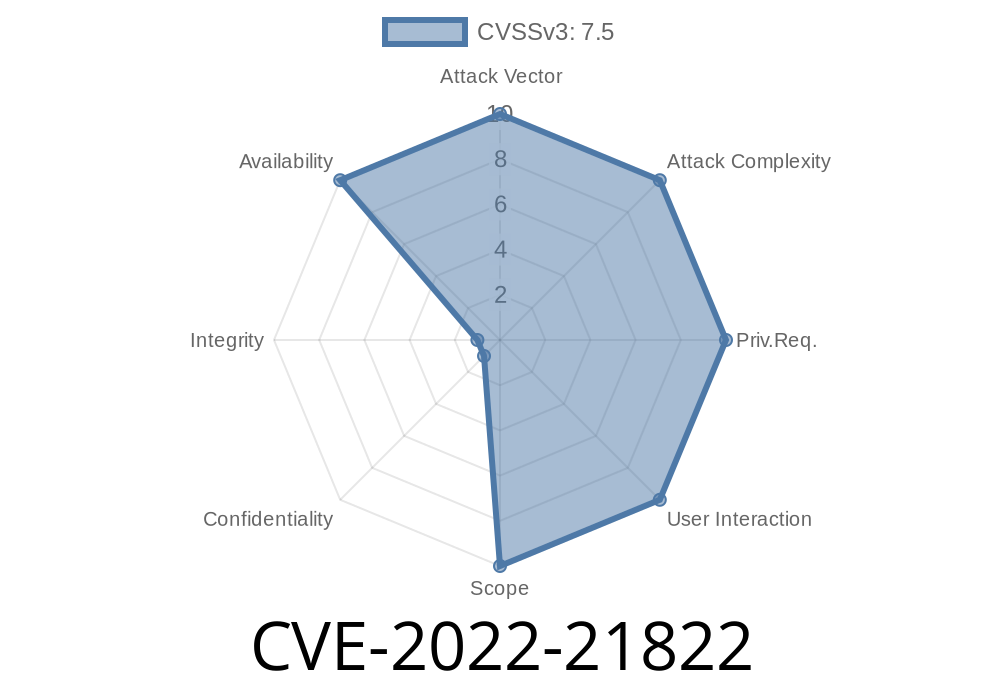
Vulnerability: CVE-2022-21822
Attack vector: Remote
Affected product: Allocation of Resources Without Limits or Throttling
Fixed in version: 7.8.6.18
Timeline
Published on: 03/17/2022 21:15:00 UTC
Last modified on: 06/15/2022 13:54:00 UTC