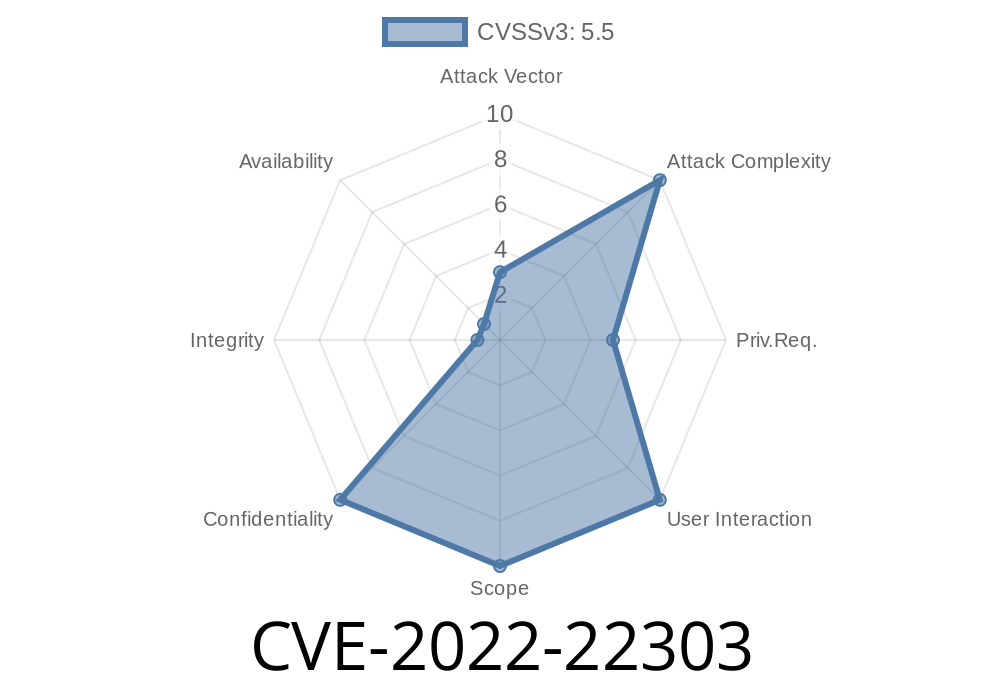
Security is all about layers. When one layer cracks, the consequences can ripple across your whole network. In this post, we will break down CVE-2022-22303, a vulnerability (CWE-497: Exposure of Sensitive System Information to an Unauthorized Control Sphere) discovered in FortiManager—a vital tool for many organizations that use FortiGate firewalls. Even if you’re not a security pro, this article will show you just how easy it was for a low-level user to cleverly harvest administrator credentials, step by step.
Versions prior to 6.2.9
This vulnerability allows a user with very basic (low privileged) access to FortiManager to gain far more than their job description allows—specifically, the credentials of any FortiGate firewall users managed through that FortiManager.
How? By taking advantage of a file meant for troubleshooting—a configuration conflict file. Normally, this file is supposed to help administrators resolve discrepancies between devices and policies. But due to a flaw, it exposed way too much.
How Does The Exploit Work?
Let’s walk through the steps, as simply as possible, to highlight just how easy things could go wrong for an organization using a faulty FortiManager.
1. Gaining Authenticated Access
First, you need a basic (low privileged) login on FortiManager. Think of an intern or a contractor role—not an admin.
2. Triggering a Config Conflict
You request a policy or configuration change that causes a conflict between what’s on the FortiGate device and FortiManager’s database. This is easy: make a tiny change and try to push it, or deliberately mismatch settings.
3. Reading the Config Conflict File
FortiManager will create a conflict file for administrators to review. But, due to the vulnerability, this file is often world-readable for anyone with access—including your basic user account.
Inside this file, FortiManager often stores literal copies of the full FortiGate configuration—including sensitive fields like usernames and password hashes (and sometimes even passwords, based on your version and configuration).
Exploit Example
Let’s get a bit more technical (but still easy to follow). Here’s how an attacker could actually pull this off.
Regular, non-admin credentials can be used.
ssh normaluser@fortimanager.internal
Step 2: Initiate a Configuration Conflict
Try to modify a policy or conflicting configuration (the details depend on your role and permissions).
The conflict file usually ends up in a directory like
/var/CMDB/xxx.conflict
Find it with
ls -lh /var/CMDB | grep conflict
Use cat to reveal secrets
cat /var/CMDB/fg1-2022-01-18.conflict
In the output, look for lines like
config user local
edit "admin"
set password ENC xxxxxxxxxxxxxxx
set email "admin@company.com"
next
end
Or even
set password "RealPasswordHere"
Which gives away everything needed to impersonate, escalate privileges, or attack other FortiGate devices.
Why Did This Happen?
- Insecure Permissions: The system didn’t restrict who could read conflict files. Anyone with ANY login could see them.
- Overexposed Information: The conflict file contained too much sensitive data that should’ve been masked or never exported as plain text.
How Real Is The Risk?
Very real. This isn’t a “theoretical” bug. If you’re an attacker with modest access, you could:
If you’re running an older version, Update Now!
- Fortinet PSIRT Advisory
- CVE-2022-22303 at NIST
- CWE-497 details
Summary
CVE-2022-22303 shows that even basic information leaks can punch massive holes in enterprise security. If you manage FortiManager, make sure you’re on the patched version—and remember, “least privilege” is more than a mantra. It’s your best defense.
If your organization hasn’t updated yet, now’s the time.
---
Timeline
Published on: 03/02/2022 10:15:00 UTC
Last modified on: 03/10/2022 15:21:00 UTC