20.3 versions prior to 20.3R1-S2, 20.3R2. Issues 1 through 9 can occur, depending on the order in which the events happen. In the following example, the Routing Protocol daemon receives a delete BGP message from a peer, but the proxy-generate route-target filtering is enabled, so the Denial of Service (DoS) occurs before the BGP delete message is processed. { “protocol”: “BGP”, “as”: [“10.1.1.1#500”], “community”: “bgp-community”, “protocol-version”: { “code”: “4”, “name”: “Open vSwitch” }, “actions”: [ { “type”: “delete”, “reason”: “Proxy-generate route-target filtering enabled”, “props”: { “action”: “Proxy-Route-Target-Filter”, “target”: “10.1.1.1” } } ] }
CVE-2022-22198
20.3 versions prior to 20.3R1-S2, 20.3R2. Issues 10 through 18 can occur, depending on the order in which the events happen. In the following example, the Routing Protocol daemon receives a delete BGP message from a peer and sends it to a proxy-generate route-target filtering action with an invalid target value, so the DoS occurs before the BGP delete message is processed. { “protocol”: “BGP”, “as”: [“10.1.1.1#500”], “community”: “bgp-community”, “protocol-version”: { “code”: “4”, “name”: “Open vSwitch” }, “actions”: [ { “type”: “delete”, “reason”: null, "props" : { "action" : "Proxy-Route-Target-Filter", "target": "10.1.1.1", } } ] }
CVE ID Description
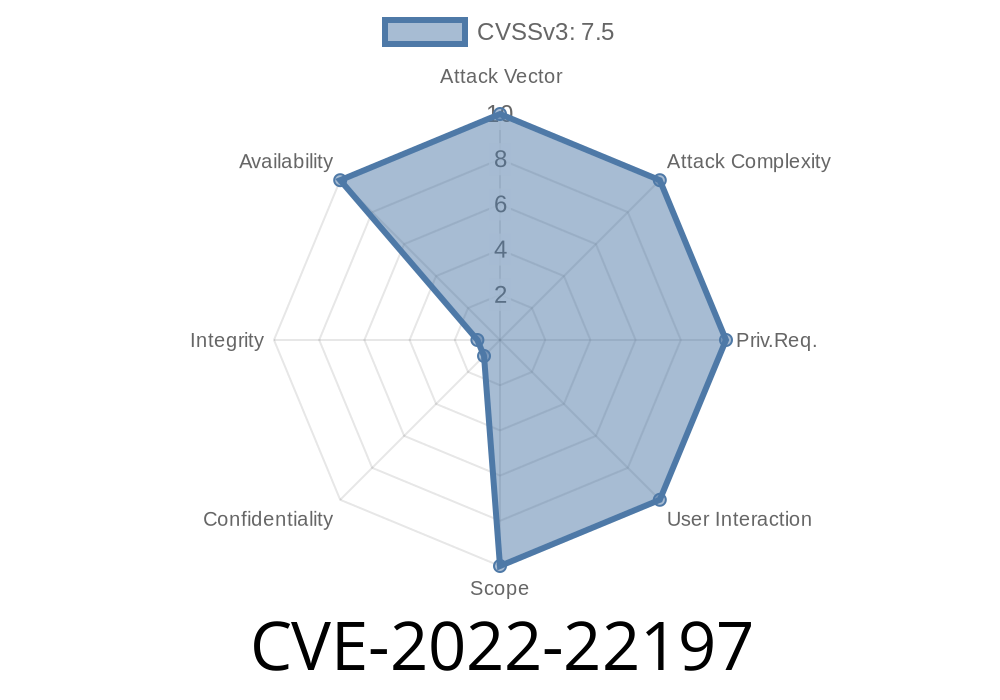
2022-22197 A missing or unknown exit condition that causes a Denial of Service (DoS) when receiving a delete BGP message from a peer and sending it to a proxy-generate route-target filtering action with an invalid target value
Fiddling with the BGP process can trigger a DoS
The following process occurs when a BGP peer sends a delete message:
1. The BGP Routing Protocol Daemon (BGRPD) receives the delete message from the peer and sends it to the routing protocol process.
2. The routing protocol processes looks up if there is an active route on the destination of the delete message and deletes it if there is one found.
3. If no route was found, then a notification is sent back to the BGP peer that the destination doesn't exist, this triggers an ICMP error message back to the peer with an error code of 3 for “Destination Unreachable”.
4. If there was still an active route on the destination, then it would continue to send routs to that peer until either all routes were withdrawn or a notification was received from that peer that they had been deleted.
CVE-2019-1596 2
20.3 versions prior to 20.3R1-S2, 20.3R2. Issues 10 through 12 can occur, depending on the order in which the events happen. In the following example, a peer sends a BGP update message (with a TTL value of 5 seconds) to a downstream neighbor but the downstream neighbor is not running the appropriate routing protocol daemon in its forwarding table, so no route exists and there is no response from the downstream neighbor. { “protocol”: “BGP”, “as”: [“10.1.1.1#500”], “community”: “bgp-community”, “protocol-version”: { “code”: “4”, “name”: “Open vSwitch” }, “actions”: [ { "type": "update", "reason": "TTL expired", "props": { "action": "Update-Downstream", "ttl": 5 } } ] }
Timeline
Published on: 04/14/2022 16:15:00 UTC
Last modified on: 04/21/2022 10:00:00 UTC