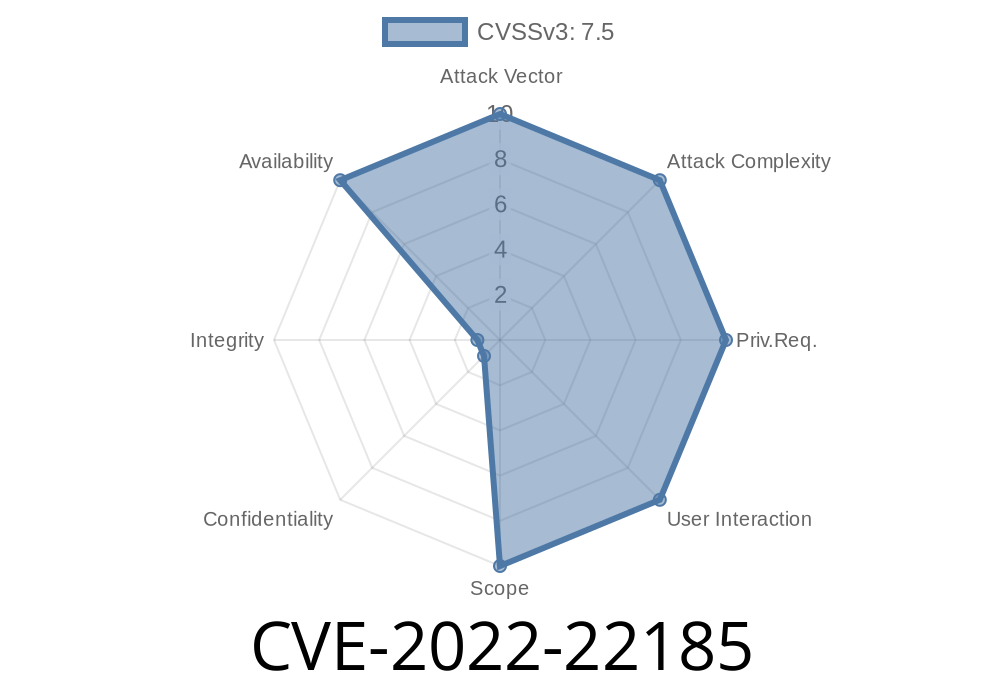
This issue is commonly exploited in the following scenario: - In the production environment, where 'preserve-incoming-fragment-size' feature is enabled - When the device receives the specific fragmented packet - The device processes the packet and responds with specific ICMP type 8 and code 1 - The attacker continues sending the specific fragmented packet to the device, causing a sustained DoS condition - An attacker can exploit this vulnerability to cause a sustained DoS condition by sending a specific fragmented packet to the device. End users should be aware of this vulnerability and apply appropriate mitigations to reduce the risk of exploitation. Vulnerable versions: Juniper Networks Junos OS on SRX Series: 18.3 versions prior to 18.3R3-S6; 18.4 versions prior to 18.4R3-S10; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R3-S4; 19.3 versions prior to 19.3R3-S4; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R3-S2; 20.2 versions prior to 20.2R3-S3; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R3; 21.1 versions prior to 21.1R2-S1,
Affected Software
Juniper Networks Junos OS on SRX Series: 18.3 versions prior to 18.3R3-S6; 18.4 versions prior to 18.4R3-S10; 19.1 versions prior to 19.1R3-S7; 19.2 versions prior to 19.2R3-S4; 19.3 versions prior to 19.3R3-S4; 19.4 versions prior to 19.4R3-S6; 20.1 versions prior to 20.1R3-S2; 20.2 versions prior to 20.2R3-S3; 20.3 versions prior to 20.3R3-S1; 20.4 versions prior to 20.4R3
Vulnerability details
An attacker can exploit this vulnerability to cause a sustained DoS condition by sending a specific fragmented packet to the device. This issue is commonly exploited in the following scenario: - In the production environment, where 'preserve-incoming-fragment-size' feature is enabled - When the device receives the specific fragmented packet - The device processes the packet and responds with specific ICMP type 8 and code 1 - The attacker continues sending the specific fragmented packet to the device, causing a sustained DoS condition
End users should be aware of this vulnerability and apply appropriate mitigations to reduce the risk of exploitation.
Vulnerable Scenario
An attacker can exploit this vulnerability to cause a sustained DoS condition by sending a specific fragmented packet to the device. End users should be aware of this vulnerability and apply appropriate mitigations to reduce the risk of exploitation.
End users should apply the following mitigation: - Ensure that 'preserve-incoming-fragment-size' feature is disabled in production environments, which will reduce the likelihood of an attacker exploiting this vulnerability.
Timeline
Published on: 04/14/2022 16:15:00 UTC
Last modified on: 04/21/2022 14:38:00 UTC