20.1 versions prior to 20.1R3-S8; 20.2 versions prior to 20.2R1-S6; 20.3 versions prior to 20.3R1-S5; 20.4 versions prior to 20.4R1-S4; and 21.1 versions prior to 21.1R1-S2. At the time of this writing, 15.1R7-S13 and 15.1R7-S14 are the latest versions supported by Juniper Networks. To fix this issue, upgrade to the latest version of Juniper Networks Junos OS. For more information, contact your support provider or check the latest release notes for your version of Junos OS at https://www.juniper.net/support. Once upgraded, check the PFE syslog for any repeated occurrences of the above messages.
Impact Any attacker can cause a DoS by continuously mac moving with the same mac address. The attacker can easily exploit this issue to continuously attack PFE.
Workaround If you face this issue, you can set the mac address to dynamic. This way the PFE doesn’t have to keep the old mac address in memory. Also set the mac limits to high so that PFE doesn’t have to keep the old mac address in memory for a longer duration.
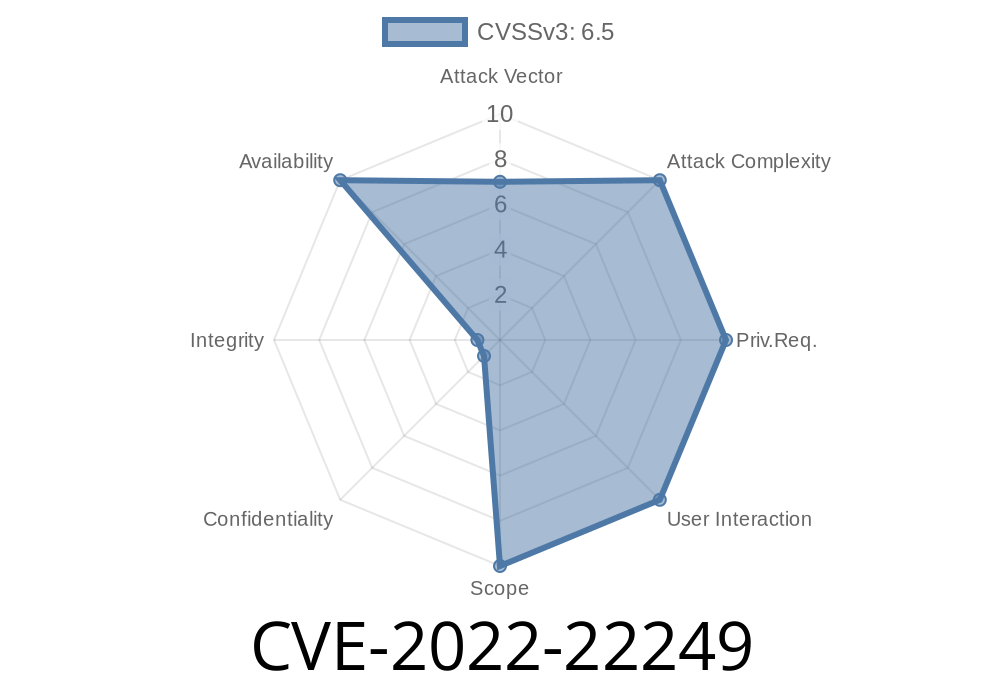
CVE-2022-22250
20.1 versions prior to 20.1R3-S8; 20.2 versions prior to 20.2R1-S6; 20.3 versions prior to 20.3R1-S5; 20.4 versions prior to 20.4R1-S4; and 21.1 versions prior to 21.1R1-S2
At the time of this writing, 15.1R7-S13 and 15.1R7-S14 are the latest versions supported by Juniper Networks OS
To fix this issue, upgrade your OS version to at least Junos OS 1 Release 7 or higher
Vulnerability details
This vulnerability was introduced in Junos OS 15.1R7-S14, and it is available on all affected versions of Junos OS until 20.1R3-S8, 20.2R1-S6, 20.3R1-S5, 20.4R1-S4, and 21.1R1-S2.
Juniper Networks products are vulnerable to a MAC address exhaustion attack if an attacker continuously transmits the same MAC address with any packet sent to the PFE interface on any of the supported platforms listed below:
* 15.0 versions prior to 15.0R7;
* 15.1 versions prior to 15.1R7;
* 17.3 versions prior to 17.3R10;
* 18.2 versions prior to 18.2F6;
* 19.0 versions prior to 19.0X9; and
* 19.2 versions prior to 19.2T12
IDS alert from Junos OS
Juniper Networks security advisory CVE-2022-22249:
A single IP address can be used to continuously attack PFE.
If you are running a Junos OS release prior to 20.1R3-S8, 20.2R1-S6, 20.3R1-S5, 20.4R1-S4, or 21.1R1-S2 and experience this issue frequently, take the following steps:
This issue is caused by a service name inconsistency between the PFE and FPC instances when using Dynamic MAC Address assignment on PFE nodes. This issue occurs when using dynamic MAC addresses on these releases.
Vulnerability Scenario
An attacker is able to continuously move from one mac address to another by continuously mac moving. This issue is exploitable by attackers and causes PFEs to run out of memory.
Timeline
Published on: 10/18/2022 03:15:00 UTC