21.2R3-S3; 21.3-EVO versions prior to 21.3R2-S1; 21.4-EVO versions prior to 21.4R1-S1; 22.1-EVO versions prior to 22.1R1-S2; 22.2-EVO versions prior to 22.2R1-S1. Vulnerable installations If rpd does crash, then rpd restart command can be used to restart the daemon. Cisco products Cisco products are not vulnerable to this issue. Cisco has issued no warnings for this issue. Mitigation If you are running a version of Junos OS earlier than Junos OS 19.2R3-S6, upgrade to a supported version or apply an appropriate workaround. Juniper Networks releases a new version of rpd with every new release of the software. For more information on how to update your rpd daemon, see the rpd daemon documentation.
RPD CVE Details
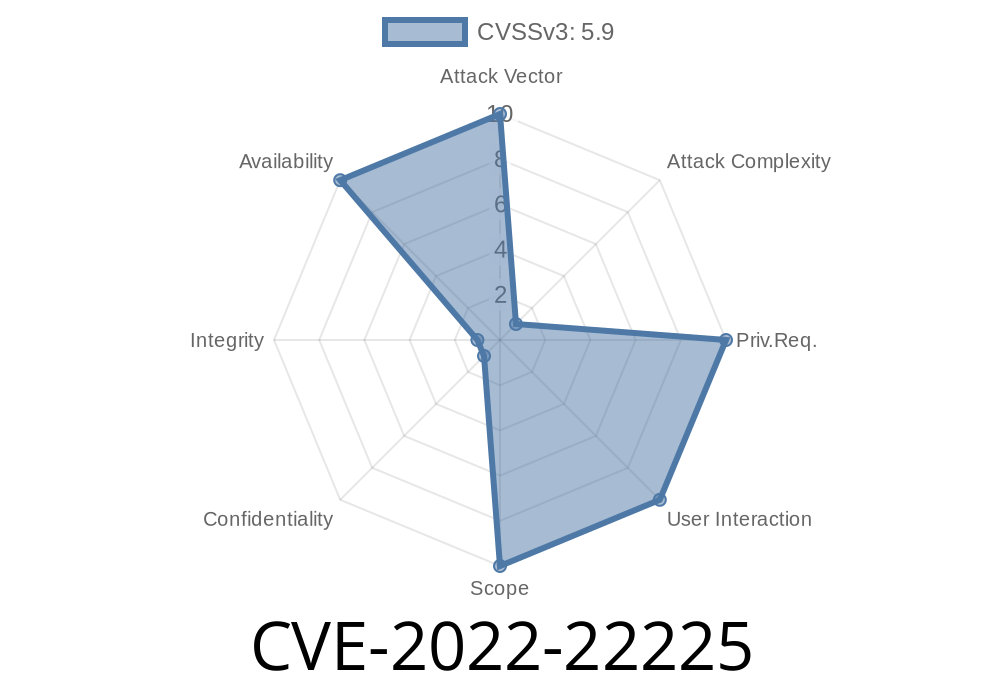
CVE-2022-22225 is a vulnerability in the Junos OS that allows an attacker to cause a denial of service (DoS) condition on an affected device. If rpd crashes, then rpd restart command can be used to restart the daemon.
Cisco products Cisco products are not vulnerable to this issue. Cisco has issued no warnings for this issue.
Mitigation If you are running a version of Junos OS earlier than Junos OS 19.2R3-S6, upgrade to a supported version or apply an appropriate workaround.
Software Description:
Junos OS, Junos OS software, Junos OS Software Release Notes
References
Cisco Systems - Confirmed Cisco Products are not vulnerable to CVE-2022-22225
Juniper Networks - Confirmed Junos OS releases a new version of rpd with every new release of the software.
Junos OS 19.2R3-S6: Fixed in Junos OS 19.2R3-S6, later releases are not vulnerable
References:
- CVE-2022-22225
- Juniper Networks
SCOPE AND RESULTS OF THE VULNERABILITY
The vulnerability allows an unauthenticated attacker to crash the router daemon (rpd) on a vulnerable device. Impact The vulnerability allows an unauthenticated attacker to crash the router daemon (rpd) on a vulnerable device. This causes the rpd daemon not to be able to start and the router does not restart successfully. Mitigation Unauthenticated attackers can use this vulnerability to cause rpd daemon not to be able to start and the router does not restart successfully by sending a malformed packet to port 3389.
Timeline
Published on: 10/18/2022 03:15:00 UTC