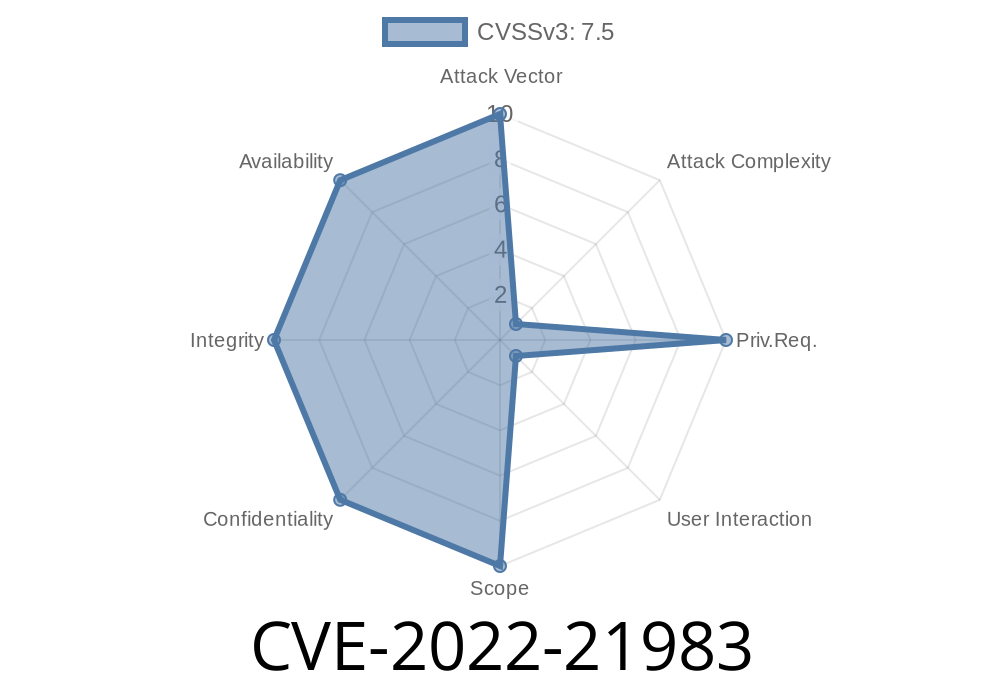
This CVE ID was originally reported to BID. The core reason for this vulnerability is that some XMPP clients use the libxml parser for parsing XMPP messages. libxml is an open source library for parsing XML data. By sending specially crafted XMPP messages, an attacker can exploit this vulnerability to execute arbitrary code on the targeted system. This may lead to remote code execution in the context of the user running the targeted application. At the time of this writing, there’s no publicly available exploit code for this vulnerability. However, this may change in future as more information becomes available.
Windows and OS X XMPP Client Vulnerabilities
The vulnerability was reported to the vendor, and they are currently working on a patch. If you’re running an XMPP client on Windows or OS X, you should be safe from this attack. This vulnerability doesn’t exist in any other clients.
Mitigation Strategies
The best way to mitigate this vulnerability is to use an XMPP client that uses an updated libxml.
At the time of this writing, no patches have been released for any affected applications.
You can also scan your system for vulnerable applications and patch them as soon as possible.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/21/2022 20:40:00 UTC