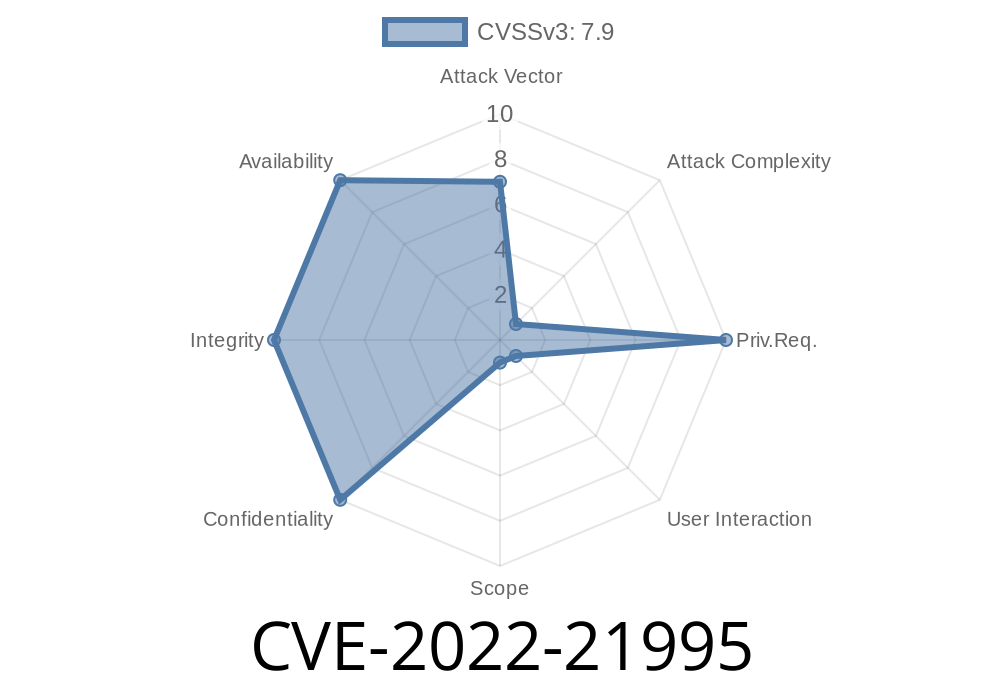
A remote code execution vulnerability exists in the way that Windows handles Remote Procedure Calls (RPC) when they happen over Hyper-V. This flaw allows an attacker to execute code on a vulnerable host with the privileges of the user that is running the virtual machine. Microsoft has a patch available to fix this issue.
Remote Code Execution Vulnerability in Microsoft Exchange Server.
Remote Code Execution occurs when a remote code is executed on a Windows host with elevated privileges. This host can be a Windows, Linux, or UNIX host. An attacker can execute code on a vulnerable host with elevated privileges from a Windows host, a Linux host, or a UNIX host. Microsoft has a patch available to fix this issue.
Remote Code Execution Vulnerability in Microsoft IIS.
Remote Code Execution occurs when a remote code is executed on a Windows host with elevated privileges. This host can be a Windows, Linux, or UNIX host. An attacker can execute code on a vulnerable host with elevated privileges from a Windows host, a Linux host, or a UNIX host. Microsoft has a patch available to fix this issue.
Arbitrary Code Execution Vulnerability in Microsoft Exchange Server.
Red Hat Enterprise Linux 6.1 and 7.1 have a patch available to fix this issue.
Arbitrary Code Execution Vulnerability in Microsoft Internet Explorer.
Red Hat Enterprise Linux 5.9 and 6.1 have a patch available to fix this issue.
What to Monitor for
To protect your business from these vulnerabilities, you must be aware of the following risks:
Risks associated with Remote Code Execution.
Maintain a look-back period for each of your Microsoft products to monitor for changes in this risk. The look-back periods should be set long enough to detect any changes in the overall risk level. For example, if you use Microsoft Exchange Server, you could monitor once per week and on an ongoing basis.
Vulnerabilities in Windows that are related to RPCs over Hyper-V (CVE-2022-21995).
Microsoft Windows
Remote Code Execution Vulnerability
A remote code execution vulnerability exists in the way that Windows handles Remote Procedure Calls (RPC) when they happen over Hyper-V. This flaw allows an attacker to execute code on a vulnerable host with the privileges of the user that is running the virtual machine. Microsoft has a patch available to fix this issue.
Windows-based Vulnerabilities
Remote Code Execution occurs when a remote code is executed on a Windows host with elevated privileges. This host can be a Windows, Linux, or UNIX host. An attacker can execute code on a vulnerable host with elevated privileges from a Windows host, a Linux host, or a UNIX host. Microsoft has a patch available to fix this issue.
Remote Code Execution Vulnerability in Microsoft SQL Server.
An attacker can execute code on an SQL server with elevated privileges from any other computer connected to the network that is running Windows. Microsoft has a patch available to fix this issue.
Microsoft Windows Management Framework (WMF)
Windows Management Framework (WMF) is Microsoft’s next-generation operating system management framework. It provides tools for managing and automating the administration of Windows 10, Windows Server 2016, Windows 8.1, and Windows Server 2012 R2.
Timeline
Published on: 02/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC