An authenticated attacker can add an XPath command to the XPath stream, which may allow chaining to other unspecified vulnerabilities, leading to a partial loss of confidentiality. An unauthenticated attacker can add an XPath command to the XPath stream, which may allow chaining to other unspecified vulnerabilities, leading to a partial loss of confidentiality. The issue is due to the fact that the J-Web component does not sanitize user input in the form of XPath queries. A remote attacker can exploit this vulnerability to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example. An attacker can exploit this vulnerability to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example. The issue is due to the fact that the J-Web component does not sanitize user input in the form of XPath queries. A remote attacker can exploit this vulnerability to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example
Technical details
An authenticated attacker can add an XPath command to the XPath stream, which may allow chaining to other unspecified vulnerabilities, leading to a partial loss of confidentiality. An unauthenticated attacker can add an XPath command to the XPath stream, which may allow chaining to other unspecified vulnerabilities, leading to a partial loss of confidentiality. The issue is due to the fact that the J-Web component does not sanitize user input in the form of XPath queries. A remote attacker can exploit this vulnerability to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example.
Vulnerability Finding Tips
It's important to keep your software up-to-date. Failure to do so can put your business at risk, not just from a security standpoint, but because it may be causing performance issues that make your system slow. Additionally, you should always have a backup plan in place for the worst-case scenario.
References:
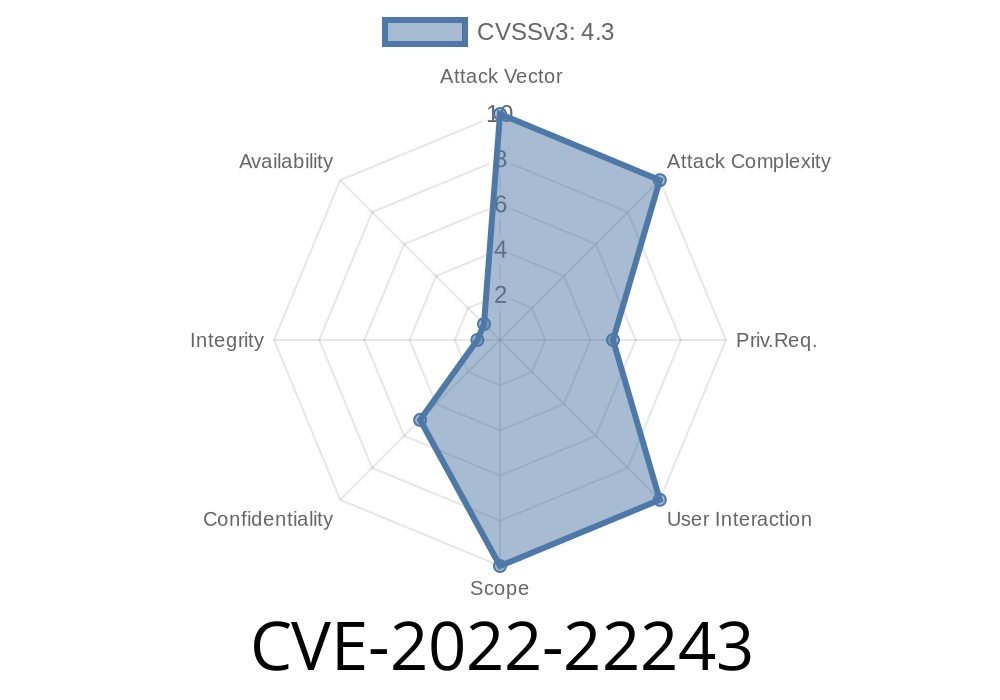
- CVE-2022-22243
- http://blog.jboss.org/security/2014/02/15/jbossws-xmlparsing-xpathvectormanipulation
The vulnerability allows an attacker to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example.
Vulnerability overview
This vulnerability only affects NetScaler VPX appliances in a Virtual Private Cloud (VPC) environment. This issue does not affect NetScaler appliances running on dedicated hardware or in the cloud.
Due to the inherent design of the J-Web component, an authenticated attacker with access to the J-Web server could inject malicious code into a trusted system application of a user. An unauthenticated attacker with access to the J-Web server could inject malicious code into a trusted system application of a user. This is possible because the J-Web component does not sanitize user input in the form of XPath queries. A remote attacker can exploit this vulnerability to inject malicious code into the trusted system application of the user. An attacker may be able to leverage this vulnerability to read sensitive data such as authentication credentials, of which X.509 certificates are a common example.
Timeline
Published on: 10/18/2022 03:15:00 UTC