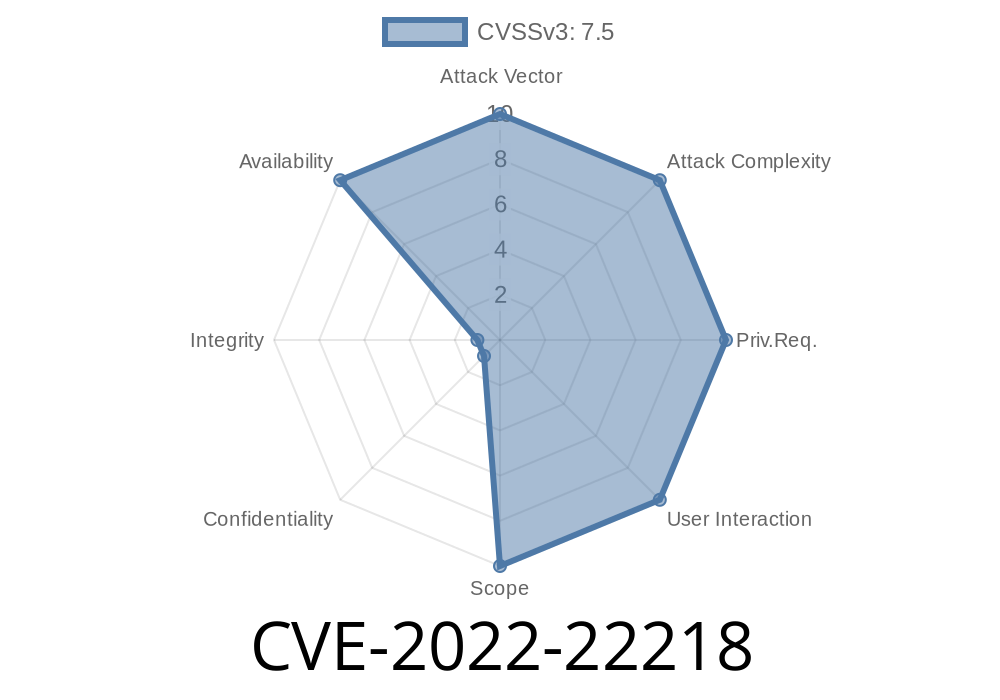
This issue was discovered by Jann Horn of Google’s Project Zero. This can be exploited remotely if the access to the affected device is allowed. Access to a device that is using auto re-enrollment can be exploited remotely. Cisco devices have a predefined Access Control List (ACL) that restricts a user from accessing certain devices. This can be exploited remotely to gain access to the affected device. To exploit this issue, an attacker must be on the same network as the device with the vulnerable software. This issue can be exploited remotely if the affected device has vulnerable software and if the attacker has remote access. On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA) server, leading to crash. A restart is required to restore services. This issue affects: On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA
Summary
This issue was discovered by Jann Horn of Google’s Project Zero. This can be exploited remotely if the access to the affected device is allowed. Access to a device that is using auto re-enrollment can be exploited remotely. Cisco devices have a predefined Access Control List (ACL) that restricts a user from accessing certain devices. This can be exploited remotely to gain access to the affected device. To exploit this issue, an attacker must be on the same network as the device with the vulnerable software. This issue can be exploited remotely if the affected device has vulnerable software and if the attacker has remote access.
Vulnerability Characteristics
This issue affects: On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA) server, leading to crash. A restart is required to restore services. This issue can be exploited remotely if the affected device has vulnerable software and if the attacker has remote access.
On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA) server, leading to crash. A restart is required to restore services.
How does this vulnerability occur?
If the certificate has expired, the device will issue a warning message to the user and then re-issue the certificate. If this is a trusted CA certificate, no further action is taken. Otherwise, a new certifcate is generated in CMA but this time it contains an invalid signature. The actual certifcate expires soon after and is deleted from memory.
Products Affected
Cisco Firepower Threat Defense (FTD)
Cisco Adaptive Security Appliance (ASA)
Cisco Network Admission Control (NAC)
Cisco Asa9211
Cisco ICX 6500
Cisco ASR 900 Series ____END__ ____END__
Description
On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA) server, leading to crash. A restart is required to restore services.
This issue affects: On SRX Series devices, an Improper Check for Unusual or Exceptional Conditions when using Certificate Management Protocol Version 2 (CMPv2) auto re-enrollment, allows a network-based, unauthenticated attacker to cause a Denial of Service (DoS) by crashing the pkid process. The pkid process cannot handle an unexpected response from the Certificate Authority (CA) server, leading to crash. A restart is required to restore services.
Timeline
Published on: 10/18/2022 03:15:00 UTC