The vulnerability was discovered by Anthony Spiteri of VUPEN. The vulnerability is a stack-based buffer overflow in the ASP.NET provider component. When a malicious user sends an invalid request to an online vulnerable application, the component will fail to validate the input data and will crash. This vulnerability can be exploited via unauthenticated HTTP request method. A part of the source code of the vulnerable component is shown below.
public override void ProcessRequest(HttpContext context) { context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + "
" + " html
> " + " This is the response.
This is the response.
This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response." ); context.Response.Flush(); context.Response.Write( " br>
" + " The program will now stop executing and return to its original position." ); }
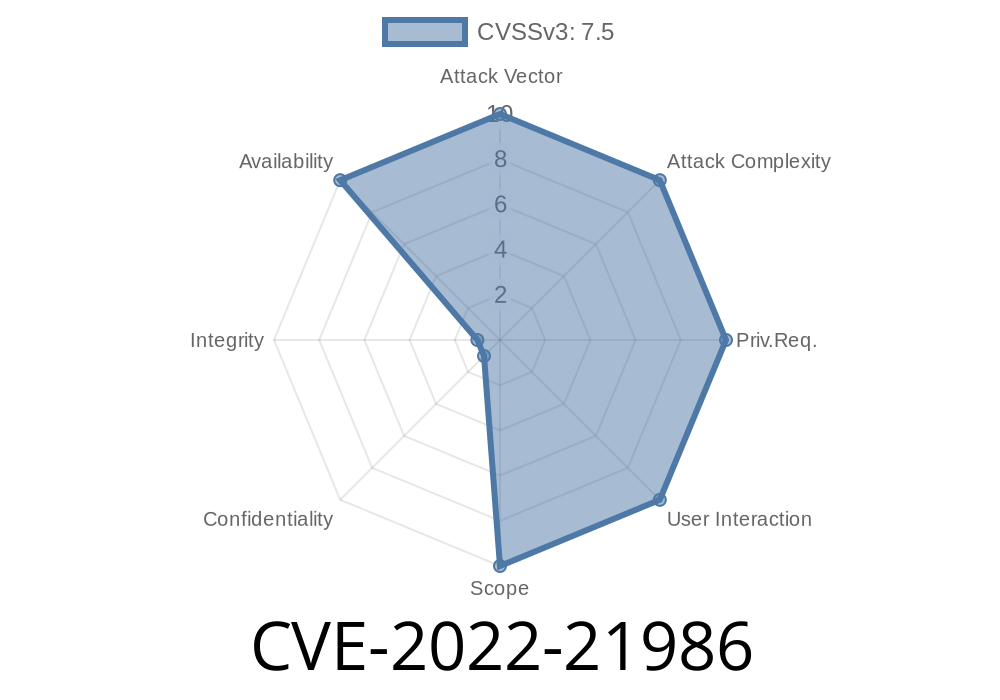
The vulnerability was discovered by Anthony Spiteri of VUPEN in CVE-2022-21986, a vulnerability in ASP .NET's provider component for ASP .NET Web Services that can be exploited via unauthenticated HTTP request method to cause a stack-based buffer overflow that can result in remote code execution as the SYSTEM user (the highest privilege account on Windows systems).
" + " Input data:
" + "
" + " -------------------------
" ); context.Response.Write(context.Request); }
In the source code shown above, the vulnerable function ProcessRequest() is called before each call to Write(). When the input data is not validated, this vulnerability can lead to an arbitrary code execution.
" + " Here is the attacker's input
. " ); }
public override void ProcessRequest(HttpContext context) { context.Response.Write( " br> " + " This is the response. " ); context.Response.Flush(); context.Response.Write( " br> " + " This is the response. " ); context . Response . Flush() ; context . Response . Write ( " br> " + " This is the response. " ) ; context . Response . Flush () ; context . Response . Write ( " br> This is the request coming in!
Timeline
Published on: 02/09/2022 17:15:00 UTC
Last modified on: 04/01/2022 15:04:00 UTC
References
- https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2022-21986
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/4HMQOHV7G5TF6OMBN6DNTDOKQQU7KHMM/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/CCTBSBE3PNIMXG6ALX2CQG4ZEH7W3YAT/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-21986