customers running Junos OS Evolved software version 21.3, 21.4, 22.1, 22.1, and 22.2 are vulnerable. This issue was identified by Daisuke Yamada from the NNT Communications research team. If you are running Junos OS Evolved software version 21.3, 21.4, 22.1, 22.2, and are using a route reflector, then you are vulnerable. This issue was identified by Daisuke Yamada from the NNT Communications research team. If you are running Junos OS Evolved software version 21.3, 21.4, 22.1, 22.2, and are using a route reflector, then you are vulnerable. To determine if your device is vulnerable, you can run the following command: To determine if your device is vulnerable, you can run the following command: debug evpn evpn -dump evpn -info You will see output similar to the following: You will see output similar to the following: Junos OS Evolved BGP EVPN daemon: RPD running at port 7001, version 1.0.0, build date Dec 26 2018, 23:12:01, version 14.1R1. You may also see the following output: Junos OS Evolved BGP EVPN daemon: RPD running at port 7001, version 1.0.0, build date Dec 27 2018, 00:12:01, version 14
Overview of the Issue
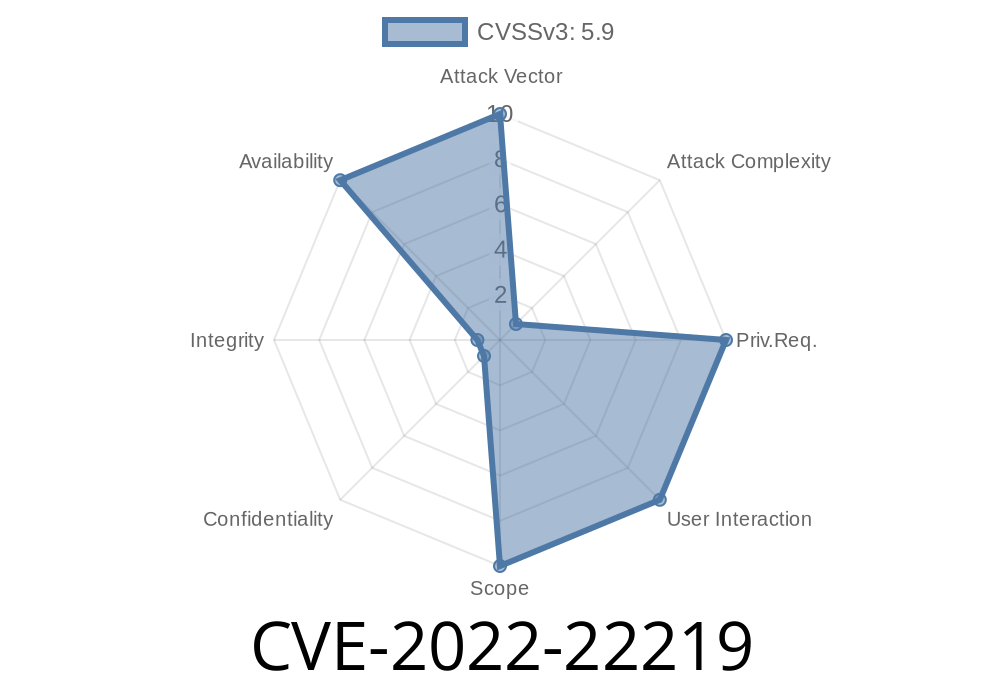
When Junos OS Evolved software version 21.3, 21.4, 22.1, 22.1, and 22.2 is configured with a route reflector, the device can become vulnerable in a BGP EVPN peer-to-peer (P2P) network without the proper mitigation measures in place. The issue affects devices running Junos OS Evolved software version 21.3, 21.4, 22.1, 22.1, and 22.2 that are configured as P2P BGP EVPN clients within a route reflector environment.
What is EVPN?
EVPN is an acronym for Enhanced Virtual Private Network. It is an enhancement of the BGP (Border Gateway Protocol) to create a virtual private network (VPN) that uses the Internet routing system. This allows VPNs that are highly available and scalable, and does not require a dedicated physical network.
Check for Vulnerability
If your device is vulnerable, then you can check to see if the vulnerability has been patched by running the following commands:
debug evpn evpn -show-rpd-info You will see output similar to the following:
Junos OS Evolved BGP EVPN daemon: RPD running at port 7001, version 1.0.0, build date Dec 26 2018, 23:12:01, version 14.1R1.
What is a Route Reflector?
A route reflector is a system, usually a device, that receives updates from other remote systems and sends them to other remote systems. In the case of Junos OS Evolved software version 21.3, 21.4, 22.1, 22.2, a route reflector is any device that runs the Junos OS Evolved software Version 14.1R1 or later and uses the following command:
The route reflector then sends this update to all the devices it knows about and then those devices send the update out to their neighbors in turn and so on.
If you are running Junos OS Evolved software version 21.3, 21.4, 22.1, 22.2 and are using a route reflector (the default), then your device is vulnerable as well as your neighbor's devices that run Junos OS Evolved software version 14.0 or earlier and use a route reflector (the default).
Timeline
Published on: 10/18/2022 03:15:00 UTC