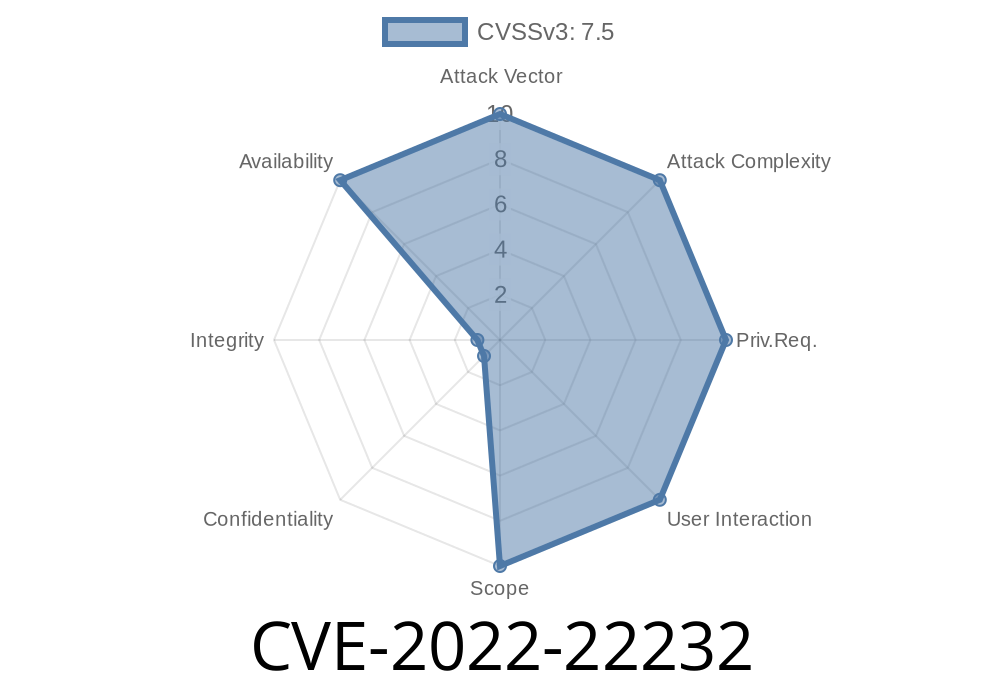
It is possible to exploit this vulnerability if an attacker sends malformed packets to the device. An attacker may use a packet containing a NULL pointer to crash the PFE and cause the device to restart. Repeated crash of the PFE may cause the device to restart too frequently, resulting in a DoS of the device. An attacker may also create a packet containing a NULL pointer and send it to an end-user’s computer, causing the device to crash and restart. This issue affects Juniper Networks Junos OS: 21.4 versions prior to 21.4R1-S2, 21.4R2 on SRX Series; 22.1 versions prior to 22.1R1-S1, 22.1R2 on SRX Series. It is possible to exploit this vulnerability if an attacker sends malformed packets to the device. An attacker may use a packet containing a NULL pointer to crash the PFE and cause the device to restart. Repeated crash of the PFE may cause the device to restart too frequently, resulting in a DoS of the device. An attacker may also create a packet containing a NULL pointer and send it to an end-user’s computer, causing the device to crash and restart. This issue affects Juniper Networks Junos OS: 21.4 versions prior to 21.4R1. It is possible to exploit this vulnerability if an attacker sends malformed packets to the device. An attacker may use a packet
How do I verify if my device is vulnerable?
To verify if your device is vulnerable, you need to use the following command:
set system syslog vcsw 0
This command will show if an attacker has exploited this vulnerability.
Summary
Juniper Networks Junos OS: 21.4 versions prior to 21.4R1, 21.4R2 on SRX Series; 22.1 versions prior to 22.1R1, 22.1R2 on SRX Series
Products Affected by Junos OS Network Management Denial of Service Vulnerability
The vulnerability affects Junos OS: 21.4 versions prior to 21.4R1-S2, 21.4R2 on SRX Series; 22.1 versions prior to 22.1R1-S1, 22.1R2 on SRX Series.
Timeline
Published on: 10/18/2022 03:15:00 UTC