On some devices, the Management Daemon running on the device provides ssh access to a user with a low privilege level. Due to this, a locally authenticated attacker with low privileges and access to the ssh operational command can escalate their privileges to root. The attacker can do this by ssh’ing to a user with low privilege level, such as bin or sys. This can be done via Telnet, SSH, or through another protocol. An attacker can then use the root privilege to install a malicious SSH server on the device. A malicious SSH server can then be used to bypass security restrictions on the device or to further escalate privileges. If user interaction was required to install the malicious SSH server, then a locally authenticated attacker can potentially escalate their privileges to root, or if there is user interaction on the device to potentially escalate privileges on a remote system to root.
CVE-2021-22238
On some devices, the Management Daemon running on the device provides ssh access to a user with a low privilege level. Due to this, a locally authenticated attacker with low privileges and access to the ssh operational command can escalate their privileges to root. The attacker can do this by ssh’ing to a user with low privilege level, such as bin or sys. This can be done via Telnet, SSH, or through another protocol. An attacker can then use the root privilege to install a malicious SSH server on the device. A malicious SSH server can then be used to bypass security restrictions on the device or to further escalate privileges. If user interaction was required to install the malicious SSH server, then a locally authenticated attacker can potentially escalate their privileges to root, or if there is user interaction on the device to potentially escalate privileges on a remote system to root.
##angler fish
There are many ways to ensure the security of your device. One way is by using a firewall that prevents unauthorized access to the system. This is one way to protect the device from malicious intrusion. Another way is by ensuring that users with low privilege level cannot escalate their privileges to root.
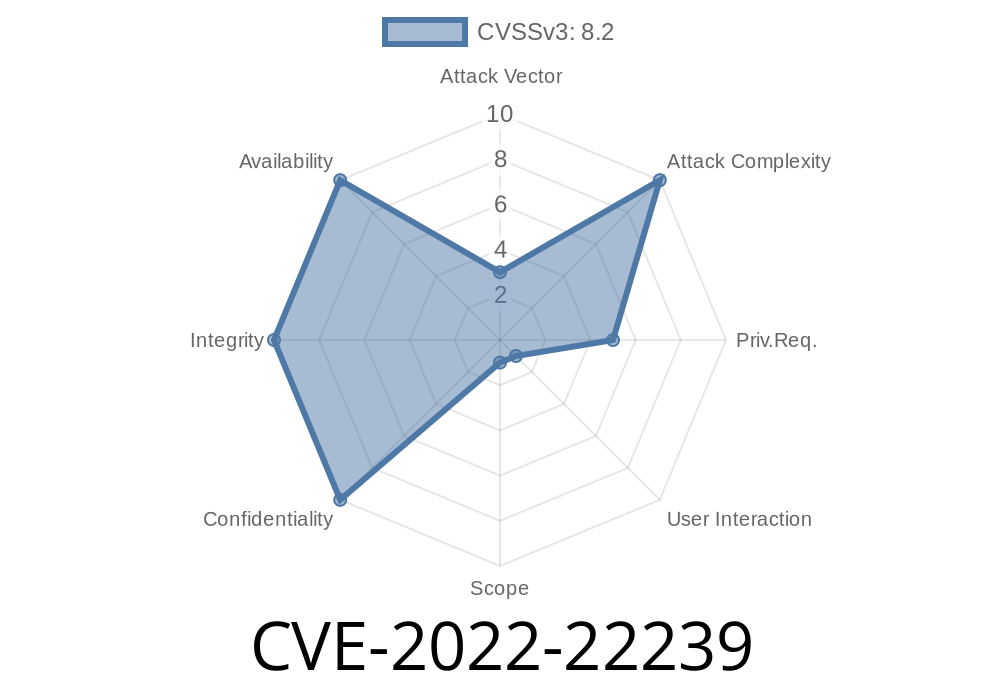
Vulnerability Description - CVE-2022-22239
On some devices, the Management Daemon running on the device provides ssh access to a user with a low privilege level. Due to this, a locally authenticated attacker with low privileges and access to the ssh operational command can escalate their privileges to root. The attacker can do this by ssh’ing to a user with low privilege level, such as bin or sys. This can be done via Telnet, SSH, or through another protocol. An attacker can then use the root privilege to install a malicious SSH server on the device. A malicious SSH server can then be used to bypass security restrictions on the device or to further escalate privileges. If user interaction was required to install the malicious SSH server, then a locally authenticated attacker can potentially escalate their privileges to root, or if there is user interaction on the device to potentially escalate privileges on a remote system to root.
Vulnerability Description:
CVE-2022-22239
On some devices, the Management Daemon running on the device provides ssh access to a user with a low privilege level. Due to this, a locally authenticated attacker with low privileges and access to the ssh operational command can escalate their privileges to root. The attacker can do this by ssh'ing to a user with low privilege level, such as bin or sys. This can be done via Telnet, SSH, or through another protocol. An attacker can then use the root privilege to install a malicious SSH server on the device. A malicious SSH server can then be used
Products Affected By CVE-2022-22239
The following products are potentially affected by CVE-2022-22239:
* ASUS routers (RT-AC66U, RT-N10, RT-N10E, RT-N10P)
* ARRIS cable modems (Spectrum CM4200, U-verse modem 2424C)
* Cisco devices with software versions earlier than IOS 15.5(2).1 and earlier than IOS 12.4(15)T
* D-Link devices (DIR-890L, DI624+, DI636+)
* Huawei devices with software versions 6.0Rx7 and earlier than 6.0RX2
* Linksys devices (E1200, E2500, E3200V2)
* Mikrotik devices running RouterOS version before 6.21
* NETGEAR routers with firmware that is no longer supported by the manufacturer
In order to determine if your device is potentially affected by this vulnerability, you can check its product page on the vendor's website or ask the vendor for a list of affected products.
Identification of the issue
This is a security issue because it provides local attackers with the ability to escalate privileges to root. This allows for local attackers to bypass security restrictions on the device, or potentially escalate privileges on a remote system to root.
Timeline
Published on: 10/18/2022 03:15:00 UTC