Affected products If you are running Junos OS on any of the affected devices, you should upgrade to a fixed version. Juniper recommends the following actions to protect your device from this vulnerability: Upgrade to a fixed version of Junos OS from Cisco.com or from the software upgrade page on the device.
Upgrade to a fixed version of Junos OS from Cisco.com or from the software upgrade page on the device.
Disable SIP traffic on the device.
Restrict access to the device by disabling unnecessary services.
Restrict access to the device by disabling unnecessary services.
Change the SIP password.
Change the SIP password.
Disable unnecessary services.
Disable unnecessary services.
Apply the FortiCAN policy to the device.
Apply the FortiCAN policy to the device.
Disable SIP on the device.
Disable SIP on the device.
Disable the media feature on the device.
Disable the media feature on the device.
Disable unnecessary services.
Disable unnecessary services.
Disable unnecessary services.
Disable unnecessary services.
This issue was resolved in Junos OS version 16.1 X46.1. SRX1400 - SIP Remote Code Execution Vulnerability An Access of Uninitialized Pointer vulnerability in SIP Application Layer Gateway (ALG) of Juniper Networks Junos OS on SRX Series and MX Series allows
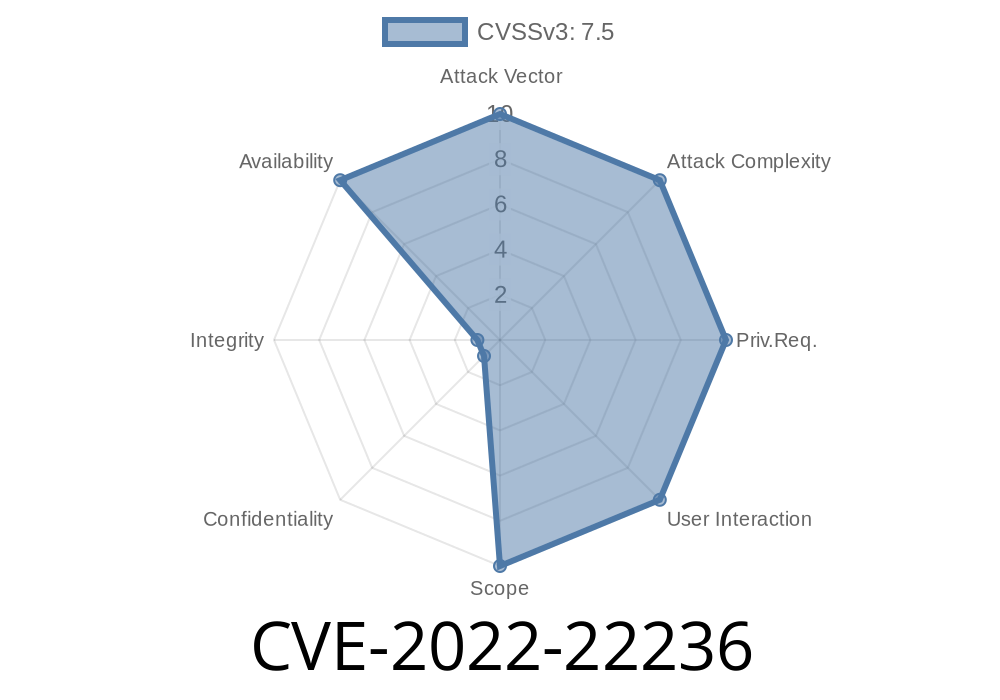
Description
Affected products If you are running Junos OS on any of the affected devices, you should upgrade to a fixed version. Juniper recommends the following actions to protect your device from this vulnerability: Upgrade to a fixed version of Junos OS from Cisco.com or from the software upgrade page on the device.
Upgrade to a fixed version of Junos OS from Cisco.com or from the software upgrade page on the device.
Disable SIP traffic on the device.
Restrict access to the device by disabling unnecessary services.
Change the SIP password.
Disable unnecessary services.
Apply the FortiCAN policy to the device.
Apply the FortiCAN policy to the device.
Disable SIP on the device.
Summary of the vulnerability
An Access of Uninitialized Pointer vulnerability in SIP Application Layer Gateway (ALG) of Juniper Networks Junos OS on SRX Series and MX Series allows remote attackers to execute arbitrary code on a vulnerable device. This issue was resolved in Junos OS version 16.1 X46.1.
Timeline
Published on: 10/18/2022 03:15:00 UTC