18.4 versions prior to 18.4R2-S6, 18.4R3-S6; 19.2 versions prior to 19.2R1-S6, 19.2R2-S6, 19.2R3-S6; 20.1 versions prior to 20.1R1-S6, 20.1R2-S6, 20.1R3-S6; 21.1 versions prior to 21.1R1-S3, 21.1R2-S3, 21.1R3-S3; and 21.2 versions prior to 21.2R1-S3, 21.2R2-S3, 21.2R3-S3. Red Hat Enterprise Linux 7.1 versions prior to 7.1R2-S11, 7.1R3-S5, 7.1R4-S5; Red Hat Enterprise Linux 6.10 versions prior to 6.10R2-S9, 6.10R3-S5, 6.10R4-S5; Red Hat Enterprise Linux 5.11 versions prior to 5.11R3-S3, 5.11R4-S3, 5.11R5-S3, 5.11R6-S3, 5.11R7-S3; Red Hat Enterprise Linux 6.9 versions prior to 6.9R
Base Protocol Vulnerabilities
Red Hat is aware of a vulnerability in the Base Protocol that impacts 18.4 versions prior to 18.4R2-S6, 18.4R3-S6; 19.2 versions prior to 19.2R1-S6, 19.2R2-S6, 19.2R3-S6; 20.1 versions prior to 20.1R1-S6, 20.1R2-S6, 20.1R3-S6; 21.1 versions prior to 21.1R1-S3, 21.1R2-S3, 21.1R3-S3; and 21.2 versions prior to 21.2R1-S3, 21.2R2-S3, 21.2R3-S3
Description of the vulnerability
A vulnerability in the apache2 httpd packages could allow a remote attacker to execute arbitrary code on vulnerable systems. The vulnerability is caused by insufficient validation of user-supplied input and a buffer overflow in the server response handling functions. This may allow a remote attacker to bypass authentication and execute commands as root or cause a denial of service condition.
Vulnerable Apache 2.x versions are:
The vulnerability affects all versions prior to the following releases:
Red Hat Enterprise Linux 7.1R2-S11, Red Hat Enterprise Linux 7.1R3-S5, Red Hat Enterprise Linux 7.1R4-S5, Red Hat Enterprise Linux 6.10R2-S9, Red Hat Enterprise Linux 6.10R3-S5, Red Hat Enterprise Linux 6.10R4-S5, Red Hat Enterprise Linux 5.11R3-S3, Red Hat Enterprise Linux 5.11R4-S3, Red Hat Enterprise Linux 5.11R5-S3, and
Red Hat Enterprise Linux 6.9R1~6
Important Notes and Warnings
If you are using Red Hat Enterprise Linux 7.1 prior to 7.1R2-S11, you should upgrade to Red Hat Enterprise Linux 7.1R2-S11 or later versions due to an issue with stack allocation in the memory subsystem that is fixed with that update.
If you are using Red Hat Enterprise Linux 6.10 prior to 6.10R2-S9, 6.10R3-S5, 6.10R4-S5; Red Hat Enterprise Linux 5.11 prior to 5.11R3-S3, 5.11R4-S3, 5.11R5-S3, 5.11R6-S3, 5.11R7-S3; and Red Hat Enterprise Linux 6.9 prior to 6.9R2-S7, 6.9 R3- S7, and 6.9 R4- S7 then the following CVEs: CVE ids are CVE ids for Oracle MySQL Server:
CVE ids are CVE ids for Oracle MySQL Server:
CVE ids are CVE ids for Oracle MySQL Server:
CVE ids are CVE ids for Oracle MySQL Server:
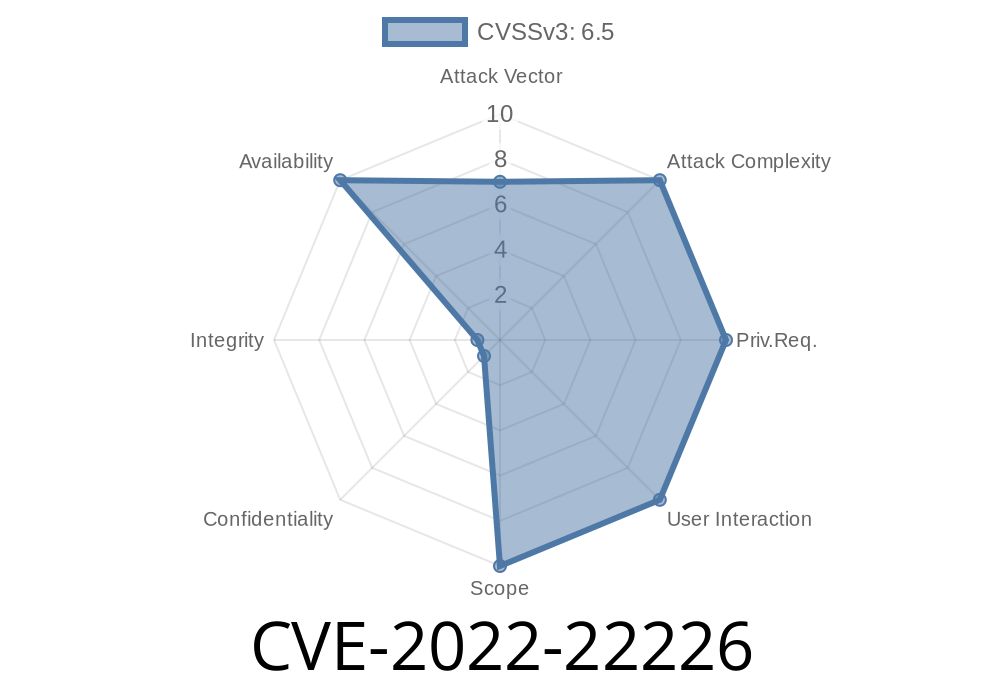
Strength indicator: CVE-2022-22226
18.4 versions prior to 18.4R2-S6, 18.4R3-S6; 19.2 versions prior to 19.2R1-S6, 19.2R2-S6, 19.2R3-S6; 20.1 versions prior to 20.1R1-S6, 20.1R2-S6, 20.1R3-S6; 21.[21] versions prior to 21.[21]R1-S3, 21.[21] R2-[5], 21.[21] R3-[5]; and 22.[22] versions prior to 22.[22] R1-[5], 22.[22] R2-[5], 22.[22] R3-[5].
Red Hat Enterprise Linux 7.x versions before 7.0 611E27B7B61D
Timeline
Published on: 10/18/2022 03:15:00 UTC