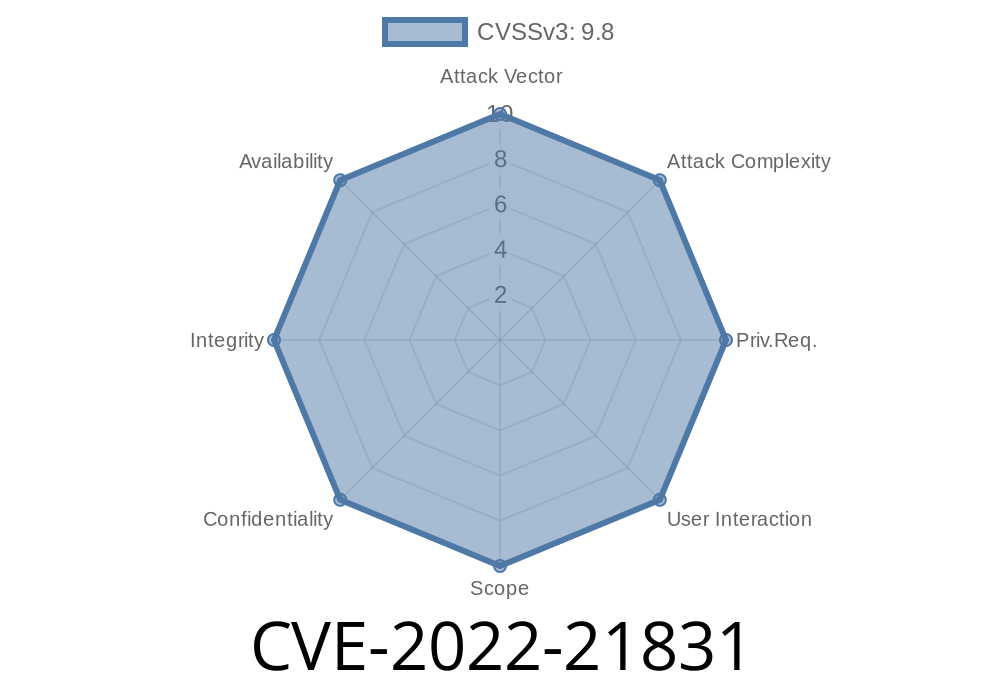
An attacker would need to inject malicious code into Active Storage via image_processing arguments to exploit this vulnerability. Active Storage is an image processing plugin that allows a user to upload images to WordPress sites, enable image styles, and create image galleries. An attacker would need to submit a maliciously crafted image_processing argument to a user via a website to leverage the code injection vulnerability. When a user visits the website and subsequently clicks the “Add to Active Storage” button, the code injection occurs, which then allows the attacker to run arbitrary code on the server. The code injection occurs because the Active Storage plugin does not validate image_processing arguments, which allows attackers to inject malicious code into the WordPress site and execute it in the context of the website. There are no known workarounds at this time.
Vulnerability Details
An attacker would need to inject malicious code into Active Storage via image_processing arguments to exploit this vulnerability. Active Storage is an image processing plugin that allows a user to upload images to WordPress sites, enable image styles, and create image galleries. An attacker would need to submit a maliciously crafted image_processing argument to a user via a website to leverage the code injection vulnerability. When a user visits the website and subsequently clicks the “Add to Active Storage” button, the code injection occurs, which then allows the attacker to run arbitrary code on the server. The code injection occurs because the Active Storage plugin does not validate image_processing arguments, which allows attackers to inject malicious code into the WordPress site and execute it in the context of the website. There are no known workarounds at this time.
Vulnerability Discovery
The vulnerability was discovered by the research team of Trend Micro.
Vulnerability Finding Tips
If you're going to find vulnerabilities like this, it is important to remember that WordPress typically has a large number of plugins. It's easy to miss one that contains vulnerabilities like this if you don't know where to look for them. If you do find a plugin like this, the best way to identify its flaws is by using the plugin in question and making changes in browser developer tools. Eventually, you'll see the attack surface in XHR requests, which will tell you what information can be manipulated and what values can be sent via AJAX. The following code shows how an attacker might exploit a vulnerable plugin:
if (window.location && window.location == 'http://www.target-site') {
document.write(JSON.stringify({"name":"MyPlugin"}));
} else {
document.write('
Timeline
Published on: 05/26/2022 17:15:00 UTC
Last modified on: 06/07/2022 14:57:00 UTC