This vulnerability allows an attacker to perform a privilege-escalation attack. Attackers can exploit this vulnerability to access privileged functions of the Web server software. By using a specially crafted request, an attacker can exploit this vulnerability to execute code on the target system.
This vulnerability is currently being exploited in the wild. Once an attacker has successfully exploited this vulnerability, the attacker can conduct Man-in-the-Middle attacks and steal sensitive information.
To exploit this vulnerability, an attacker must be able to issue a request to the Web server software. The request must be sent to the server software, and the server software must process the request.
The Web server software that is vulnerable to this vulnerability is Windows. Windows Web server software that is vulnerable to this vulnerability is Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, and Windows Server 2012.
Details about how to exploit this vulnerability are available in the Microsoft advisory. End users can protect themselves from exploitation of this vulnerability by installing this security update. In addition, administrators can protect network users from exploitation of this vulnerability by using user authentication.
Impact of Public Exploits: There are currently no public exploits available for this vulnerability
Vulnerability Scoring
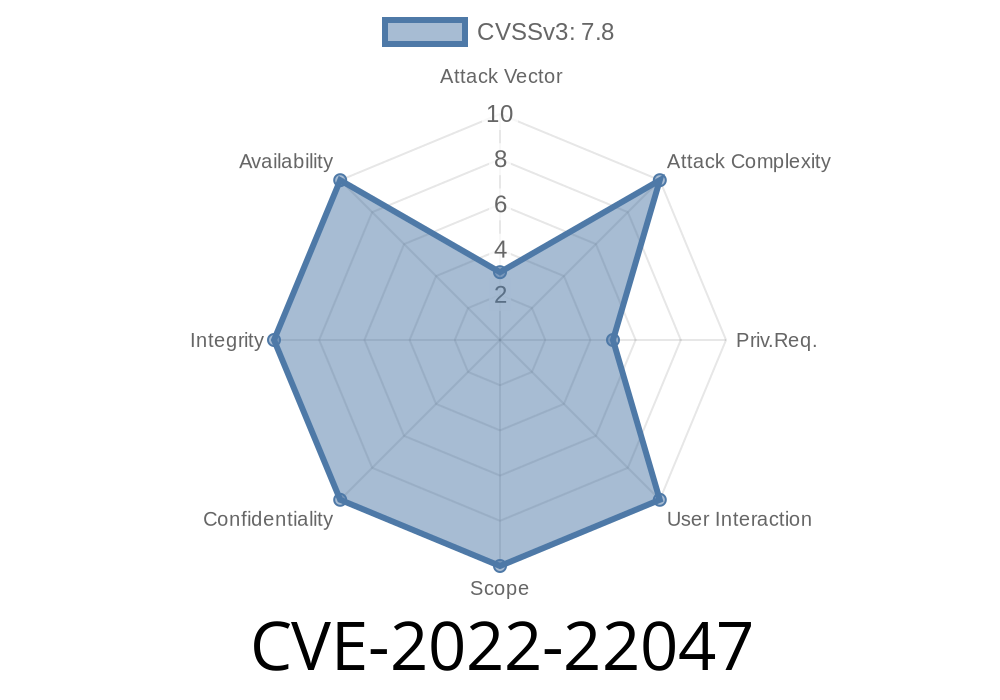
This vulnerability has a medium severity.
For more information on how to score vulnerabilities, please see the Vulnerability Scoring document.
Microsoft Windows Server 2003 CVE-2022-22048
This vulnerability allows an attacker to perform a privilege-escalation attack. Attackers can exploit this vulnerability to access privileged functions of the Web server software. By using a specially crafted request, an attacker can exploit this vulnerability to execute code on the target system.
This vulnerability is currently being exploited in the wild. Once an attacker has successfully exploited this vulnerability, the attacker can conduct Man-in-the-Middle attacks and steal sensitive information.
To exploit this vulnerability, an attacker must be able to issue a request to the Web server software. The request must be sent to the server software, and the server software must process the request.
The Web server software that is vulnerable to this vulnerability is Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, and Windows Server 2012.
Details about how to exploit this vulnerability are available in the Microsoft advisory. End users can protect themselves from exploitation of this vulnerability by installing this security update. In addition, administrators can protect network users from exploitation of this vulnerability by using user authentication.
Impact of Public Exploits: There are currently no public exploits available for this vulnerability
Microsoft Windows Server Update Services Vulnerability CVE-2022-22047
This vulnerability allows an attacker to perform a privilege-escalation attack. Attackers can exploit this vulnerability to access privileged functions of the Web server software. By using a specially crafted request, an attacker can exploit this vulnerability to execute code on the target system.
Details about how to exploit this vulnerability are available in the Microsoft advisory. End users can protect themselves from exploitation of this vulnerability by installing this security update. In addition, administrators can protect network users from exploitation of this vulnerability by using user authentication.
Impact of Public Exploits: There are currently no public exploits available for this vulnerability
Microsoft Windows Server Update Services (WSUS)
The vulnerability is also addressed by an update released on April 5, 2013. "Microsoft has released security updates to address the vulnerability."
WSUS is a Windows Server Update Services (WSUS) deployment tool that provides network administrators with tools to deploy and configure Microsoft updates across multiple computers. WSUS 3.0 service packs are available for users running WSUS 2.0 SP2 or later versions of the WSUS server. The WSUS client can download these updates from either a local installation of WSUS or from the Microsoft update servers.
Timeline
Published on: 07/12/2022 23:15:00 UTC
Last modified on: 07/16/2022 13:50:00 UTC