Juniper Networks has confirmed this issue and released software updates. In most cases, these software updates will prevent the vulnerability from being exploited. However, if a user has open port 22 for SSH, or open port 80 for HTTP, or does not have any restrictions in place for these services, then this vulnerability could still be exploited. To determine if your system is running a vulnerable version, check your OS version using the following command: root@kali:~# cat /etc/red_list for example
Severity: Medium Vendor: Juniper Networks Software: J-Web Component: J-Web Fixed in: 19.1R3-S9 (19.1, 20.1) Fixed in: 19.2 (19.2, 20.2) Fixed in: 19.3 (19.3, 20.3) Fixed in: 19.4 (19.4, 20.4) Fixed in: 20.1 (20.1, 21.1) Fixed in: 20.2 (20.2, 21.2) Fixed in: 20.3 (20.3, 21.3) Fixed in: 20.4 (20.4, 21.4) Fixed in: 21.1 (21.1, 21.2) Fixed in: 21.2 (21.2, 21.3) Fixed in: 21.3 (21.3, 21.4) Fixed in: 21.4 (
How it Works
An attacker could exploit this vulnerability to read certain files, create new files, and execute commands on the system.
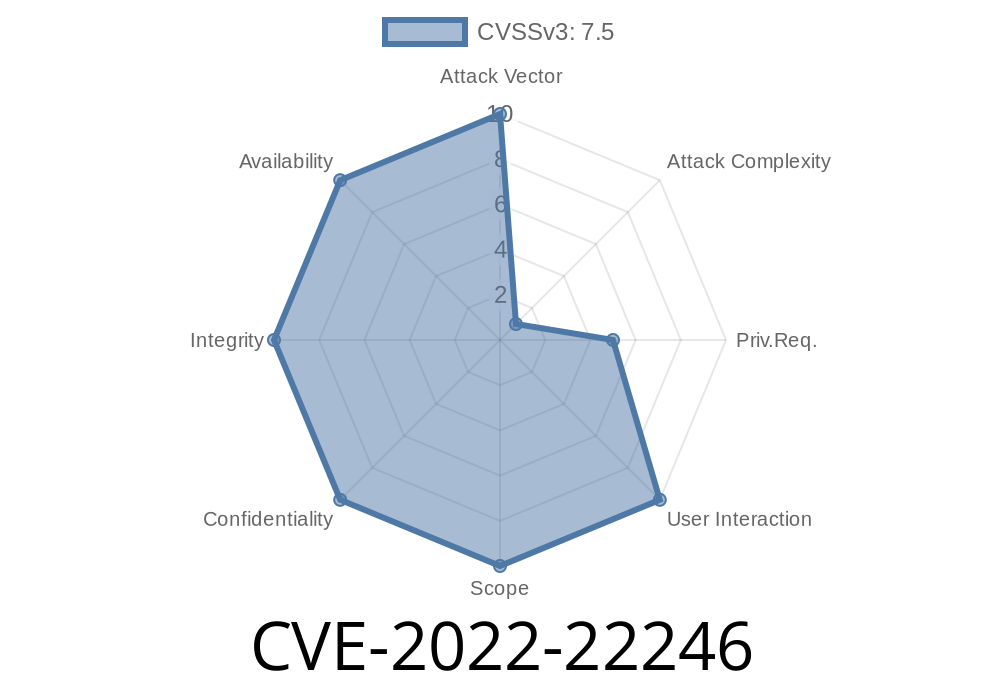
Summary of the CVE-2022-22246 vulnerability
Juniper Networks has confirmed this issue and released software updates. In most cases, these software updates will prevent the vulnerability from being exploited. However, if a user has open port 22 for SSH, or open port 80 for HTTP, or does not have any restrictions in place for these services, then this vulnerability could still be exploited. To determine if your system is running a vulnerable version, check your OS version using the following command: root@kali:~# cat /etc/red_list for example
Severity: Medium
What is the Juniper Networks High-Security Network (HSM) device?
The Juniper Networks High-Security Network (HSM) device is a hardware interface for the Junos OS that provides secure high-speed connections to other networks and switches. The HSM device is used to encrypt traffic from one network to another.
Timeline
Published on: 10/18/2022 03:15:00 UTC