This vulnerability is due to a input validation error in the handling of VHDX files. An attacker could exploit this to execute arbitrary code in the context of the Hyper-V host. Microsoft released updates for Windows Server 2016, Windows 10, Windows Server 2019, and Windows Server 1803 to resolve this issue. After installing the update, you should create new VHDX files with a different name. CVE-2022 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible. How to protect yourself: - Use strong passwords. - Don’t open suspicious emails or click on links in them. - Keep your software up to date. - If possible, use a virtual machine to run critical applications. - If possible, isolate sensitive data to prevent any data leakage. - Don’t install applications from untrusted sources.
Microsoft Windows – CVE-2023 -22008
This vulnerability is due to a input validation error in the handling of VHDX files. An attacker could exploit this to execute arbitrary code in the context of the Hyper-V host. Microsoft released updates for Windows Server 2016, Windows 10, Windows Server 2019, and Windows Server 1803 to resolve this issue. After installing the update, you should create new VHDX files with a different name. CVE-2023 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible. How to protect yourself: - Use strong passwords. - Don’t open suspicious emails or click on links in them. - Keep your software up to date. - If possible, use a virtual machine to run critical applications. - If possible, isolate sensitive data to prevent any data leakage.
Microsoft Windows Hyper-V CVE-2096
This vulnerability is due to a memory corruption issue in the handling of VHDX files. An attacker could exploit this to execute arbitrary code in the context of the Hyper-V host. Microsoft released updates for Windows Server 2016, Windows 10, Windows Server 2019, and Windows Server 1803 to resolve this issue. After installing the update, you should create new VHDX files with a different name. CVE-2096 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible. How to protect yourself: - Use strong passwords. - Don’t open suspicious emails or click on links in them. - Keep your software up to date. - If possible, use a virtual machine to run critical applications
Windows 10 - CVE-2021 -22007
This vulnerability is due to a input validation error in the handling of VHDX files. An attacker could exploit this to execute arbitrary code in the context of the Hyper-V host. Microsoft released updates for Windows Server 2016, Windows 10, Windows Server 2019, and Windows Server 1803 to resolve this issue. After installing the update, you should create new VHDX files with a different name. CVE-2021 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible. How to protect yourself: - Use strong passwords. - Don’t open suspicious emails or click on links in them. - Keep your software up to date. - If possible, use a virtual machine to run critical applications. - If possible, isolate sensitive data to prevent any data leakage. - Don’t install applications from untrusted sources
Microsoft released updates to patch Hyper-V vulnerability
Microsoft released patches to fix a vulnerability in Windows 10, Windows Server 2016, Windows Server 2019, and Windows Server 1803. This vulnerability is due to an input validation error in the handling of VHDX files. An attacker could exploit this to execute arbitrary code on the Hyper-V host. After installing the updates, you should create new VHDX files with a different name. CVE-2022 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible.
Hyper-V CVE ID
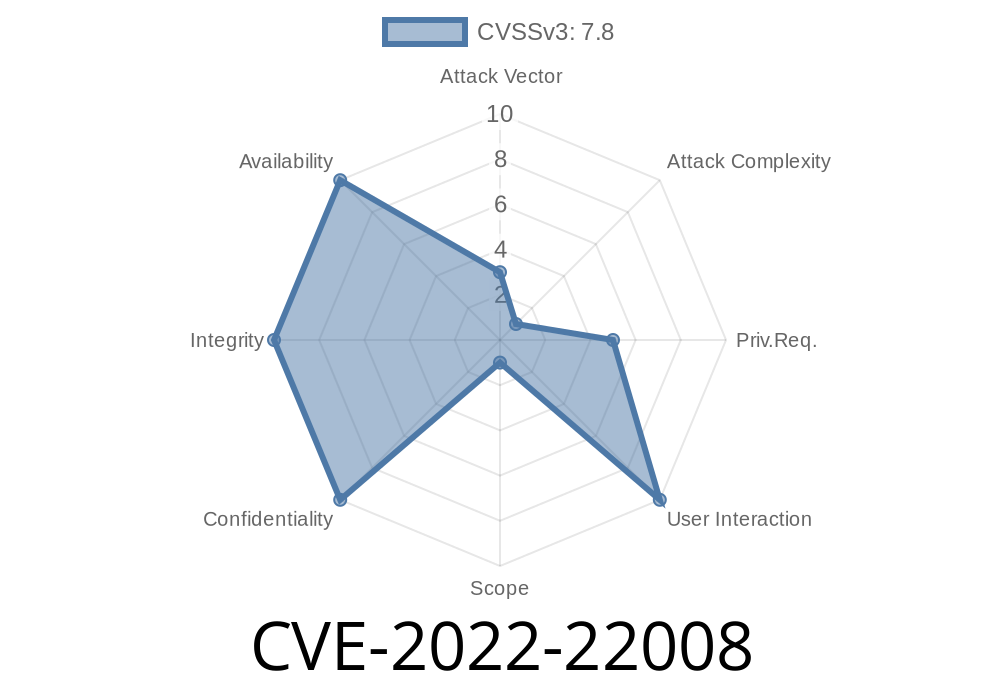
CVE-2022-22008 is a vulnerability that affects Hyper-V. An attacker could exploit this to execute arbitrary code in the context of the Hyper-V host. Microsoft released updates for Windows Server 2016, Windows 10, Windows Server 2019, and Windows Server 1803 to resolve this issue. After installing the update, you should create new VHDX files with a different name. CVE-2022 is one of the most critical vulnerabilities in Windows 10. It is critical because it allows an attacker to execute code remotely on the Hyper-V host. An attacker could then install a malicious application or launch a phishing attack to gain access to data. Microsoft released security updates to patch this vulnerability. You should install these updates as soon as possible.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 05/26/2022 16:40:00 UTC